Here’s a quick tutorial on how to build a secure, real world client-server model that establishes client identity by using CRYSTALS-Dilithium, a post-quantum cryptography algorithm.
Encryption relies on mathematics to safeguard sensitive electronic information, such as websites and emails. Public-key encryption systems, which are widely used today, depend on mathematical problems that are computationally intractable, ensuring that websites and messages remain inaccessible to unauthorised third parties.
When developing new standards, NIST (National Institute of Standards and Technology) in the US evaluates not only the security of the algorithms’ underlying the mathematics but also their most effective applications. The latest standards are designed to address two essential cryptographic tasks:
- General encryption – protecting information exchanged across public networks.
- Digital signatures – providing identity authentication.
In 2022, NIST announced the selection of four algorithms for standardisation: CRYSTALS-Kyber, CRYSTALS-Dilithium, SPHINCS+, and FALCON. Draft standards for three of these were released in 2023, while the fourth — based on FALCON — was released in late 2024.
This article focuses on building a secure, real world client-server model that establishes client identity using CRYSTALS-Dilithium, a post-quantum cryptography (PQC) algorithm finalised by NIST as the primary standard for digital signatures. The algorithm has been standardised as ML-DSA (Module Lattice-Based Digital Signature Algorithm).
Traditional software that relies on RSA or ECC is now being replaced by PQC standards like Dilithium. This standard has numerous advantages.
- Quantum resistance: Unlike RSA and ECC, which are vulnerable to quantum attacks, Dilithium resists all known quantum algorithms. Developers adopting CRYSTALS-Dilithium can ensure long-term system integrity and non-repudiation.
- Compact and secure signatures: To reduce signature size while maintaining deterministic behaviour, Dilithium employs a rejection sampling technique. Only signatures within specific bounds are accepted, ensuring both security and efficiency.
- Efficiency in constrained environments: Despite being lattice-based, Dilithium is computationally efficient. On microcontrollers such as the ARM Cortex-M4, it can sign messages in under 6 million cycles while using less than 8KB of RAM.
Several cryptographic libraries already support Dilithium, including BoringSSL, OpenSSL, WolfSSL, Libgcrypt, and IBM’s PKCS#11. For our implementation, we make use of liboqs, a free and open source C library from the Open Quantum Safe (OQS) project, available on GitHub. This library provides a broad range of quantum-safe cryptographic algorithms, making it well-suited for both experimental and production environments.
The liboqs library offers three major capabilities:
- A collection of open source implementations of quantum-safe key encapsulation mechanisms (KEMs) and digital signature algorithms (see its supported algorithms list).
- A common API for all supported algorithms.
- A test harness and benchmarking routines for evaluation and performance measurement.
For communication between the client and server, we use Python with socket programming. The connection is established through an assigned port (e.g., 65432) and a host IP address (e.g., 127.0.0.1 for localhost, though any valid IP can be used).
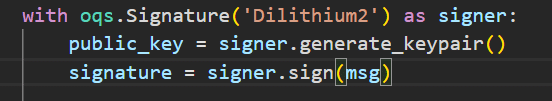
The client generates a public key using the Dilithium library and signs the message with its private key, as shown in Figure 1.
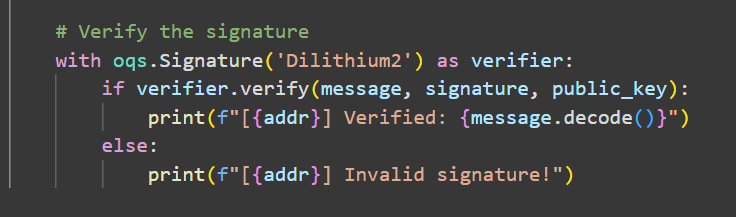
The client then transmits its public key and the signed message to the server through the same socket connection. On the server side, the socket is bound to the specified address and port to receive the client’s signed message. Using the OQS library, the server verifies the integrity and authenticity of the communication by validating the signature with the client’s public key and comparing it with the original message. The server-side code is shown in Figure 2.
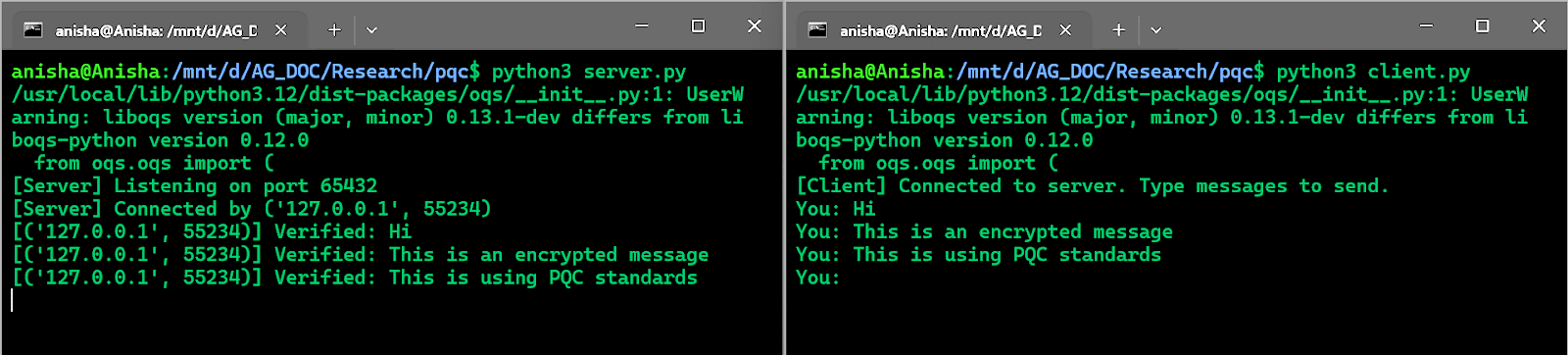
After successful verification, the command and output shown in Figure 3 demonstrates the client-server communication flow. It is important to encode messages into bytes—either using the pickle library or through packet encapsulation—to ensure seamless data exchange over the socket interface.
One of the key advantages of CRYSTALS-Dilithium is its strong balance between performance and cryptographic strength. It is both efficient and compact when compared to other post-quantum digital signature algorithms.
In our implementation, we utilise Dilithium2 (128-bit security level), which features the following parameter sizes:
- Signature size: ~2.4KB
- Public key size: ~1.3KB
- Private key size: ~2.5KB
When compared to SPHINCS+, another post-quantum signature scheme, Dilithium provides much faster signing and verification speeds while also producing significantly smaller signatures. Although traditional ECDSA signatures are shorter (typically 64-72 bytes), they lack quantum resistance, rendering them unsuitable for the post-quantum era.