Qubes OS is a compartmentalised operating system with high security and isolated virtual machines (VMs). It takes the approach of compartmentalisation to deliver security. The OS is open source and freely available at https://www.qubes-os.org. Installation is a very easy process, involving just a few clicks.
OS level security
Popular operating systems like Windows or OS X suffer from security issues due to their pre-installed dependencies. For example, opening an innocent portable executable (PE) downloaded from the Internet without knowing about the actual functionality of the particular PE, allows malware to execute on your computer. Once the malware is executed, the entire OS is compromised. Traditional security systems like antivirus software and firewalls are not capable of detecting present day attacks/intrusions. The Qubes OS provides security services at the operating system level; hence, it is called a security-oriented OS (Figure 1).
Qubes allows users to define their own security domains, which are implemented as lightweight VMs or AppVMs. A person can have personal, work-related, shopping, banking and random AppVMs and can use the applications within those VMs. However, these applications are well isolated from each other. Qubes also supports secure copy-and-paste and file sharing between the AppVMs. The OS executes all the applications in isolated VMs in order to achieve security without being compromised. For example, a user can download any type of file from the Internet and can execute it in one compartment, and the same user can do bank transactions securely in another compartment. Qubes supports inter-VM secure file transfer.
Virtualisation in Qubes OS
Qubes OS adopts an approach called software compartmentalisation, where Type1 virtualisation is achieved by executing the isolated VMs directly on the hardware using the XEN hypervisor (a bare metal hypervisor). This is very different from conventional VMs like Vbox or VMware (hosted hypervisors), and an attacker must be capable of disrupting the hypervisor in order to compromise the entire system, which is immensely difficult.

Dom0
Dom0, an active desktop manager, handles the entire login sessions and is more trusted than other domains. It is the heart of the entire security management. Dom0 is used for running window managers. Due to its overarching importance, connectivity to Dom0 is restricted and the user is never allowed to run an application in this interface.
To open a window in Dom0, go to Start → SystemTools → Konsole
To view various command line tools, please execute the following command:
Qvm ls
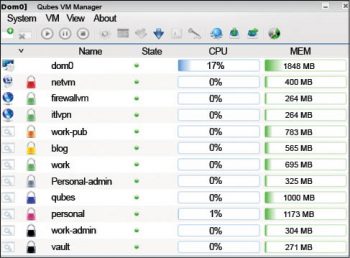
For managing AppVMs and TemplateVMs, a GUI based Qubes Virtual Manager is used (Figure 2).
Start →SystemTools →Qubes manager
To start any application from the console, use the following command:
Syntax: Qvm-run a <domain> <app name> [arguments]
An example is: qvm-run a work python sibi.py
Syntax to add domains is: qvm-create
Syntax to remove domains is: qvm-remove
The qrexec framework is used by core Qubes components to implement communication between domains. Qubes domains are isolated by design, but there is a need for a mechanism to allow the administrative domain (dom0) to force command execution in another domain (VM).
Some available services of the Qubes OS are:
- Inter-domain file copying
- Dynamic memory management in Qubes
- Disposable VMs
- Dom0 secure update mechanism
Inter-domain file copying
Remote procedure calls (qrexec and Qubes RPC) are used for inter-domain file copying. There are two cases when we need a mechanism to copy files between VMs:
- Regular file copy, when a user instructs a file manager to copy some given files/directories to a different VM.
- DispVM copy, when a user selects Open in DispVM on a file; this file must be copied to a disposable VM, edited by the user and, possibly, a modified file must be copied back from DispVM to the VM.
Dynamic memory management in Qubes
Qmemman (the Qubes memory manager) is used for memory management. Qmemman checks for the do-not-membalance file before allocating memory for the new domain. If it finds the file, it suspends memory balancing. The command to free the specified amount of memory is:
/var/run/qubes/qmemman.sock
Xenstore is used for VM memory management. Traditionally, Xen VMs are assigned a fixed amount of memory. It is not the optimal solution, as some VMs may require more memory than that assigned initially, while others under-utilise memory. Thus, there is a need for a solution capable of shifting free memory from one VM to another.
Tmem provides a pseudo-RAM that is assigned on an as per-need basis. Basically, Tmem is integrated with the Linux kernel and provides an interface to copy memory to/from fast (RAM based storage).
Disposable VMs
In general, disposable VMs are lightweight; they are created and booted in a short period of time (less than one second) with the sole purpose of hosting only one application. .
The Dom0 secure update mechanism
In general, Dom0 executes a secured qvm-dom0-update script under updateVM, where RPM files are checked, verified and downloaded. Once all the updates are downloaded, the update script requests for RPM service qubes.ReceiveUpdates to be executed in Dom0. This service is implemented by the qubes-receive-updates script running in Dom0. The Dom0s qvm-dom0-update script waits until qubes-receive-updates has finished. The qubes-receive-updates script processes the untrusted input from Update VM; it first extracts the received *.rpm files (that are sent over the qrexec data connection) and then verifies the digital signature on each file in order to avoid processing compromised updates. The qubes-receive-updates script is a security-critical component of the Dom0 update process.
References
[1] https://www.qubes-os.org
[2] https://www.qubes-os.org/doc/qubes-architecture/
[3] https://www.qubes-os.org/getting-started/










































































