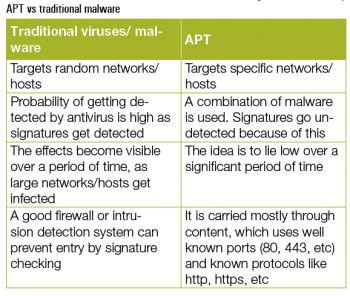
Advanced persistent threats or APTs are a kind of cyber attack that can go undetected for a long period of time. The objective of the attack is:
- To extricate vital data rather than cause damage.
- To gain access to the network or host.
The typical characteristics of APTs are listed below:
Advanced: They are highly sophisticated and targeted.
Persistent: They put in a lot of effort to achieve their goal and to reach the target.
Threatening: They have a newly generated payload compared to the conventional, target-specific payloads something not known to security personnel.
In an APT, the attackers deface the network, plant advanced malware and hide themselves until they receive the command to get off the target. An advanced persistent threat uses a step-by-step approach.
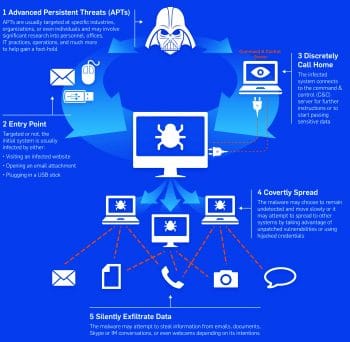
Intrusion kill chain
”Intrusion kill chain is crucial, but its not enough.” –Peter Tran.
The intrusion kill chain (also known as a kill chain, a cyber kill chain or attack cycles) is a model used to execute the successful pathway towards segmenting, analysing and mitigating the cyber attack. Various stages of attacks are performed in order to gain access to the target.
1. Reconnaissance: This is the initial stage of identifying and selecting the target. All the relevant information about the target is obtained by crawling the Internet (social engineering) to get personal information like email, social media ID, etc.
2. Weaponisation: At this stage, a RAT (remote administration tool or a Trojan) is encapsulated with any client application which is likely to be an executable.
3. Delivery: During this stage, the weaponised executable is transferred to the target via email, suspicious links, USB media, etc.
4. Exploitation: Once the executable is delivered to the victim, the payload triggers the Trojan and exploits the operating systems vulnerability or targets a specific app.
5. Installation: Installation allows the Trojan and attacker to remain in close proximity.
6. Command and control server: A command and control server is used to control the Trojan installed in the target via remote access.
7. Actions and goals: After six stages of progress, the goal is accomplished by compromising the host.

The intrusion kill chain often takes many days for a successful attack to take place. It is very hard to identify these chain processes due to their stepping stone behaviour (compromising multiple hosts to reach the target). Its very difficult to identify the first three stages of the attack cycle.
Zero day exploits
A zero day exploit is a computer application vulnerability which is unpatched and previously not known to security vendors. These security holes are exploited by the attacker before the vendor becomes aware of the exploits. Zero day attacks include data infiltration and exfiltration malware, malicious code, etc. The best example of a zero day exploit is Stuxnet, which was named the first digital weapon.
Stuxnet
Stuxnet, the first digital weapon, ranks No. 1 among zero day vulnerabilities when it comes to causing collateral damage to computers in the real world. Stuxnet was first discovered in June 2010, and reportedly destroyed one-fifth of the centrifugal pumps of the Iranian nuclear facility. Stuxnet is specific to PLC boards and targets the rotator which spins them up and down. It has unique characteristics which differ from traditional payloads of various malware and Trojans. According to the Kaspersky report, once the Trojan hits the system, it automatically compromises the host PLC boards and sparks chaos.
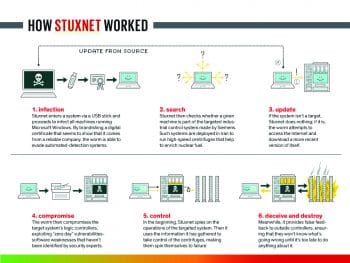
Components of Stuxnet
Various aspects of Stuxnet differentiate it from other malicious software. These range from modifying system libraries, targeting the Step 7 SCADA controller, the use of a command and control server (via RPC), installation of malicious driver code in system software like drivers, etc. Stuxnet is also capable of downloading auto updates, which update an older version installed in a system. It recursively communicates to the command and control server covertly, to pass on information about its spread, the devices affected and possible ways of getting updated. Stuxnet auto updates via a built-in peer-to-peer network. This kind of auto updating leads to different versions and different attack vectors. The recent version of Stuxnet uses LNK vulnerabilities, whereas the older version uses Autorun.inf.
LNK vulnerability: Stuxnet registers the code in an infected Windows computer. Whenever USB drives are inserted, Stuxnet automatically copies the code to the drive. A very interesting fact is that the code will work to infect any of three machines. If the drive is already infected, a new version of Stuxnet is updated to the drive for further infection. An LNK vulnerability contains four files with the .lnk extension in addition to Stuxnet DLL, which are used to execute the payload in different versions of Windows.
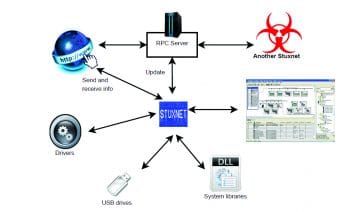
Autorun.inf: Autorun.inf is an auto run file which automatically runs the code in USB drives whenever the drive is inserted in a Windows machine. Here, the command and code for infection is inserted and configured in the autorun.inf file. Hence, the Windows OS ignores the Stuxnet data portion in the autorun.inf file.
WinCC
WinCC is an interface to SCADA systems; Stuxnet searches for WinCC and connects to the database via a hard-coded password. It then attacks the database using SQL commands by uploading and replicating a copy of code on a WinCC computer.
Network shares
Stuxnet can use Windows shared folders to propagate itself in a LAN. It drops and schedules a dropper file to execute it on remote computers.
Print spooler vulnerability (MS10-061)
Stuxnet copies and shares itself to remote computers using this vulnerability and then executes itself to infect the remote computers. In general, Stuxnet replicates into two, and then it copies itself into the C:\Windows\system folder with zero day privilege escalation and infects the computer.
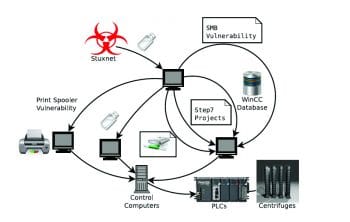
SMB vulnerability (MS08-067)
Server message block (SMB) is a network file-sharing protocol. Stuxnet modifies the path and sends data through a malformed path between remote computers.
Step7 project vulnerability
Stuxnet infects the executable of WinCC Simatic manager and modifies the shared libraries, DLLs, libraries for shared objects, code and data. Then it copies the additional code into the step7 directory, and connects to the command and control server for remote execution of payloads.
The attack phase
Stuxnet consists of two modules – the user module and kernel module.
User module: In the user module, there are several functions to do the following operations. First, Stuxnet itself injects malware code into the actual running process. This results in the execution of the malware code in the target address space. Then it checks for the appropriate platform (Export 15 Stuxnet routine to check for appropriate Windows version) to execute the code; if the machine is already infected, zero day vulnerabilities are used for escalating privileges. Finally, it installs (Export 16 Stuxnet routine for installation) two kernel drivers (Mrxnet.sys and Mrxcls.sys) – one for execution of Stuxnet after reboot and the other to hide the files.
Kernel module: Kernel module consists of two dropped driver files, namely, Mrxnet.sys and Mrxcls.sys. The latter is a driver used to mark itself as startup in the early stages of a boot. This driver takes responsibility for reading the registry and contains information for injecting Stuxnet code. Mrxnet.sys is used to hide the Stuxnet files; it creates the device object and attaches it to the system object (s7otbxdx.dll) of step7 to monitor all the requests.
Interestingly, as in the case of sabotaging the Iranian nuclear programme, Stuxnet monitored and recorded the normal operating frequency of centrifuges and fed the recorded data to the WinCC monitor during the attack. If the operator found the centrifuges are not operating normally, then Stuxnet shut itself down to a safe mode to remain undetected.
How to figure out if you are a victim ofAPT attacks
Heres a list of things you must do to spot an APT attack before it is too late:
- An APT may go unnoticed by a single antivirus/intrusion detection system; multi-level defence is required.
- Analysing network layered packets is a good way to keep a check.
- Log analysis from various sources with co-relation may help in early detection.
- You must monitor end points for suspicious behaviour.
- Good asset management should be in place to guard critical systems.
- Monitoring critical assets is very important.
References
[1] https://blogs.sophos.com/2014/04/11/how-do-apts-work-the-lifecycle-of-advanced-persistent-threats-infographic/
[2] http://en.wikipedia.org/wiki/Zero-day_attack
[3] http://en.wikipedia.org/wiki/Advanced_persistent_threat
[4] http://www.stuxnet.net/
[5] http://www.wired.com/2014/11/countdown-to-zero-day-stuxnet/
[6] http://www.engadget.com/2014/11/13/stuxnet-worm-targeted-companies-first/
[7] Paul Mueller and Babak Yadegari, Report on The Stuxnet Worm
[8] http://www.symantec.com/connect/w32_duqu_precursor_next_stuxnet