The first article in this series discussed the basic installation and configuration of IPCop 1.4.21. Subsequent articles covered six important add-ons: Advanced Proxy, URL Filter, Update Accelerator, Calamaris, Block Outgoing Traffic and Zerina. In this article, we will explore IPCop’s built-in VPN functionality, and implement a site-to-site tunnel-mode VPN using two IPCop.
Imagine a company with two offices at different locations, connected via the Internet. Here, organisational traffic travels over an “open” channel, risking confidentiality (unauthorised snooping of data) and integrity (unauthorised tampering of data). To overcome these risks, one of the best ways is to encrypt traffic over the Internet, which is what a VPN does.

Refer to Figure 1. The two private networks, Office 1 and Office 2, are connected using inexpensive Internet bandwidth. For data security, VPN Gateway 1 and VPN Gateway 2 establish a tunnel — all traffic flowing through it is encrypted, to ensure confidentiality and integrity.
To avoid firewalls at either end blocking this encrypted traffic as malicious, VPN functionality is incorporated into the firewall itself (or by using a separate gateway, and bypassing the firewall for VPN traffic). IPCop readily supports IPSec site-to-site (also called net-to-net) VPN.
The actual transfer involves the following steps: Gateway 1 and Gateway 2 establish a VPN tunnel. When a host in Office 1 sends data to a host in Office 2, VPN Gateway 1 encrypts the data, encapsulates the encrypted data in an IP packet, and sends this packet to VPN Gateway 2. VPN Gateway 2 de-encapsulates the packet, decrypts the data, and delivers it to the desired host in Office 2. This mechanism ensures confidentiality of data travelling over the Internet. Also note that internal IP addresses of Office 1 and Office 2 are not disclosed to the Internet.
The IPCop site-to-site VPN setup
Here’s an overview of the network used for the trial setup:
- Two IPCop firewalls, one for Office 1 (Sankalp) and Office 2 (Vasantika)
- The respective IP address ranges are 192.168.20.0/24 and 192.168.51.0/24
- The IPCop green addresses are 192.168.20.254 and 192.168.51.1
- The setup is carried out from Office 1.
- For identifying IPCop boxes easily, Office 1 is the left side, and Office 2 is the right side
Configure the boxes as follows: IPCop GUI –> VPNs –> VPNs menu, Configure Public IP or FQDN or red interface, and select the Enabled check-box (see Figure 1).
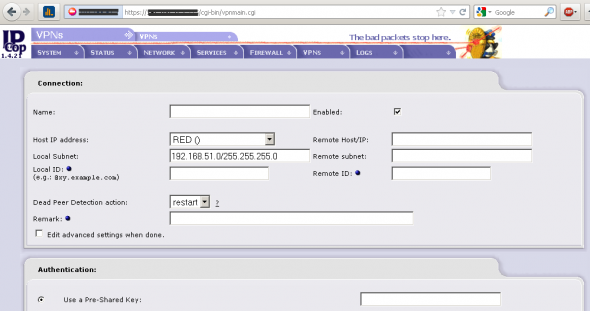
Select ADD under Connection status and control. Select Net-to-Net Virtual Private Network, and fill in the following parameters:
| Parameters | Value for left box | Value for right box |
| Name | TowardsVasantika | TowardsSankalp |
| Remote host/IP | 192.168.51.1 | 192.168.20.254 |
| Remote subnet | 192.168.51.0/255.255.255.0 | 192.168.20.0/255.255.255.0 |
| Host IP address | Office 1 RED IP Address | Office 2 RED IP Address |
| Local subnet | 192.168.20.0/255.255.255.0 | 192.168.51.0/255.255.255.0 |
| Use a Pre-Shared Key (PSK) | Thisisatestpresharedkey | Thisisatestpresharedkey |
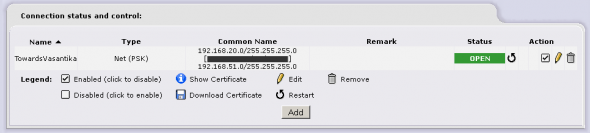
Scroll down, then click on Save to complete both configurations. Successful completion will open the tunnels immediately, as seen in Figures 3 and 4. Now, all hosts from either office can access hosts from the other office, using their IP address.

The security of PSK-based VPNs depends on the strength and confidentiality of the key. The key is also required to be distributed securely to the remote gateway location(s). If the PSK is compromised, the whole network may be under threat. To overcome this problem, certificate-based VPNs can be employed, using the inbuilt certificate generator provided with the IPCop distro, as follows: Generate a Root/Host certificate on both the IPCop boxes — scroll to the bottom of VPNs –> VPNs, give a CA name, and click the Generate Root/Host Certificates button. Fill in the required details. Download the Host and Root certificates of both the boxes.
On the left IPCop, go to the VPNs –> VPNs menu and add a new Net-to-Net VPN connection. Set the Remote Host IP as the RED IP of the Right IPCop, and Remote Subnet as 192.168.51.0/255.255.255.0. Upload the Right IPCop’s host certificate. Save this setup. Upload the Right IPCop’s root certificate via the VPNs –> VPNs menu, giving the correct CA name used while creating the certificate.
Repeat the same process on the Right IPCop box, using the corresponding Left IPCop host and root certificates.
That is all! If the configuration is correct, the tunnel will immediately open. You may verify this from Connection status and Control under the VPNs –> VPNs menu.
IPCop offers an excellent cost-effective solution to establish site-to-site VPNs. Once established, the connectivity is very stable, and requires attention only on rare occasions.
Important notes and troubleshooting guidelines
- Make sure that different IP subnets are used in the offices.
- The default value in the “Public IP or FQDN for RED interface” VPN setup field could have the service provider’s name, such as
IPADDRESS.static-xxx.serviceprovider.net.in. Make sure you remove non-IP-address text. - IPCop RED with private IP addresses (such as 192.168.x.x or 10.x.x.x) makes VPN configuration really difficult. This happens when IPCop is installed inside a router configured in route mode. Here, reconfigure the router in bridge mode, so that IPCop RED will get a public IP.
- Refresh the browser a few times if tunnel “open” status is not displayed.
- Ensure correct uploading of root and host certificates generated Ensure that the root and host certificates generated on the right box are uploaded correctly on the left box and vice versa.
- If the tunnel does not open, verify the parameters on both boxes. You can also check Logs –> System logs –> IPSec logs for further troubleshooting.
- Additional tunnels can be created to network multiple offices; the most important point to remember is to use different IP subnets for different offices.
- IKE aggressive mode (available under advanced options) is definitely not preferred; it transmits a pre-shared key in clear text.
- Though IPCop has an inbuilt certificate generator, you may also purchase and use certificates from various certifying authorities.
References
- IPCop website
- IPCop forum
- IPSec basics
- NIST IPSec VPN guidelines [PDF]










































































Hello,
My name is Alec and I work for the marketing department at VPN4ALL
ltd, I am quite fascinated by your blog posts, and I must commend your writing
skills.
I was wondering if you would be interested to test our VPN
software for free so as to prepare a review about our services on your site.
Our website is a personal VPN service that encrypts all your data
transmitted over the internet and tunnels your online communications through
one of our secure server locations. It changes your visibility to the World IP
address and protects you against online snoopers and intruders. All in one
click!
This review may prove to be quite beneficial if a partnership was
formed between both parties whereby you’d be earning commissions on sales your
referrals make referred through an affiliate link in your website/review.
The commission earnings start from 25 percent and go up depending
on your performance with our affiliate program, plus you get to receive a,
•A sign up bonus of $9.95 loaded into your Affiliate account once
you sign up with us.
•Enjoy Recurring commissions on every renewal your referrals make
•Enjoy our VPN Client by becoming our VPN active member.
Special offer: the first three orders you refer to us will qualify
you for a $5 cash bonus (money deposited into your account on top of your
regular commission) + a $10 gift certificate from VPN4ALL ltd to purchase any
of our packages.
To join (or learn more about) our program you may fill out the
application here https://www.vpn4all.com/userportal/guestaffiliates.php.
If you’re not ready to join the affiliate program right away, I
would still love to hear back from you: to see how/if we can still work
together. I’m very much looking forward to your reply.
Regards,
Alec/Marketing department
http://www.vpn4all.com