Samba is an open source network file system. It allows access to shared resources across the different OSs such as UNIX, Linux, IBM System 390, OpenVMS, etc. It is an open source implementation of Microsofts SMB (Server Message Block)/CIFS (Common Internet File System) protocol.
The main components of Samba
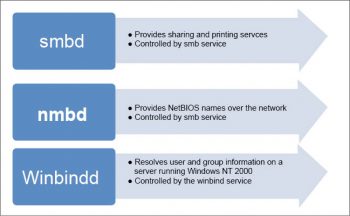
Samba is made of three daemons (smbd, nmbd and winbindd). There are two services (smb and winbind) that control the behaviour of daemons.
- smbd: The server message block daemon provides sharing and printing services over the network. It also controls resource locking, user authentication and data sharing through the SMB protocol. The Samba server listens for SMB traffic on the default TCP ports, 139 and 445.
The smb service controls the behaviour of the smbd daemon. - nmbd: This provides NetBIOS names over the network. It allows the browsing protocols to make up the Windows Network Neighborhood view. The Samba server listens for NMB traffic on the default UDP port 137. The smb service also controls the behaviour of the nmbd daemon.
- winbindd: This resolves user and group information on a server running Windows NT 2000 or Windows Server 2003. It renders Windows user/group information in a format that is understandable by UNIX platforms. A Microsoft RPC call, the name service switch (NSS), and pluggable authentication modules (PAM) allow this daemon to achieve this. This allows Windows NT domain users to access a UNIX machine as UNIX users. The winbind service controls the behaviour of the winbindd daemon. It doesnt require the smb service to be started. It is a client side service, which is used to connect to Windows users.
Samba also contains several important files. - smb.conf: This basic configuration file can be edited directly with a text editor or via a utility program like SWAT or Webmin.
- smbpasswd: This contains the names of users to which smbd will refer when it is time to enforce user-level access control.
- smbusers: This provides the names of Sambas administrators and of users with specialised Samba access.
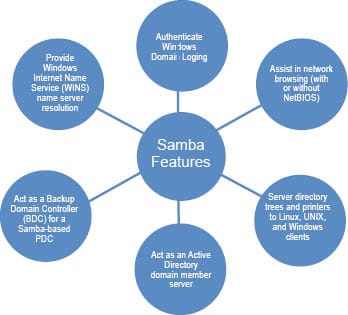
Sambas features
The primary features of Samba are shown in Figure 2.The other features are:
- Establishes shares on UNIX that are accessible to Windows users
- Shares printers
- Creates a naming scheme so one can use user-friendly names rather than IP addresses
- Makes UNIX a Windows Internet Naming Service (WINS) server
Why use Samba?
Here are a few reasons:
- Samba easily replaces a Windows NT Samba file/print server.
- It offers more stability/performance compared to Windows NT.
- It allows interoperability between UNIX and Windows workstations.
- It can serve as a Windows primary domain controller.
- Samba can serve as a highly stable WINS server.
- It can be used to stabilise Windows browsing services.
Installation and configuration
Samba installation
To install Samba on a Linux machine, use the following command:
yum -y install samba
To create a new Samba user (the new Samba user must exist on the Linux machine as a user), use the following command:
smbpasswd -a <username>
For example, to add the user max, execute the command given below:
smbpasswd -a max
To create a Samba users (smbgrp) group, execute the following command:
groupaddsmbgrp
To add a user into a group, use the command given below:
usermod -G smbusersmax
Samba configuration
The smb.conf file stores all the configurations for Samba. It provides runtime configuration information for the Samba programs. It determines which system resources you can share with the outside world and what restrictions you wish to place on them. The file consists of sections and parameters. The name of the section must be enclosed in square brackets. Each section continues until the next one begins.
Each section of the file starts with a section header such as [global], [homes], [printers], etc.
The [global] section has the variables to define sharing for all resources.
The [homes] section allows remote users to access their (and only their) home directory on the local (Linux) machine. That is, users can access their share from Windows machines and they will have access to their personal home directories.
The [printers] section works the same as the [homes] section, but for printers.
If you change this configuration file, the changes do not apply until you restart the Samba daemon with the command service smb restart.
To view the status of the Samba daemon, use the following command:
/sbin/service smb status
To start the daemon, use the following command:
/sbin/service smb start
To stop the daemon, use the following command:
/sbin/service smb stop
To start the smb service at boot time, use the following command:
/sbin/chkconfig --level 345 smb on
Access management using Samba
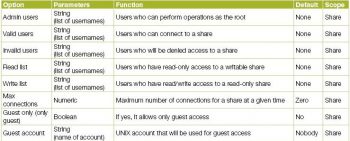
Table 1 gives the access control options.
Table 2 gives the username options
The authentication of clients is shown in Table 3
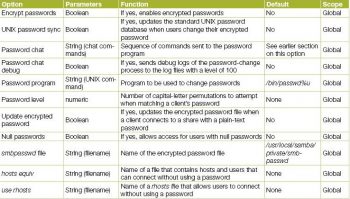
The password configuration options are listed in Table 4
Samba server types and security modes
There are three different types of servers available:
- Domain controller
• Primary domain controller (PDC)
• Backup domain controller (BDC)
• ADS domain controller - Domain member server
• Active directory domain server
• NT4 style domain server - Standalone server
There are two types of security modes available for Samba: share-level and user-level, known as security levels.
Share-level security: This can be implemented in only one way. With share-level security, the server expects a password for each share. It is not dependent on a particular user name.
In smb.conf, the security=share directive that sets share-level security is:
[GLOBAL] security = share
User-level security: This is the default setting for Samba. It is used by Samba, even if the security = user directive is not listed in the smb.conf file. Once the server accepts the user name/password, the user can then access multiple shares without entering the password for each instance.
In smb.conf, the security = user directive that sets user-level security is:
[GLOBAL] security = user
There are different implementations of user level security (see Figure 3).
Domain security mode: In this mode, the Samba server has a domain security trust account, which ensures all authentication requests are handled by domain controllers.
It can be achieved by using the following directives in smb.conf:
[GLOBAL] ... security = domain workgroup = MARKETING
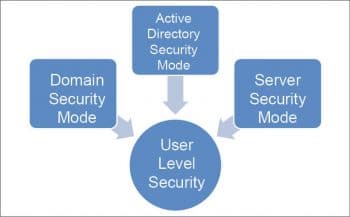
Active directory security mode: In the active directory environment, this mode is used to join as a native active directory member. The Samba server can join an ADS using Kerberos, even if a security policy restricts the use of NT-compatible authentication protocols.
In smb.conf, this can be achieved by using the following directives:
[GLOBAL] ... security = ADS realm = test.COM password server = kerberos.test.com
Server security mode: This is used when Samba is not capable of acting as a domain member server. In smb.conf, this mode is achieved by using the following directives:
[GLOBAL] ... encrypt passwords = Yes security = server password server = pwd
References
[1] https://www.samba.org/samba/
[2] https://docs.fedoraproject.org/en-US/Fedora/12/html/Deployment_Guide/ch-samba.html#samba-rgs-overview
[3] http://www.fredshack.com/docs/samba.html
[4] https://access.redhat.com/documentation/en-US/Red_Hat_Enterprise_Linux/5/html/Deployment_Guide/ch-samba.html
[5] https://help.ubuntu.com/lts/serverguide/samba-fileserver.html
[6] http://www.linuxtopia.org/online_books/network_administration_guides/samba_reference_guide/index.html