
Penetration testing, affectionately called pen-testing, involves testing a piece of software, or network and security systems, for resilience against attacks from crackers (or black hat hackers — the bad guys). Nothing is perfect; we all know that. Every application, website or network has vulnerabilities. Pen-testing allows us to detect those holes so that we can fix them and prevent exploits. It’s a very geeky domain, so I will keep things simple here.
Penetration testing is conceptually divided into:
- Black-box testing: As the name implies, the internals are not taken into consideration for this type of testing. How the software actually works (or the network functions) is not relevant here. The functionality of the software or network is considered, and then the testing is carried out.
- White-box testing: The opposite of black-box testing, this involves the internal workings of the system; the workings of the software or network are probed and tested for holes.
Web application pen-testing
Since the domain of penetration testing is a broad one, this article will focus on pen-testing Web applications. To aid understanding, we will be doing some hands-on work with a neat framework called Samurai. There are many methodologies for testing Web applications. There is a comprehensive one by OWASP (the Open Web Application Security Project). This lists a methodology with nine sub-categories: configuration management testing, business logic testing, authentication testing, session management testing, authorisation testing, data validation testing, denial of service testing, Web services testing and AJAX testing. To keep things simple, I will explain a widely used 4-stage methodology (used by Samurai too) for testing Web applications.
Stage 1: Reconnaissance
The first stage in pen-testing a Web application is to find what information about the application is already available out there. What servers does it run on? What backend technology does it use? What environment does it run in, apart from details like its infrastructure, its hosts, machines, operating systems, network details, etc? Basically, this is an information-gathering stage. Getting to know our target is what is going on at this stage.
Stage 2: Mapping
What are the bits and pieces that make up the application? What makes it tick? What are the relationships between the various components of the application? At this stage, you map these, and understand the workings of the Web application. You begin to understand how the system works, as a whole. This is highly useful to identify possible vulnerabilities, loopholes and exploits.
Stage 3: Discovery
This is where you discover the vulnerabilities. There are two types of discoveries: client-side and server-side. Client-side discoveries include breaking open (or decompiling) Flash, Java and the AJAX components of the Web application on the client end. Server-side discoveries are vulnerabilities like SQL injection, session exploits, information leaks, username harvesting, command injections, etc
Stage 4: Exploitation
This is the fun part. Based on the previous stages, you actually exploit the Web application to test its resilience. At this point, you begin to understand the actual working and impact of the loopholes.
The four stages are iterative in nature, and can go on continuously for a Web application — yielding priceless data to help you understand the weaknesses of the system. The ultimate goal of this is, of course, to plug these holes, and make the system more secure from real attackers. Compare this to running a fire drill in your building, or simulating a bank robbery to ensure that the bank’s security is robust.
Enter Samurai WTF
Okay, I know the acronym WTF has a tendency to invoke the giggles, but it stands for Web-Testing Framework, and not what you thought initially. Samurai is a live Linux distribution packed to the brim with the best open source pen-testing tools for all the four stages listed above. What’s more, it has a preconfigured wiki that acts as a central store of information during testing.
Getting started
Like any other live distro, download the ISO from the website and burn it to a disc, or use a virtualisation tool like VirtualBox to test it. Once the disc boots, you will be greeted with a boot prompt that looks like many other Live CDs. Just type live at the boot: prompt to start the booting process. After the boot-up is complete, you will be greeted by the login screen (Figure 1). The username and password are ‘samurai’; use these to log in and get to the desktop (Figure 2).

As mentioned earlier, Samurai comes with a bundle of pen-testing tools (see Figures 3, 4 and 5). In the following sections, I will demonstrate the four stages of Web application pen-testing, using one tool from each category. As you will notice, Samurai has clubbed Reconnaissance and Mapping into one application category. Lets begin with those two stages.


Introducing DVWA
Let’s use a testbed to understand the four stages in their entirety. Samurai bundles a neat Web application that runs on PHP/MySQL, called DVWADamn Vulnerable Web App (Figure 6). This is a Web application which is, well, damn vulnerable. It’s got a lot of loopholes, and is meant to help you understand pen-testing; so let’s use this to understand the concepts of pen-testing. You can access DVWA by opening Firefox in Samurai, and navigating to http://dvwa/. Alternatively, you can access it via the Samurai local home page (http://localhost/)

Reconnaissance and mapping
For reconnaissance and mapping, use the ever-powerful Maltego (Community Edition), for example, if you want to see all the “To Websites” entries for the domain http://dvwa/ (which is our DVWA address). First, start Maltego (see Figure 7) and drag the “Website” node onto the graph.

Click the node, and edit the Value property in the Properties editor on the right; set it to http://dvwa/. Now right-click the node, and select Incoming Links –> All In This Set. This will draw up a map of the incoming links to your Web applications (Figure 8). Similarly, you can recon and map various entities available in the Maltego toolbox.

Discovery
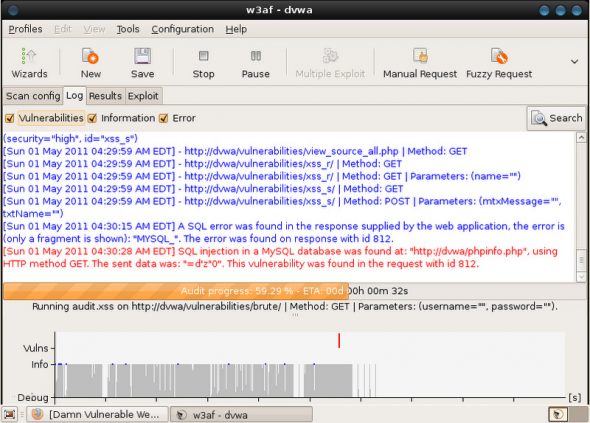
W3af, the Web Application Attack and Audit Framework, is a very powerful utility for running a discovery on a URL. It’s intuitive and fast. Start the w3af GUI from Applications –> Samurai –> Discovery –> w3af GUI. In the URL field, enter http://dvwa/. Generally, you select the plugins that you want to use to test; for now, just select fast_scan to run a quick scan, and click the Start button on the top toolbar (see Figure 9).

The scan begins to run, and soon you will get an SQL injection vulnerability picked up, as seen in Figure 10. You can now use this for exploitation, in the next stage.
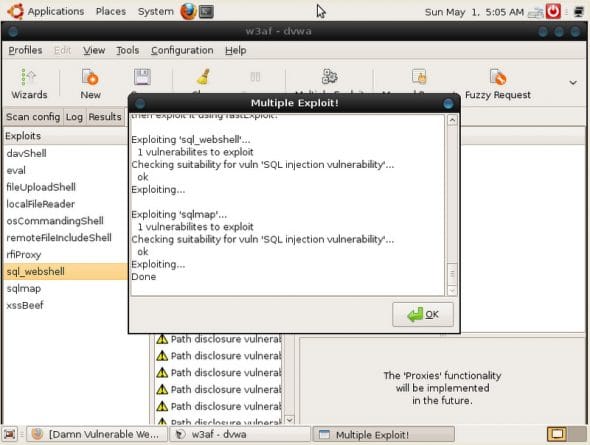
Exploitation
Let’s exploit the SQL injection vulnerability we picked up. Go over to the Results tab in w3af, and look for the red sqli (indicating the SQL injection vulnerability). We now need to see if it can be exploited. Expand the sqli tree; observe the cogs, which indicate that the vulnerability can be tested for exploits. Click the cogs to make w3af run multiple exploits. w3af now tries to exploit this discovery, and succeeds — see Figure 11.
Samurai WTF has a whole lot more to offer than the tools I have described here. Spend some time with it, and those of you who love to dabble a bit in hacking will find this suite of penetration tools really exciting, I’m sure. Pen-testing is a very happening domain, where the testers are always at the cutting-edge of technology, with a deep knowledge of the domain they are testing. So go, get geeky!




https://www.facebook.com/Boycottcpanel This is important to you whether you know what it is or not. You data is not safe currently, if you shop online at places that use this, even if you don’t shop online you might have multiple accounts with the same passwords. This is really important please read it.
Siddharth Mankad :)
[…] voici un lien pour plus de détails : https://www.opensourceforu.com/2011/06/web-app-penetration-testing-with-samurai/ […]