In this first part of a series on IoT constrained node networks, we get introduced to the IoT, its building blocks, constrained node networks, their characteristics, the protocols used and the recommended firmware.
The Internet of Things (IoT) transforms our lives through smart automation and has become an integral part of many activities. IoT is spreading to various domains such as industry, agriculture, medicine, smart cities, etc. The main elements that have enabled widespread IoT adoption are the rapid advances in software, networking, sensors and artificial intelligence (AI). IoT involves giving networking capabilities to things, which can be physical or virtual. Physical things include humans, wearables, vehicles, homes, computers, embedded devices, etc. Virtual things include virtual machines, virtual networks, social media sites, etc. All these things being connected through the Internet is what IoT is all about.
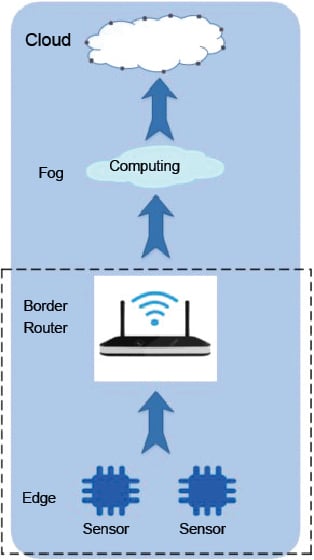
The building blocks of an IoT system
An end-to-end IoT system can be classified into three networks — the edge network, the fog network and the cloud network. This classification is based on the type of devices and the applications running in those networks.
A. Edge network
- Devices: These include embedded devices, sensors, actuators and gateways. The devices may be constrained (with limited resources) or unconstrained.
- Applications: These include sensing, monitoring, actuating and conducting operations with the external world.
B. Fog network
- Devices: These are gateways and high-end servers.
- Applications: These include the roles of the broker, data acquisition and processing, commanding, real-time analytics, databases, etc.
C. Cloud network
- Devices: These are cloud platforms and high-end servers.
- Applications: These include storage, machine learning and deep learning.
The edge system consists of constrained or unconstrained devices, or both. This article discusses only constrained devices.
Devices with limited resources like memory, processing capacity and power are called constrained nodes.
There are three classes of constrained nodes, as shown in Table 1.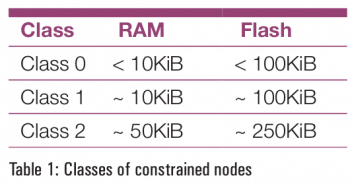 The support for the network stack and the security for these constrained nodes is shown in Table 2.
The support for the network stack and the security for these constrained nodes is shown in Table 2.
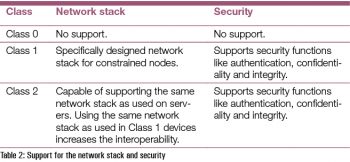 Constrained networks
Constrained networks
A constrained network exhibits the following characteristics:
- Low bit-rate/throughput
- High packet loss and high variability of packet loss
- Highly asymmetric link characteristics
- Lack of advanced network services like multi-cast
The possible reasons for these characteristics of constrained networks are listed below:
- Cost constraints
- Constraints posed by the nodes
- Physical constraints, e.g., power or environmental constraints
- Technology constraints such as having to use legacy technologies
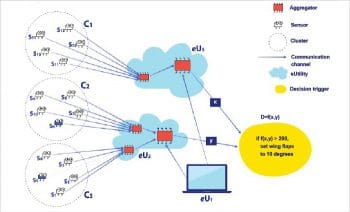
Constrained node networks
A constrained network is composed of a significant number of constrained nodes. These constrained node networks are deployed generally in the edge network of an IoT system.
The building blocks of a constrained node network are listed below.
- Sensors: Sensors are electronic devices, modules or sub-systems that measure physical properties and give an electrical output, e.g., temperature or acceleration sensors.
- Actuators: These are devices that take an electronic input and give a physical output, e.g., motors.
- Clusters: This is a grouping of sensors and actuators.
- Communication channels: This is a medium through which data is transferred, e.g., wired or wireless.
- Aggregators: These are the devices used to aggregate all the data from sensors and sometimes give commands to actuators. They are gateway devices.
- eUtility: This may be software, hardware or services that support aggregators in feeding data and in computing.
- Decision trigger: This is the software that does the computing and takes action if needed.
Special network stacks and constrained node networks
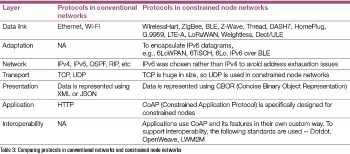
Constrained networks cannot use conventional TCP/IP stacks and need a new network stack because of their resource constrained nature. Refer Table 3 which compares protocols in conventional networks and constrained node networks.
 Constrained node: Firmware comparison
Constrained node: Firmware comparison
The firmware for IoT devices need to meet the following requirements — energy efficiency, real-time capabilities, network connectivity, security, safety and a small footprint.
The firmware design relies heavily on which type of data link layer protocol is used in a constrained node. Table 4 gives a comparison between some of the commonly used link layer technologies.
The key points that make the Thread protocol the preferred technology are listed below:
- Thread is an open source implementation of an open specification.
- Thread has inherent IP support. Zigbee has recently got IP support as an enhancement.
- Thread and Zigbee support Dotdot, which is an application layer protocol for interoperability. The number of Zigbee devices in the world is significant. Since Thread supports Dotdot, it can also communicate with Zigbee devices in a seamless way.
- Thread has been supported by Google, ARM, Nordic, Cascoda, NXP, Particle, Qorvo, Qualcomm, Samsung, Silicon Labs, STMicroelectronics, Synopsys, TI, Zephyr and Apple since 2018. This raises the hope that the Thread protocol will become the de facto technology for constrained nodes.
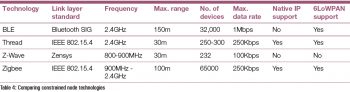 The first part in this series gives an introduction to IoT, constrained node networks, and how these networks are used in an IoT system. The firmware requirements and the network protocols meant for constrained nodes have also been explored. The firmware comparison in Table 4 clearly shows that the
The first part in this series gives an introduction to IoT, constrained node networks, and how these networks are used in an IoT system. The firmware requirements and the network protocols meant for constrained nodes have also been explored. The firmware comparison in Table 4 clearly shows that the
Thread protocol has an edge over other technologies and is the recommended firmware for constrained nodes in IoT.



