FreeIPA is an integrated security information management solution built using various open source technologies like 389 Directory Server, MIT Kerberos, NTP, DNS and the Dogtag Certificate System.
FreeIPA provides users and administrators a one-stop solution for integrated identity and authentication solutions in the Linux environment. Using FreeIPA server, systems administrators can manage authentication, authorisation and account information at a centralised place.
It provides both CLI and Web UI for management and administration.
The components of FreeIPA are:
1. 389 Directory Services: LDAP directory infrastructure
2. MIT Kerberos: For single-sign-on authentication
3. Dogtag: A certificate authority
4. Bind: A DNS service
5. SSSD: A client side component that integrates with FreeIPA for authentication
FreeIPA is a reliable solution as it is built on top of very well-known open source components and standard protocols. It is easy to install, manage and configure FreeIPA server and clients.
Getting started with FreeIPA
Installing the OS: Sysadmins can use Fedora or CentOS virtual machines for configuring and trying out FreeIPA in a given environment. They can use public demo servers to get a quick idea about FreeIPA server, which can be found at http://www.freeipa.org/page/Demo
Setting up a static hostname: Kerberos authentication relies on a static hostname; so in order to satisfy this requirement, the host should either have a fully qualified domain name from the DNS server or a static hostname in the /etc/hosts file.
$ echo 10.10.10.1 ipaserver1.example.com ipaserver1 >> /etc/hosts
Here, we are using ipaserver1.example.com as the static hostname and assign 10.10.10.1 as the IP address to it in the /etc/hosts file, in order to get the static hostname resolved.
Installing FreeIPA server: We will use the standard FreeIPA server packages provided by the OS such as Fedora or CentOS. You can always choose to install from the upstream source hosted on https://git.fedorahosted.org/cgit/freeipa.git
Install the FreeIPA server by issuing the following command when using Fedora 21/CentOS 6:
# yum install freeipa-server
The installation log for freeipa-server is located at /var/log/ipaserver-install.log
Configuring the FreeIPA server: After installation, you need to configure the FreeIPA server, which can be done using the following command:
# ipa-server-install
ipa-server-install is an interactive script which will ask the administrator a few basic questions like the directory server password, DNS forwarder name, etc. This command will gather all the required information from the administrator and configure all the required services.
The user can check other configurable parameters of the ipa-server-install command by using the man ipa-server-install command.
Here is a quick, non-interactive command for installing the FreeIPA server:
# ipa-server-install --ip-address 10.10.10.1 -r example.com -p Password -a Password --setup-dns --forwarder 10.10.10.254 -U
For more information about various parameters, see man ipa-server-install or ipa-server-install – – help
Check the installation by using the following command:
# ipa --version
If admins want to uninstall FreeIPA server, they can use the following command:
# ipa-server-install --uninstall
The user can also specify the -U option for non-interactive uninstallation of the FreeIPA server. Please remember that this step is irreversible and removes all configuration related to the current FreeIPA server. Uninstallation logs are located in /var/log/ipaserver-uninstall.log.
Getting started with FreeIPA server
FreeIPA provides both command line and a Web user interface for easy management and administration of various services and for the configuration required. It uses a role based authentication system where the admin user is the privileged user.
During installation, an administrative user called admin is created. This is used for all administrative tasks in FreeIPA. Use the following command for authenticating as the admin user:
$ kinit admin
This command will prompt the user for the administrator password, which was given at the time of installation with option a, viz., Admin password.
Performing simple tasks using admin users: The simplest task in FreeIPA is creating users. The administrator can create users in FreeIPA using the following command. Keep in mind that you need to have a valid Kerberos ticket for the admin user.
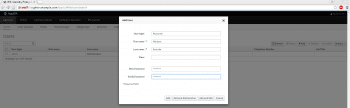
$ ipa user-add
This command is also interactive, just like ipa-server-install. After providing the required information, a user is created in the FreeIPA system. But, currently, the password for the newly created user is not set. The administrator can set a password using the following command:
$ ipa passwd <username>
The password provided at this prompt is temporary. When the user first logs into the system, the user is prompted to change the temporary password.
A newly created user can be authenticated using the following command:
$ kinit <username>
Using the FreeIPA server with the Web UI
The FreeIPA server provides a Web user interface for easy management and administration of various services provided. Logs related to the Web UI can be found in /var/log/httpd/error_log. After installing and configuring the FreeIPA server successfully, go to http://<ip-address-or-fqdn-ipa-server>/ipa/ui. FreeIPA uses self-signed certificates for encryption, so Firefox or any other browser will prompt the user for adding an exception for an untrusted connection to FreeIPA server. After proceeding to the login page, the user will be prompted for the username and password. The first time, the user can use admin user with the password specified at the time of installation using the -a option in the ipa-server-install command.
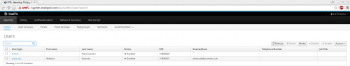
After successful login, users will land on the dashboard page.
The user can be added from the same page using the Add button on the user page.
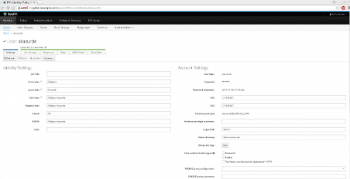
User details can be viewed by clicking on individual users in the User Page. The administrator can also edit/modify users details.
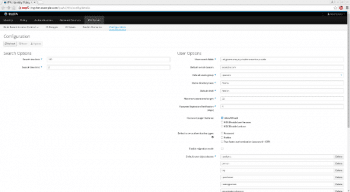
The administrator can change various FreeIPA related configuration settings using the Configuration tab found in the IPA server section. In this section, the administrator can modify settings such as the default shell used by users, the default email domain name, password expiration notification, and many other settings.
The administrator can also manage various things such as the domain name server, the certificate system (CS) using FreeIPA server, etc. Settings for DNS and CS can be found under Network Services and Authentication sections, respectively.
FreeIPA is an open source project written in Python. You can contribute to it by writing code, testing and documentation. Details related to contribution towards FreeIPA can be found at http://www.freeipa.org/page/Contribute. For more details and information related to FreeIPA, please visit http://www.freeipa.org/page/Main Page







































































