This article explores the challenges in managing handheld devices based on the Android platform that are being used in an enterprise. It also explains the complexities of creating an enterprise-ready Android platform, which is a must for companies that want to manage their workforce and keep their data secure.
This article explores the challenges in managing handheld devices based on the Android platform that are being used in an enterprise. It also explains the complexities of creating an enterprise-ready Android platform, which is a must for companies that want to manage their workforce and keep their data secure.
The enterprise mobility trend and its unique benefits have made enterprises open to empowering their employees and customers with one-tap access to business data from any handheld device. New business opportunities are emerging as billions of people rapidly embrace the use of mobile devices. However, the innovation rate in mobile devices, social media software and cloud computing is accelerating faster than the enterprise adaptation rate.
In a report by the comScore MobiLens service, which underlined key trends in the US smartphone industry during the three month period ending June 2013, Google Android is the leading smartphone platform with 52 per cent market share.
There is little doubt that Android has become the dominant platform because of its commercial-friendly licence, hassle-free supply chain commoditisation, robust architecture, together with the open source and easily customisable code base. These benefits have led more and more enterprises to look at Android as a cost-effective mobile platform for corporate-owned devices given to their field force. While empowering the field force results in high productivity gains, companies have certain concerns regarding regulatory compliance, security, technology, expense, organisational policy, and legacy technology constraints. Addressing all of these concerns is critical for an enterprise and, in turn, has created a high demand for devices powered by an enterprise-ready Android platform.
The need for an enterprise-ready Android platform
As we know, managing devices is inevitable for any enterprise in this era of cyber-crimes and the high incidence of security breaches suffered by enterprises due to lack of proper device management. Enterprises typically manage their employees devices by leveraging one of the several mobile device management solutions available in the market like BoxTone, MobileIron, Soti, etc. Like other smartphone platforms, Android too provides for some essential device management features built into the platform and exposed to the applications. The mobile device management solutions deploy an on-device agent that takes care of policy management and enforcement by leveraging the built-in device management APIs supported by the mobile platform. The scope of the policy imposed on the device by the mobile device management solution is, however, limited by the platform hooks provided by the underlying mobile platform for managing the device.
Sadly, the typical security concerns of an enterprise do not get covered in the built-in device management support that the default Android platform provides. However, the open source nature of Android and its easy customisation empowers us to extend the OS to support the specific needs of enterprise usage. Here is an example. In February 2013, American Airlines (AA) deployed 17,000 Samsung Galaxy Notes to its flight attendants for better management of their crew functions, resulting in a better passenger experience. It customised Android to block the phone dialling and camera functions. It removed certain non-essential apps from the platform and pre-bundled various applications that were related to its crew operations. And most important, it chose the Samsung Galaxy Note because it is built on an enterprise ready Android platform, i.e., the Samsung for Enterprise (SAFE) platform. This offers a wide range of device management capabilities, thereby going much beyond the basic device management capabilities of the default Android platform. Rich device management capability, a favourable licence, endless customisation options and cost-effectiveness were the key enablers of this success story.
Given below are some of the enterprise-specific device management requirements that drive the need for an enterprise-ready Android platform.
Communication management: An enterprise systems administrator should be able to whitelist or blacklist outgoing SMS or phone calls for a user. Totally disabling outgoing SMSs or phone calls may also be required at times.
Application management: The sys admin should be able to whitelist or blacklist the applications that can be installed on the user device.
Security management: Data security is the prime concern for any enterprise. The data stored in encrypted form on the device and memory cards should be accessible to only authorised personnel through the proper application channels.
Second, a ‘remote wipe’ for selected users (enterprise user space) should be possible in case of a device being lost to ensure that the enterprise’s data doesn’t get into the wrong hands.
Another important function for some enterprises that want to monitor user devices is that all network communication be necessarily through a VPN tunnel. In other words, the user should not be able to carry out any network related communication if the user is not logged on to the VPN client.
Last of all, the sys admin should be able to enable or disable certain accessories and features depending on the degree of security required for the different types of enterprise data. For example, the admin may need to block Internet tethering, Bluetooth, Wi-Fi, the use of an SD card, USB, screen capture, OTA firmware upgrade, the camera, GPS, etc.
Expense management: Enterprises usually have certain budgetary limitations on the data and phone call usage of users. The admin should be able to ensure a role- or user-based data and phone usage quota along with roaming restrictions that control device usage while travelling.
Building an enterprise-ready Android platform
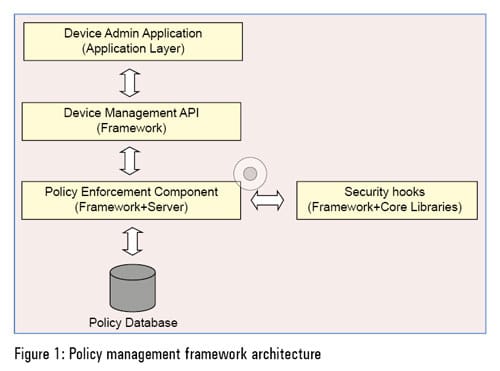
The high level architecture of an enterprise-ready Android platform with an enhanced policy management framework is depicted in Figure 1.
Security hooks
Security hooks are the deterministic control points for a feature in the Android stack. They are uniquely identified in the specific Android version code base and feature specific policy enforcement checks that would be introduced at that point. Every hardware or software feature in a device can be controlled depending on the device management needs of the enterprise. For example, security hooks can be identified for controlling the use of Bluetooth, Wi-Fi, SMS, phone calls, etc, as per policy requirements.
Policy enforcement component
The policy enforcement component provides support for managing and enforcing various policies on the device. It is the core component of the enterprise-ready Android platform and has two major responsibilities.
Policy management: Device admin APIs use this sub-component for reading and updating policy configuration on the device. Policies set on the device are persisted by this subcomponent on it, and are made available for policy enforcement workflow when triggered.
Policy enforcement: The policy enforcement component gets invoked every time a feature that supports some policy is being used. For example, if you are sending an SMS and there is a ‘contact whitelisting’ policy for outgoing SMS, then the policy enforcement component gets invoked from the appropriate security hook point and checks if the contact to whom the SMS is to be sent is part of the contact whitelist. An outgoing SMS could get blocked if the contact is not part of the whitelist, and an appropriate enterprise policy compliance alert is generated to warn the user.
Device management APIs
This component resides at the framework layer. It provides APIs for device management applications. It is basically a wrapper layer over the policy enforcement component and is capable of reading or updating policy configuration information.
This component defines a custom permission. Any application that uses these APIs is required to use the pre-defined permission. It also enables some pre-determined listeners (that would be implemented at the device admin app end) to receive notifications on updates in the device policy configuration.
Device admin application
The device admin application (also called an on-device agent) resides at the application layer. It allows the retrieval and updating of various device management policies and their details. It accomplishes this by leveraging the device management APIs for reading and updating policy. The device admin application requires pre-defined permission for using device management APIs.
Deploying this platform on a device alone would not make it manageable. The mobile device management (MDM)vendor or OEM needs to implement the corresponding device admin application in order to support this platform for the MDM solution to be used.
To conclude, with the increasing growth in enterprise mobility, smartphones powered with an enterprise-ready Android platform have become the need of the hour. In order to address this need, enterprise mobility solution providers offer ready to use, enterprise ready Android platforms with pluggable points for customisation. The platform can be easily tailored and customised as per specific needs, and then factory set on Android devices to gain the required manageability of devices.