Tag: SQL injections
Cyber Attacks Explained: Web Exploitation
Websites are no longer merely about having an "Internet presence" today, but are also used for commercial transactions and to transfer sensitive data. Such...
IT Service Provider Turns to PostgreSQL for Scalability
A S Kumaresan, an Enterprise DB contest winner, tells LINUX For You why PostgreSQL was an obvious choice for an ICT provider.
When a client...
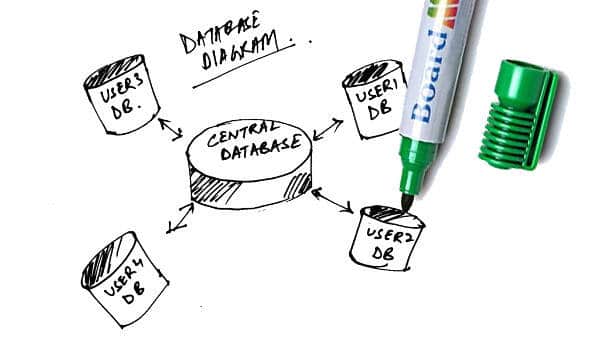
Securing Database Servers
With the ever-expanding data requirements for Web applications, database administrators often configure security parameters at the OS and database layer. Unfortunately, administrators seldom consider...
Up Close and Personal with NoSQL
Aimed at Web developers, DBAs, programmers, et al., this article covers the basic concepts about NoSQL databases, the different types and their features.
When you...
Securing Apache, Part 1: The Basics
Targeted at readers with Web security concerns, information security experts, systems administrators and all those who want to jump-start their careers in Web security,...