This is the second part of the blog series, ‘IoT Constrained Node Networks’. Reading the first part,‘ An Introduction to IoT Constrained Node Networks’, which was carried in the November 2019 issue of OSFY, will ensure a better understanding of this article.
This blog provides an overview of cyber security standards, tells how to use the NIST cyber security framework, and presents some guidelines to secure data in IoT constrained node networks.
Constrained node networks: Cyber security challenges
Constrained node networks face many challenges like mobility, reliability, scalability, management, availability, interoperability and cyber security. And of all these challenges, cyber security is the most critical. Among all the aspects of it, securing data is very important as it determines both the confidentiality and integrity in the CIA (confidentiality, integrity and availability) triad. Conventional data security methods cannot be followed for constrained node networks because of resource constraints. The objective of this blog is to present the guidelines to securing data in constrained node networks in an IoT system.
Cyber security standards and the associated problems
There are various standards available to implement mechanisms for securing data. It is always good to follow these standards rather than to proceed with one’s own custom solution, since it requires an enormous effort to understand the standards and select an appropriate one.
The list below covers a majority of the security standards applicable for embedded software development and its standard definitions:
- Institute of Electrical and Electronic Engineers (IEEE) – The PHY and data link layer standards
- Internet Engineering Task Force (IETF) – Networking protocols from Layer 3 and above
- International Standard Organization (ISO) – Defines standards for many domains
- International Electrotechnical Commission (IEC) – Electrical and electronic products
- ISO/IEC 27000 family of standards – Jointly defined by ISO and IEC, these are information security management system (ISMS) standards
- International Society of Automation (ISA) – Defines standards for automation
- ISA Security Compliance Institute (ISCI) or isasecure – A part of the ISA group, this defines standards for industrial automation control systems.
It provides the following certifications in alignment with IEC-62443:
- EDSA – Embedded Device Security Assurance
- SSA – System Security Assurance
- SDLA – Security Development Lifecycle Assurance
viii. IEC-62443 or ISA-99 – Security of Industrial Control System (ICS) networks. This standard was developed by the International Society of Automation (ISA) and taken over by IEC for further development.
The NIST framework: A single solution to ensure security?
The National Institute of Standards and Technology (NIST) is a non-regulatory agency of the United States Department of Commerce. One of the objectives of NIST is to help organisations to better understand and improve how they manage cyber security risks by proposing security guidelines. They have released a cyber security framework document [see Reference 6] which covers all aspects of the subject — security functions, categories, sub-categories and the standards associated with them.
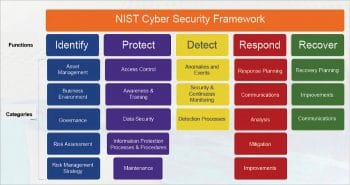
The framework defines five major functions as listed below (Figure 1):
- Identify: To identify what needs to be protected, such as systems, assets, data and capabilities.
- Protect: Implement appropriate safeguards to ensure delivery of critical infrastructure services.
- Detect: Implement appropriate activities to identify the occurrence of a security event.
- Respond: Implement the appropriate activities when facing a detected security event.
- Recover: Implement the appropriate activities to restore the affected services.
Organisations need to go through all the sub-categories and references for developing the security requirements, which should also align with their business goals. This careful analysis should result in a set of security requirements that is called a profile.
How to use NIST for data security during IoT product development
NIST has created a profile for IoT systems and released a guidelines document [see Reference 7] which mandates the devices’ capabilities like networking protocols and cryptographic support to achieve data security.
The usual phases of IoT product development, during which the roles of cryptography and networking protocols are involved, are shown in Figure 2.

Processor selection
Cryptographic algorithms need significant processing capabilities, otherwise it affects performance. The cryptographic operations should be offloaded to hardware accelerators to improve the performance. The selected processor should have this hardware acceleration support.
Firmware selection
The firmware that runs in the constrained nodes should support running cryptographic algorithms and use the hardware acceleration for cryptography. There are some networking protocols that are specifically designed to support constrained nodes. For example, firmware are openthread, contiki, zigbee stack etc.
Application development
During application development, choose a relevant cipher suite and its library implementation to ensure data security.
A cipher suite is a set of various algorithms that help secure a network connection. There are several cipher suites that contain different combinations of algorithms. The kinds of algorithms that cipher suites usually include are listed below:
- Key agreement – To securely exchange keys between devices; e.g., RSA, Diffie-Hellman
- Encryption – To encrypt the data transfer; e.g., AES, DES, RC4
- Message authentication – To provide data integrity checks; e.g., SHA, HMAC
- Signatures – To authenticate the client or server; e.g., DSA, ECDSA
To know more about various cipher suites and libraries, check out references 2, 3, 4 and 5 listed at the end of this article. Selection of the relevant cipher suite ensures confidentiality and integrity of the data transfer.
The required cipher suites are generally present as part of the selected firmware. After the cipher suite is selected, the next step is to extract the requirements and best practices related to data security from the guidance documents listed in reference 7, and implement them.
Provisioning of keys
Constrained nodes need preconfigured keys, so that cipher suites use these keys to secure the communication in the data link and transport layers. When the nodes are deployed in the production environment, these keys should be provisioned.
In conventional systems, the focus is more on securing the transport layer, as the medium is wired and the switch/router takes care of the physical security of the data link layer. But in constrained node networks, the focus should be more on the data link layer as the medium is wireless and anybody can access this medium. Since the security is needed at Layer 2 itself, the only way to achieve this is by using the pre-shared key (psk).
The IoT use cases that require data security are listed below.
- Network joining – The IoT device joins the network.
- Data transfer – The IoT device transfers data.
- Command – The IoT device receives commands from other devices and processes them.
- Secure storage – The IoT device stores its ID and other data.
- Network leaving – The IoT device leaves the network.
This article explored the security approach by using the NIST framework which ensures end to end security coverage. The IoT profile generated out of the NIST framework is used as a reference to ensure data security in IoT constrained node networks. The key task is to identify the security requirements from the NIST recommended guidelines. According to Wikipedia, “A 2016 US security framework adoption study reported that in 70 per cent of the surveyed organisations, the NIST cyber security framework is the most popular best practice for information technology (IT) computer security, but many note that it requires significant investment.”












































































