The global BYOD market is likely to grow to about US$ 266 billion by 2019, as forecast by MarketsandMarkets. With this, security and compliance are a priority for enterprise decision-makers.
According to IDC, the US mobile worker population will grow at a steady rate over the next five years, increasing to nearly 72 per cent of the total US workforce. Further, as per a StrategyAnalytics report, globally, the mobile workforce is set to increase to about 42 per cent of the total workforce by 2018.
Definitely, IT consumerisation is one of the key driving forces everywhere. Other drivers include the increasing affordability of mobile devices, combined with the growing acceptance of BYOD programmes. However, the most tactical challenge still remains to ensure a secure and policy-compliant mobile ecosystem.
Mobility is not just about the creation of appealing mobile applications its about changing the way businesses run. In this article, I will share with you the key challenges in creating an enterprise-grade mobile solution and how to overcome them.
Transformative enterprise mobile solutions
a transformative enterprise mobile solution is essentially an end-to-end solution built to optimally mobilise business processes. It must integrate seamlessly with enterprise backend systems. It must support mobile-specific features and, most importantly, it must comply with relevant IT security policies.
It involves making the solution secure from an enterprise data privacy perspective and enhancing productivity for users. It helps in fostering life cycle management for apps and devices, and also integrates well with the current enterprise ecosystem. Thereby, it helps an enterprise solution suite evolve with time as per the needs of the enterprise, its users and market demands.
Let us now look at the key challenges involved in building such transformative enterprise mobile solutions.
The key challenges
One of the central challenges is that of ensuring data security. Most of the enterprise data accessed from mobile devices makes its way through untrusted networks and often resides on untrusted BYOD devices, along with a mix of personal and professional data.
Another challenge is that the enterprise data to be accessed from mobile devices usually includes a variety of data sources at the backend, which may involve integrating standard data sources such as Salesforce, SAP and others. Or even integration of custom data sources.
Further, integration with the current enterprise ecosystem, including cloud services leveraged for computing or storage purposes as well as third party solutions such as enterprise mobility management, is crucial for making the solution work smoothly in the current set-up.
Another challenge is to build and test solutions for an ever-evolving and dense device portfolio with a variety of device platforms, device models and form factors to be targeted.
Inspite of strategising and huge efforts invested in building an efficient well-integrated mobile solution, ensuring user adoption and acceptance for it is no easy task. User experience, including usability, is a vital factor impacting adoption, specially for mobility solutions.
Further, life cycle management of the solution is a major challenge considering the scale of target platforms, devices and apps, with the further complexity of supporting multiple OS versions together with multiple app versions.
One more key challenge is policy management, reporting and administration. The organisations need to be able to report enterprise-wide on everything users have done with valuable content, and integrate personal devices effectively into existing enterprise compliance solutions. They also need the ability to simply provision and on-board users and manage their environments to suit their business groups needs and policies.
Finally, the enterprise mobile solution has to be dynamic enough to analyse, learn and evolve with time to better suit the users needs.
So, is there a simple and quick solution to these challenges? The answer is yes.
The solution MADP and EMM
There are two types of solutions that work together to address all the challenges to building a secure and manageable enterprise mobile solution. These are mobile application development platforms, a.k.a. MADP, and enterprise mobility management solutions or EMM.
MADP empowers cross-platform mobile app development for enterprise apps to address platform diversity and ensure that they integrate well with the existing enterprise ecosystem. It helps to get modular access to heterogeneous data sources, and all this along with effective handling of the app life cycle.
EMM focuses on securing data at rest and data on the move for enterprises. It also provides remote manageability for device, app and content. It has analytics provision too, thereby helping in identifying and addressing low user adoption.
Lets take a closer look at both these solutions.

Mobile Application Development Platforms (MADP)
According to Gartner, A MADP enables an enterprise to design, develop, test, deploy, distribute, analyse and manage a portfolio of cross-platform mobile apps on a range of devices running Android and iOS, and to address the requirements of diverse use cases including external-facing and internal-facing scenarios.
There are generic MADPs available in the market as products or offered by service providers in the form of white-labelled solutions. Whether to use a generic MADP or opt for a custom one largely depends on the complexity of the enterprises ecosystem, its time-to-market needs, security concerns, and customisation requirements.
The MADP advantage
MADP brings in excellent support for cross-platform mobile app development. This enables the developer to code once and generate multiple apps targeting different platforms as per business needs.
Next, MADP helps to solve the complexity of integrating heterogeneous data sources by providing out-of-the-box integration with standard data sources like Siebel, Salesforce, Postgres, etc. It also supports custom components to integrate with legacy and custom data sources.
Further, MADPs support standard cloud services and third party tools like enterprise mobility management (EMM) solutions. Enterprises may opt for standard or custom solutions for these too.
Finally, these platforms can enable employees to build, test, distribute, manage and update apps more rapidly.
Definitely, if youre going to invest in enterprise mobile solutions, then you need to seriously consider investing in a MADP solution, whether standard or custom.
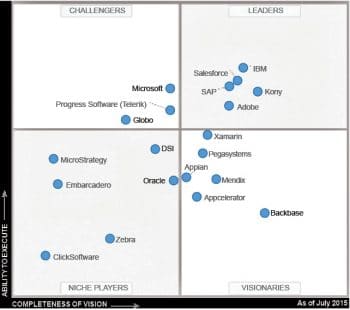
You can see Gartners Magic Quadrant for MADPs, July 2015, in Figure 1.
It is evident that the MADP market continues to mature, moving away from the tech-centric position of the past towards a more business-aligned approach, expanding support for the app development life cycle and offering more robust and scalable capabilities.
Depending on an enterprises needs, a vendor in any quadrant could be the best for an enterprise. Some enterprises may prefer custom MADP to address specific concerns related to vendor lock-in, the nature of the solution, security, roadmap demands, long-term costs, etc.
Enterprise Mobility Management (EMM)
Gartner has defined the EMM space as: Enterprise mobility management (EMM) suites consist of policy and configuration management tools and a management overlay for applications and content intended for mobile devices based on smartphone OSs. They are an evolution from the previous generation of MDM (mobile device management) products that lacked application and content management. IT organisations and service providers use EMM suites to deliver IT support to mobile end users and to maintain security policies.
Broadly speaking, there are three major categories of EMM solutions, namely: mobile device management (MDM), mobile application management (MAM) and mobile content management (MCM).
An MDM solution provides for device level management functionality. For instance, a company may want to restrict an employee to using a corporate-owned device to connect to a network through the company Wi-Fi only. The features of an MDM solution are heavily dependent on the support provided by the target device platforms. The more manageability a platform provides, the better the control that an MDM solution will have on those devices.
Some policies typically used under MDM are passcode enablement, Wi-Fi restriction, application whitelisting, mandated VPN, storage encryption, etc.
MAM focuses on securing corporate data from possible unauthorised access and misuse. Typically, an application management solution supports app level policies like blocking screen capture, copying of screen data, offline data encryption, etc, to ensure that the corporate data remains sandboxed and protected.
MCM takes care of securing the corporate content accessed and shared on the devices in the form of files. It provides the users a way to access, store and view documents from enterprise content repositories while letting the administrator establish controls to protect this content from unauthorised and unsafe distribution.
Some controls usually deployed under this category include document encryption, access control rules on sharing, a file sync policy, etc.
Some commercial EMM suites even provide for add-ons related to network management for example, secure apps for browser and personal information management.
You can see the Gartner Magic Quadrant for Enterprise Mobility Management 2015 in Figure 2. There are many EMM solutions out there, ranging from cloud-based to site-based deployment options. While the SaaS based model is becoming the preferred choice in the industry, the EMM focal point is gradually shifting to data and unified endpoint management.
Surely, EMM is becoming necessary for any organisation that manages more than a handful of mobile devices. Assessing your companys needs and accordingly choosing the right EMM solution is the key to achieving the expected return on investment (ROI).
Building mobile applications for enterprises requires a different level of understanding and work, as compared to consumer mobile applications. The enterprise mobile solution not only has to stand out in terms of user experience, but also has to integrate well with the existing enterprise set-up, and needs to ensure security and manageability of the data leaving the enterprise premises.
Some of the recommended open source tools and technologies that can be leveraged for building robust enterprise mobile solutions are: OpenStack for IaaS, Cordova for cross-platform development, Robotium and Selenium for test automation, Robolectric and Mockito for mobile app unit testing, etc.
By leveraging the recommended solutions, an enterprise can achieve both secure and manageable solutions that are capable of transforming how its business processes work, in a time-efficient and cost-effective manner.










































































This was a refreshing post that highlighted some areas I had not though about.
https://www.wedigtech.com
thanks for sharing building mobility solution for enterprices
Thanks for sharing the awesome content which gave more ideas on MADP. Happy Sharing.
Thanks, that is the clearest and most helpful article I have ever found on the net!
Its great post, thanks for sharing it