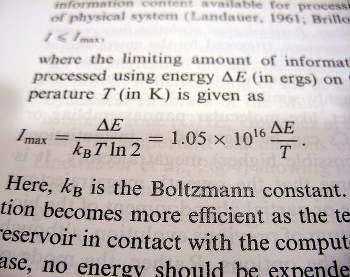Tag: unix
OpenIndiana — a Free Fork of Solaris
OpenIndiana comprises the Illumos core, taken from OpenSolaris, with a set of GNU user-land tools. OpenIndiana can even be called an analogue to GNU/Linux,...
Amanda: A One-Stop Solution for All Your Backup Problems
Looking for an enterprise backup solution for your servers? Is your network too complex to be handled by simple backup utilities? Does the thought...
Joy of Programming: The Technology Behind Static Analysis Tools
There are a wide range of static analysers available today -- both commercial as well as open source. Have you ever wondered how static...
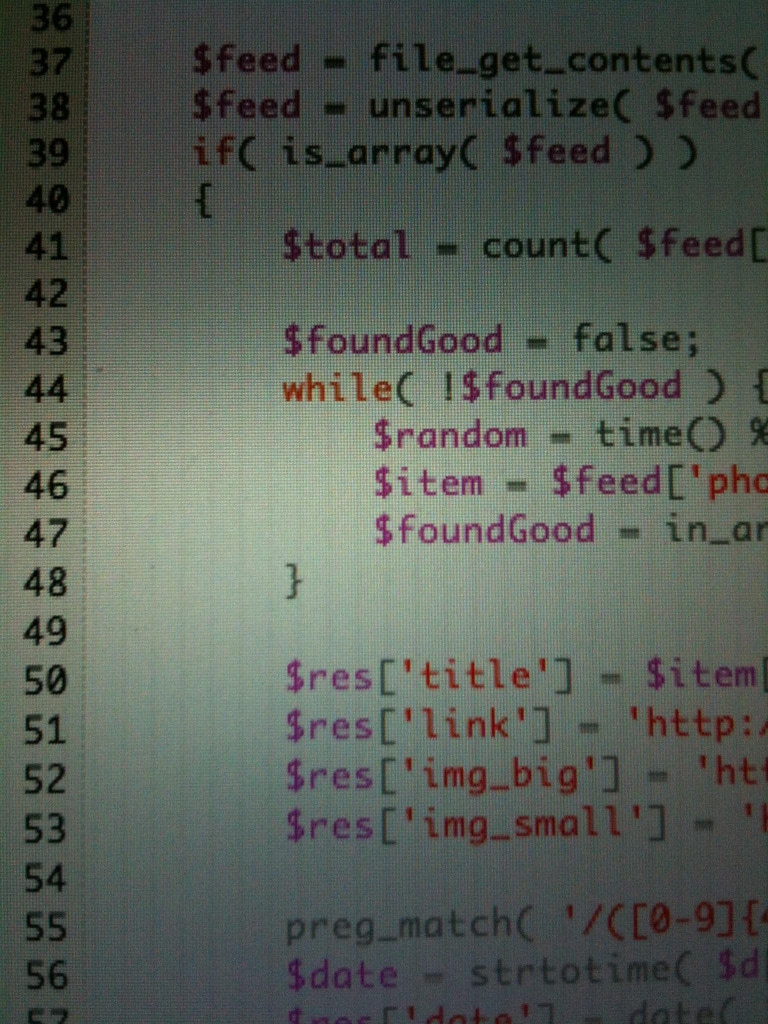
Light-Weight Processes: Dissecting Linux Threads
This article, aimed at Linux developers and students of computer science, explores the fundamentals of threads and their implementation in Linux with Light-Weight Processes,...
Unix-to-Linux Migration Has Come of Age
If you've often wondered whether you ought to migrate your Unix system to Linux, this article will answer your question!
The driving force behind every...
Joy of Programming: How Debugging Can Result in Bugs!
We typically debug code to find and fix bugs. However, debugging itself can cause bugs. This is an interesting phenomenon that we cover in...
Sed Explained, Part 2: Data Structures and Operators
Continuing from the previous article on the subject, we now proceed to Sed data structures and operators.
Sed has a few powerful data structures and...
Graphics Using Xlib, Part 1
This article introduces you to the X Window System, with the aim of helping developers understand how to use the Xlib library effectively.
The X...
What is Scientific Programming?
This article will take you into the world of scientific programming -- from simple numerical computations to some complex mathematical models and simulations. We...
Sed Explained, Part 1
UNIX-like operating systems have numerous powerful utilities accessible via the command-line and shell-scripting, which are flexible enough to operate in a variety of problematic...