This article describes the various functionalities of a network-based firewall, besides taking readers through the installation and configuration of IPCop 2.0.6, especially from the perspective of a small and medium business. It also illustrates how a securely configured firewall ensures data security and mitigates various risks such as virus spread.
IPCop is a complete Linux distribution whose sole purpose is to protect the networks it is installed on. By implementing the best of current technology, outstanding new technology and secure programming practices, it has become the Linux distro for those wanting to keep their computers and networks safe.
Basics
There are two types of firewalls.
Host-based firewalls are typically software programs installed on an operating system. They can control which software programs installed on the computer can access the Internet and who can access the host system.
Network firewalls are used to control access between any two networks–for example, your system or network on one side, and the Internet on the other. Any computer system or network directly connected to the Internet without any protection is exposed to many risks. From a security perspective, once you are connected to the Internet, it is your computer, your system and your network against everybody else on the other side. Even unknowingly, other infected systems could cause harm to your system. A firewall is used to mitigate these risks and to secure your internal systems from malicious users and programs working on the external side.
Network security for small businesses
Though awareness about firewalls is on the rise, even today, many organisations assume that installing the operating system, application software and the connecting network is all thats required to set up their IT infrastructure. Many key network security aspects such as the use of managed switches, securing the wireless network, changing default passwords, deploying a firewall at the network gateway, etc, are not considered.
Why open source?
One of the primary reasons for not securing networks is the expense involved. Here, open source software is an alternate to commercially available products. These include operating systems, word processors, spreadsheets, presentation tools, graphic tools, browsers, etc.
Open source has a wide range of firewall distributions to offer. Some of them are pfsense, endian, untangle, ipfire and, of course, IPCop. These can be installed on any computer system supported by the corresponding distro -the hardware configuration requirement is absolutely minimal. Even an old computer system with a Celeron CPU, 512 MB RAM and a 20 GB hard disk can run these firewalls. For the few who think open source has no support, some of these firewalls have paid support available.
Readers, please think this over: Any properly configured firewall, even an open source firewall distribution, is certainly better than the best non-configured branded firewall!
SME network and security requirements
Let us consider the typical set-up of a small and medium business — a head office with 25 users, branch offices with 4-5 users, and a number of field representatives. Let us try to summarise their IT network requirements.
Head office:
- Computer systems network
- Isolation of Internet exposed systems from the
internal network - Internet access control-website filtering,
services filtering - Gateway anti-virus and anti-spam
Branch offices:
- Site to Site VPN Connectivity – for head office connectivity
- Internet access control- website filtering,
services filtering
Field representatives:
- Host-to-network VPN connectivity (for travelling individuals)
Depending upon the number of users and the features required, the price for commercially available firewalls suitable for SME network ranges from Rs 10,000 to Rs 50,000. In addition, an annual subscription is required for continued support. The first few VPN client licences are free, while additional licences typically cost Rs 2000 per user. The firewall has a pre-defined lifecycle and one may have to purchase a new model after support for the current model expires. Against this, open source distros are available free and come with community support. Paid support/ maintenance is also available through local vendors.
IPCop 2.0.6, the open source firewall that runs on any old computer system and which meets most of these requirements, is simple to install and has excellent community support, which is absolutely free!
Note: Gateway anti-virus and anti-spam module is currently not available for IPCop 2.0.6
The IPCop firewall
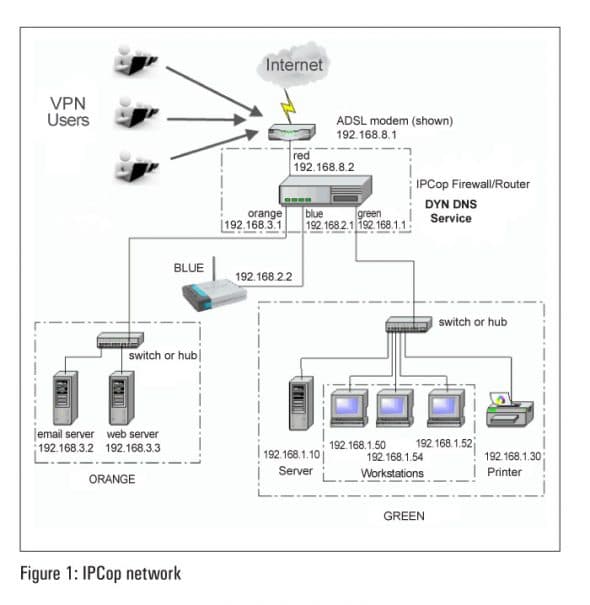
Let us try to understand a network that uses IPCop, with the help of a simple diagram (Figure 1).
At the head office, the IPCop firewall will segregate the internal network as:
- Protected computers ‘Green network’192.168.1.0
- Protected wireless network ‘Blue network’ 192.168.2.0
- DMZ computers (systems to be accessed from the internal network and from the Internet) ‘Orange network’ 192.168.3.0
Depending upon the number of users in any remote branch, the connectivity will be established either by site-to-site VPN (for over five users) or by site-to-host OpenVPN. These VPN users can access various services from the internal network for example, a CRM/ERP software.
If more than five users from one branch wish to connect to the head office, at the same time, site-to-site VPN could be deployed using the IPCop firewall at that branch.
IPCop installation
Start by downloading the ISO image of the latest stable release from http://ipcop.org/download.php. Burn it to a CD. IPCop installation is very simple and straightforward. You require a computer system with a minimum of two Ethernet cards, 512 MB RAM, a 20 GB hard disk or a 1 GB flash drive, and a CD-ROM drive for installation. Start the installation by booting from the IPCop CD.
The first screen greets you with the IPCop mission statement: The bad packets stop here. Press Enter at the Boot prompt. Select the desired language; an information dialogue box tells you that pressing Cancel will reboot the system. Continue by clicking OK. Select the type of keyboard and the time zone, then enter the correct date and time, if required. Select the hard disk on which to install IPCop. Beware that all the data on this disk will be erased. Then click OK to continue. Here, a very interesting screen greets you, irrespective of whether the installation is on the hard disk or on a flash drive. Select the desired disk type from Flash/Disk. The installer will create the required file systems and swap space, ask whether you have an older backup to be restored, and complete the installation.
Reboot the system and continue to configure the box. Enter the host name and domain name, before selecting the Red (Internet) interface type and Ethernet card. Note that here you can configure any Ethernet card to any interface. In the earlier version, the first detected Ethernet was always assigned to Green, and it was tricky to change it later. Also, to identify the card easily, you can set it in LED blinking on mode. Assign Green, Red and Blue (if required) cards, and enter the Green IP address and subnet mask. Also, select the Red type, such as Static, PPPoE, etc. You may enable DHCP if desired, and enter root, admin and backup passwords to complete this part of the configuration.
IPCop configuration
Reboot the system and wait till you see the login screen (which can be used to log in as the root user). Use a client computer browser to open https://IPCopIP:8443 and authenticate yourself as the admin with an earlier defined password. The first step is to complete the set-up by configuring the Internet. This trial set-up uses PPPoE on the Red interface. Proceed to Network > Dialup, and enter the PPPoE username and password. From the Home screen (System > Home), click the Connect button to connect to the Internet. Configure the IPCop Green IP as the default gateway and DNS in the client TCP/IP settings.
The next important step is to upgrade to the latest release. Start by checking whether new updates are available; go to the System > Update page. Select Refresh Update List and check for the availability of new updates. Do apply all the available patches. After the updates, IPCop will be upgraded to the latest version 2.0.6 (as of July 1, 2013).
Configure client systems under Green and Blue with the corresponding IPCop interface IP address as their default gateway and DNS. An external DNS IP address can also be used.
That is all… you can now start browsing securely.
To conclude this article, let me answer a few questions that are frequently asked by users at various organisations, and explain three real life scenarios where a properly configured firewall could have helped. Let me emphasise that not just a branded, but any properly configured firewall would have saved the day.
Firewall FAQs
”All our systems have anti-virus. Do we require a network firewall?” Yes, anti-virus is not a substitute for a network firewall.
”All our systems have a host-based firewall. Do we require a network firewall? ”
Yes. First, configuring host-based firewalls on multiple systems itself is a big task. Also, these firewalls sit only on operating systems and do not protect other network devices such as network printers, access points, Network Attached Storage (NAS) boxes, etc.
“Since we have a firewall costing Rs 100,000 installed in our network, arent our systems protected? ”
Not sure. While auditing, I have observed that these firewalls are not configured properly. The best approach to configuring any firewall is to deny all traffic from the firewall and allow only the desired traffic by creating rules, one by one. Such an approach generates a lot of reconfiguration calls after installation is completed and hence is not preferred by many. You may buy or install any good firewall. Much depends on its configuration rather than anything else.
“Is it possible to filter https traffic using IPCop?”
Yes, let me try to explain. When you browse a http website, all data travels in clear text format. In simple language, this means an intruder can sniff this traffic and read through your login ID and password. To overcome this, https websites use an asymmetric encryption mechanism so that the traffic is sent in encrypted form from the browser to the Web server, thus ensuring its confidentiality. Now, since this traffic is encrypted, even a firewall cant read it! Then the question is, how can it be filtered? There are two ways:
Blocking the https protocol will disable all https traffic even all required https websites will be blocked. You can allow various sites by finding their IP addresses and creating corresponding allow rules. This method is tedious, specially considering that many websites have multiple IP ranges, and a few website IP addresses change.
Blocking all direct https traffic and allowing it only via Advanced Proxy (inbuilt in IPCop). Here, all browsers will have to be configured with proxy settings. The https proxy functions as follows:
1. Browser https traffic is terminated by the IPCop proxy (instead of the destination Web server).
2. The URL filter reads the requested URL.
3. If the URL is on the blacklist, the request is dropped.
4. If the URL is not on the blacklist, a new connection is initiated from IPCop to the destination Web server.
5. A reply from the Web server is terminated on IPCop.
6. IPCop forwards the reply to the corresponding Web browser.
Here, please observe that the traffic is decrypted and re-encrypted by IPCop. This results in a slight reduction in browsing speed, and technically, IPCop can read https traffic. But this is the way all https URL filters work.
Real life scenarios
Here are some real life scenarios where a properly configured firewall could have helped
Sasser worm: Sasser attacks the vulnerable Microsoft SMB port 445. Once affected, the system shuts down in one minute, displaying a count-down window. If you are really interested in experiencing Sasser, try this: Install Windows XP without the service pack, and connect your system to the Internet directly in a short while, the system will get infected by Sasser. (Be very careful while you play around!) This is because, some Sassers are still in the wild and try affecting vulnerable systems even today!
Here, putting your system behind a network-based firewall will definitely help. Port 445 of the internal system will not be accessible from the Internet and the worm will be blocked by the firewall before entering the Internal network.
CodeRed worm: On July 13, 2001, a number of computer systems running the Microsoft IIS Web server on Windows NT or Windows 2000 were affected by a worm called CodeRed. It is believed that about 300,000 servers were affected on Day One! The worm was designed in a very peculiar manner. From the 1st of any month to the 13th, it would try to spread to random IIS Web servers. Once a Web server was infected, it would in turn generate a lot of traffic towards the Internet searching for IIS servers randomly, ultimately infecting the vulnerable ones.
A properly configured firewall denying any traffic to be initiated from the Web server towards the Internet could have curtailed the spread of this worm. Also, a Web server should only reply to the incoming Web requests and should not be allowed to browse the Internet.
In this case, infection of vulnerable IIS Web servers (even those sitting behind a firewall) was inevitable, but a properly configured firewall could have definitely stopped the spread of CodeRed from the affected Web server.
ISP connectivity issues: In an earlier time, one ISP started its services from a central area of Pune with much fanfare. A horrifying fact was that all connected networks were not separated at the ISP end in simple terms, double clicking on Network Neighbourhood made all the systems connected to this ISP visible and, of course, the data on them accessible! Here, deploying a firewall would have assured separation
References
[1] Google search for IPCOP LFY
[2] IPCop official website: www.ipcop.org
[3] A great IPCop forum: www.ipcops.com