Crossplane is an invaluable asset for developers and IT professionals, as it offers a Kubernetes-centric approach to provisioning and monitoring cloud resources. Let’s explore its benefits.
Crossplane, an open source framework from Upbound, is transforming the container orchestration landscape by extending Kubernetes’ capabilities to manage and provision infrastructure as code (IaC) across a variety of cloud platforms. Using Kubernetes-native tools, it provides a framework that is both intuitive and robust for managing cloud infrastructure. By employing Crossplane to deploy a web application on Azure, you can take advantage of a unified, declarative configuration approach that facilitates resource management and is consistent with contemporary DevOps practices.
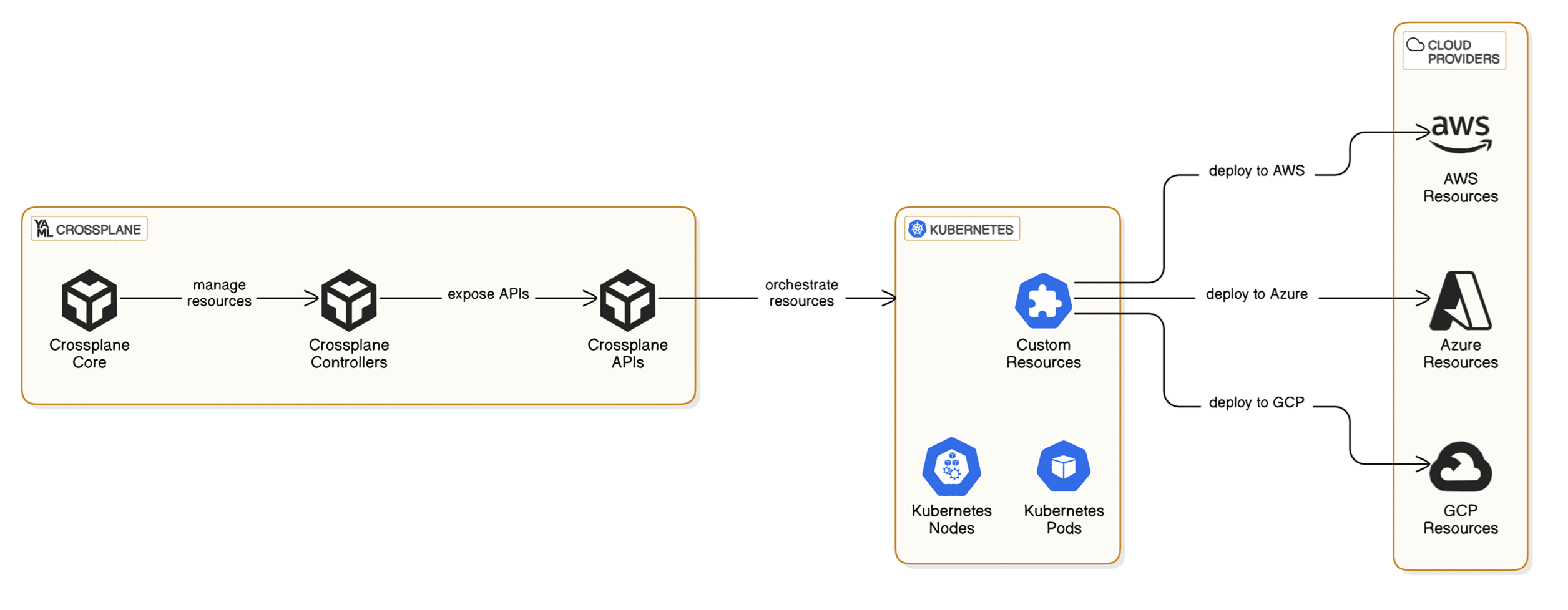
Crossplane is an open source project that enhances the Kubernetes API to facilitate the management of cloud infrastructure. It enables users to define and provision cloud resources by utilising Kubernetes custom resource definitions (CRDs). This method guarantees that infrastructure administration is consistent with the declarative and API-driven principles that Kubernetes employs for application deployment.
The Crossplane framework is a potent tool that simplifies the administration of cloud infrastructure in the context of cloud-native computing.
Declarative configuration
Declarative configuration is the foundation of Crossplane’s functionality. Crossplane enables users to specify the intended state of their infrastructure in YAML manifests by capitalising on Kubernetes’ declarative nature. This method simplifies the process of administering complex infrastructure by abstracting away the underlying implementation details, enabling developers to concentrate on the high-level design. Declarative configuration guarantees that the system consistently endeavours to attain and sustain the specified state, thereby simplifying the orchestration and management of resources across multiple cloud environments.
Self-healing control plane
The self-healing control plane of Crossplane is intended to improve the reliability and resilience of cloud infrastructure. This mechanism operates by perpetually monitoring the system’s state and automatically resolving any discrepancies between the desired and actual states.
Crossplane’s control plane detects anomalies and implements corrective measures to re-establish the desired state when a resource deviates from its intended configuration because of manual intervention or external factors. This guarantees a high level of availability and minimises the operational overhead that is associated with manual interventions.
Reconciling controllers
Reconciling controllers are the foundation of Crossplane’s functionality, as they are responsible for managing the lifecycle of resources. The configuration manifests specify the intended state, which these controllers continuously reconcile with the actual state of the infrastructure. In doing so, they guarantee that the infrastructure remains in a consistent and predictable state. Crossplane capitalises on the control loop mechanism of Kubernetes, which enables controllers to monitor modifications to resource specifications and implement the actions needed to reconcile the current state with the desired state. This automation mitigates the risk of configuration drift and improves the system’s overall stability.
Extensibility
One of the most noteworthy attributes of Crossplane is its extensibility. The framework can be expanded by incorporating the concepts of Configuration Packages and Composite Resource Definitions (XRDs). Custom resources that represent higher-level abstractions of infrastructure components, such as databases, networks, or complete application stacks, can be defined by users using XRDs. On the other hand, Configuration Packages facilitate the grouping of numerous resource definitions and their respective controllers into reusable units. This modularity enables organisations to customise Crossplane to meet their unique requirements and seamlessly integrate it with their current procedures and tools.
Extending Kubernetes for infrastructure as code
Crossplane augments Kubernetes’ capabilities to provision and administer infrastructure as code (IaC) across a variety of cloud platforms, such as Google Cloud, Azure, and AWS. It incorporates infrastructure management into the Kubernetes ecosystem by defining infrastructure resources as Kubernetes Custom Resource Definitions (CRDs). This method allows developers to utilise a unified set of tools and practices to administer both application and infrastructure resources. Users can provision and administer infrastructure in a cloud-agnostic manner using Crossplane’s provider ecosystem, which supports a diverse array of cloud services.
Building cloud-agnostic and cloud-native solutions
Crossplane’s capacity to facilitate the development of cloud-native and cloud-agnostic solutions is one of its primary advantages. Crossplane enables developers to construct applications that are not inextricably linked to any specific cloud provider by abstracting cloud-specific details and offering a standardised interface for infrastructure management. This decoupling improves portability and flexibility, allowing organisations to implement multi-cloud strategies and circumvent vendor lock-in. Furthermore, Crossplane’s integration with Kubernetes guarantees that applications are developed from the ground up in accordance with cloud-native principles, including observability, resilience, and scalability.
Prerequisites for Crossplane
Ensure that the following are present in order to develop infrastructure as code using the Crossplane platform solution:
- Kubernetes cluster (private or public cloud)
- kubectl has been deployed and configured
- Crossplane has been implemented in your Kubernetes cluster
- Azure account with the necessary permissions
Now, let’s start with the configuration and deployment steps.
Step 1: Install Crossplane Azure provider
To commence the deployment of a web application on Azure using Crossplane, it is necessary to install the latter on your Kubernetes cluster. The following example illustrates the process of developing a web application that is connected to a Postgre SQL database backend and deployed using Crossplane orchestration. Install the Azure provider for Crossplane first. This provider enables Crossplane to oversee Azure resources.
run the following in bash prompt kubectl crossplane install provider crossplane/provider-azure:v0.17.0
Step 2: Create Azure provider config
The subsequent stage is to configure the Azure provider once Crossplane is operational. This allows Crossplane to oversee Azure platform resources. Generate a Kubernetes secret to house your Azure credentials. Establish a provider configuration for Azure that incorporates your Azure credentials.
```yaml script for Azure Provider config apiVersion: v1 kind: Secret metadata: name: azure-creds namespace: crossplane-system data: credentials: --- apiVersion: azure.crossplane.io/v1alpha3 kind: ProviderConfig metadata: name: example spec: credentials: source: Secret secretRef: namespace: crossplane-system name: azure-creds key: credentials ```
Step 3: Define a resource class
The resources necessary for your database instance can be defined after the Azure provider has been configured. Begin by establishing a resource group and specifying a resource class for the Azure PostgreSQL instance.
```yaml script to define resource class apiVersion: database.azure.crossplane.io/v1beta1 kind: PostgreSQLServerClass metadata: name: standard-postgres specTemplate: location: West US resourceGroupName: my-group sku: tier: GeneralPurpose family: Gen5 capacity: 2 storageProfile: storageMB: 5120 administratorLogin: myadmin administratorLoginPasswordSecretRef: name: db-password key: password ```
Step 4: Create managed resources
Establish a managed resource for the PostgreSQL instance like the yaml script given below:
```yaml script for managed resource config to PostgreSQL database instance apiVersion: database.azure.crossplane.io/v1beta1 kind: PostgreSQLServer metadata: name: my-postgres spec: forProvider: resourceGroupName: my-group location: West US sku: tier: GeneralPurpose family: Gen5 capacity: 2 storageProfile: storageMB: 5120 administratorLogin: myadmin administratorLoginPasswordSecretRef: name: db-password key: password providerConfigRef: name: example ```
Step 5: Deploy the web application
Once the AKS cluster is operational, it is possible to deploy your web application. Begin by establishing a Kubernetes deployment and service for the application. Deploy the web application, which is a sample NGINX deployment, to the Kubernetes cluster.
```yaml script example for deploying the web application with nginx apiVersion: apps/v1 kind: Deployment metadata: name: nginx-deployment spec: replicas: 2 selector: matchLabels: app: nginx template: metadata: labels: app: nginx spec: containers: - name: nginx image: nginx:1.14.2 ports: - containerPort: 80 --- apiVersion: v1 kind: Service metadata: name: nginx-service spec: selector: app: nginx ports: - protocol: TCP port: 80 targetPort: 80 type: LoadBalancer ```
This configuration in YAML will deploy your web application across three replicas and expose it through a LoadBalancer service.
| Feature | Crossplane | Pulumi | Terraform |
| Declarative configuration | Yes (YAML) | Yes (Code in multiple languages) | Yes (HCL) |
| Self-healing control plane | Yes | No | No |
| Reconciling controllers | Yes | No | No |
| Extensibility | High (XRDs and Configuration Packages) |
Moderate (Custom resources) | Moderate (Providers and modules) |
| Cloud provider support | Multi-cloud | Multi-cloud | Multi-cloud |
| Kubernetes integration | Yes | Partial | Partial |
| Programming languages | YAML | JavaScript, Python, Go, etc | HCL |
Comparison of Crossplane, Pulumi, and Terraform
In recent years, Crossplane has gained popularity as a cloud-agnostic solution, despite the presence of competitors like Terraform and Pulumi. For a thorough understanding of Crossplane’s capabilities, it is imperative to compare it to other prevalent IaC tools, including Terraform and Pulumi (refer to the Table above).
In summary, Crossplane is a robust container orchestration framework that provides declarative configuration, self-healing, extensibility, and controller reconciliation. It is an optimal option for developing cloud-agnostic and cloud-native solutions due to its seamless integration with Kubernetes and support for multi-cloud environments. Although Pulumi and Terraform also offer valuable IaC capabilities, Crossplane’s distinctive assets are its comprehensive infrastructure management approach and its capacity to exploit the full potential of Kubernetes.