Let’s take a quick look at the free tools and libraries that are available for the security of Docker and containers.
Docker is a containerization solution that lets programmers encapsulate a service together with its dependencies, prerequisites, libraries and operating system. It facilitates app deployment and portability by isolating application code from underlying system code.
Over the past few years, more and more apps are being containerized rather than being hosted on virtual machines, thanks to the use of Docker. The latter is essential to this shift because it facilitates the smooth adoption of containerization technologies. Use cases for Docker have emerged across every conceivable business sector, no matter how big or small.
By decomposing a code into smaller and more manageable pieces that can communicate with one another via REST APIs, a microservices design helps developers overcome development challenges with Docker technology. Each feature may often be implemented as its own service, meaning it can run separately from the others. As a result, businesses can hasten the pace of release cycles, expand operations on demand, and implement code changes with minimal disruption to service. Among the many applications of Docker, one of the most common is the transition from monolithic to microservices based architectures.
One of the most interesting applications of microservices architecture is the container. A container is a standardised software package that separates an application’s runtime from the system on which it runs by enclosing it with all of its dependencies and resources. Containers are different from virtual machines in that they only virtualise software layers above the OS.
Docker’s positive impact on enterprises and real world scenarios
Because of its mobility and ecosystem, Docker has grown to be synonymous with containerization. It has been adopted and supported by all the main cloud providers including GCP, AWS, Azure and many others. Organisations are saving a lot of money by using containerization and running several containers on a single host. Since Docker enables service deployment on inexpensive commodity hardware, it may be used to avoid spending money on costly servers.
Docker is prominently used for creating and managing containerized development environments with Docker images, which enable rapid provisioning and consistent performance over the course of a project’s life span. In addition, it provides comprehensive assistance for all development-related tools, frameworks, and technologies.
Docker environments also make it easier to use tools like CI/CD, A/B testing, and webhooks. Thus, it is simple to include Bitbucket or GitHub repos with the development environment, allowing for automated builds to be generated from the source code and afterwards pushed to the Docker Repo.
One of the most important ways to put Docker to use is in the development and deployment of software. There is less risk of unexpected issues arising due to configuration variations between the test environment and the production environment when developers conduct tests in the same environment where the apps will run in production.
Security and integrity aspects in Docker containers
Once attackers have compromised a host, they frequently have the resources to go laterally and compromise more containers. A container’s ability to access the system file directory might weaken the effectiveness of security measures. In rare cases, attackers who get root access to a container can use it to gain root access to the host too.
When it comes to container security, Docker has you covered at every stage: during development, during deployment, and during orchestration. However, the Docker daemon, container runtime, Dockerfile, and base images are all potential entry points for attackers.
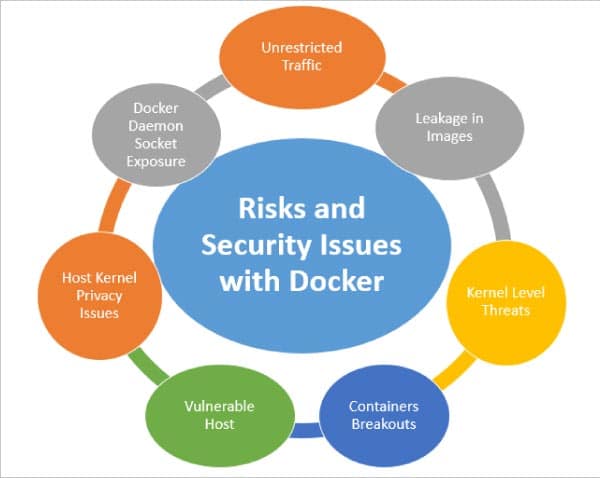
So Docker does come with a few risks and vulnerabilities:
- Unsafe and unrestricted traffic with vulnerable communications
- Malicious and vulnerable container images
- Host system security loopholes
- Unrestricted access
- Exposure of Docker daemon socket
- Privacy leakages in Docker images
- Vulnerabilities with host kernel
- Container breakouts
- Kernel level threats
Table 1: Key tools and libraries that help with security in a Docker environment
| Library / Tool | Usage | URL |
| Docker Bench for Security |
Audit of Docker containers and benchmarking | https://github.com/docker/docker-bench-security |
| Cilium | Kernel layer security | https://github.com/cilium/cilium |
| Anchore | Inspection of container security with integration of policies | https://github.com/anchore/anchore-engine |
| OpenSCAP Workbench | Integration of security and privacy policies | https://www.open-scap.org/ |
| Dagda | Scanning of viruses, malware, Trojans and other malicious traffic in Docker containers | https://github.com/eliasgranderubio/dagda |
| Notary | Integration of cryptography and deep level security | https://github.com/notaryproject/notary |
| Grafaes | Internal policies for privacy and security | https://grafeas.io/ |
| Sysdig Falco | Deep level visibility and scan of containers with behavioural activity analysis | https://github.com/falcosecurity/falco |
| Banyanops Collector |
Evaluation of Docker on different perspectives and dimensions | https://github.com/banyanops/collector |
| Dockscan | Security scanner against vulnerability | https://github.com/kost/dockscan |
| Batten | Docker audit toolkit | https://github.com/dockersecuritytools/batten |
| Inspec | Testing, audit and deep level analysis of the Docker environment | https://github.com/inspec/inspec |
Free tools and libraries for Docker and containers
Though Docker is a secured environment, there is huge scope for research in its privacy, integrity and security aspects. Lots of libraries and frameworks are available and still under development to cope with the security leakages in a Docker environment (see Table 1). The Common Vulnerabilities and Exposures (CVE) database and the National Vulnerability Database (NVD) are the key databases that receive a lot of attention from auditors and are used as standards by other organisations. After the container image is scanned, its contents are exposed, and comparisons are made against the vulnerability manifests in order to assess its security posture.
Organisations can benefit a lot from automating container audits and other container security activities since doing so allows teams to detect issues early in the build process. A number of free and open source libraries are still under development and will be released at continuous intervals to help businesses use them in real world scenarios.












































































