Home 2011
Yearly Archives: 2011
Digital Magazine Store Magzter Uses Open Source to Slash Costs
A mobile digital magazine newsstand goes the open source way to cut its initial investments, and allow publishers to share digital editions of their...
Aakash: A Historical Mistake?
India created history (of sorts) recently by launching the world's cheapest tablet, Aakash. It almost looked like we'd conquered the world... till the reality...
GDB: Logging Function Parameters, Part 1
Sometimes an application's release version crashes in particular scenarios, but the debug version does not -- and to make matters worse, the call-trace gets...
Lisp: Tears of Joy, Part 6
Lisp has been hailed as the world's most powerful programming language -- but only the top percentile of programmers use it, because of its...
Device Drivers, Part 12: USB Drivers in Linux Continued
The 12th part of the series on Linux device drivers takes you further along the path to writing your first USB driver in Linux...
Agile Software Development Made Faster, More Secure
While the value proposition that open source offers to agile software development teams is tremendous, the enterprises adopting these tools may still inadvertently get...
nexenta: Bringing Enterprise Storage to the Open Source World
This article discusses some of the challenges and technologies related to data storage, and introduces the Nexenta Core Platform, which is an OS based...
Storage Management using Openfiler, Part 4
In the previous article in the series on Openfiler, we discussed configuring RAID. Here, we will proceed with the installation and configuration of iSCSI....
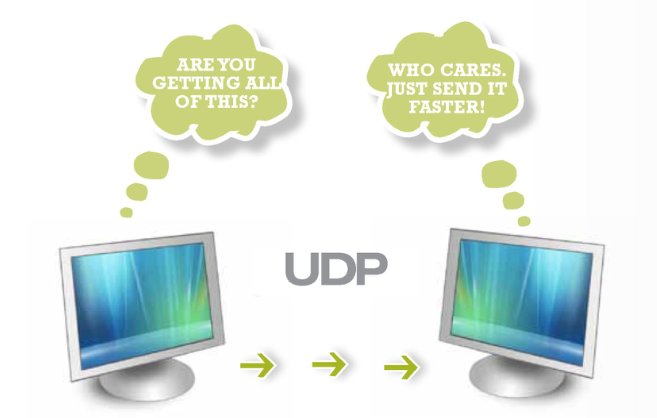
The Socket API, Part 4: Datagrams
Let's try to develop server clients using UDP, the protocol behind some important services like DNS, NFS, etc.
UDP, the User Datagram Protocol, is a...
Cyber Attacks Explained: DoS and DDoS
With this article, we begin a new series on the major kinds of cyber attacks that weaken the IT security infrastructure within organisations. With...