Nowadays, there is considerable amount of confusion among industry professionals and researchers regarding the significant differences between vulnerability scanning and penetration testing, as the two phrases are commonly interchanged. However, their exact technical meanings and implications are very different. A vulnerability assessment simply identifies and reports noted vulnerabilities, whereas penetration testing attempts to exploit the vulnerabilities to determine whether unauthorised access or malicious activity is possible. This article features the top five open source automated penetration testing tools.
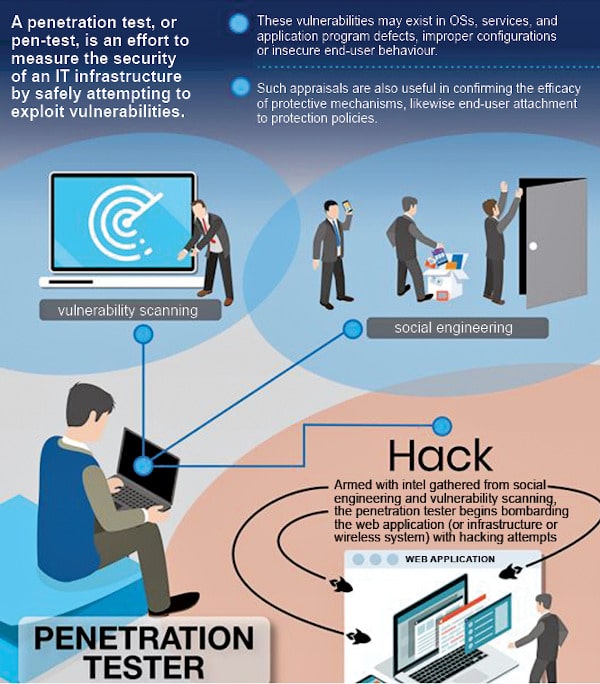
Penetration testing is a simulated cyber attack that professional ethical hackers launch to break into corporate networks to find weaknesses before attackers do. This process uses the tools and techniques available to malicious hackers. It can be automated with software applications or performed manually. In a nutshell, the process involves gathering information about the target before the test, identifying possible entry points, attempting to break in—either virtually or for real and reporting back the findings. The main objective of penetration testing is to identify security weaknesses. It can also be used to test an organisation’s security policy, its adherence to compliance requirements, its employees’ security awareness, and its ability to identify and respond to security incidents.
A penetration test can also highlight weaknesses in a company’s security policies. For instance, although an enterprise’s security policy focuses on preventing and detecting an attack on its systems, that policy may not include a process to expel a hacker. The reports generated by a penetration test provide the feedback needed by an organisation to prioritise the investments it plans to make in its security and for its application developers to create more secure apps.
The penetration testing process can be divided into the following five stages:
- Planning and reconnaissance
- Scanning
- Gaining access
- Maintaining access
- Analysis and WAF (Web application firewall) configuration
Planning and reconnaissance: This is the first stage of penetration testing, which involves the following activities:
- Defining the scope and goals of a test, including the system to be addressed and testing methods to be used.
- Gathering all information with regard to the network, domain names and mail servers to understand how the target works and detect vulnerabilities.
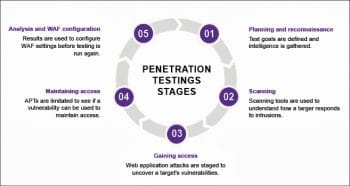
Scanning: This is the second stage of penetration testing to understand how the target application will respond to various intrusion attempts, and includes the following:
- Static analysis, which is a detailed inspection of application code to understand its behaviour. For this analysis, there are tools available to scan the entire code in a single way.
- Dynamic analysis is the detailed inspection of running application code, which is done to understand the real-time performance of the app.
Gaining access: During this stage, various attacks are performed, like SQL injection, backdoors and XSS, in order to uncover various vulnerabilities. In this stage, testers attempt to intercept the traffic, steal data and then analyse the results to assess the damage, if any.
Maintaining access: In this stage, various advanced persistent threats are performed by the pen testers to achieve a persistent presence in the system, and to uncover any hidden channels that could be used to steal an organisation’s sensitive data.
Analysis: This stage is the final outcome of the penetration test, highlighting the vulnerabilities and backdoors in the system as well as the hidden sensitive points, which could be catastrophic.
Types of penetration testing
- White box pen test: In this case, the hacker will be provided with some information ahead of time, regarding the target company’s security information.
- Black box pen test: Also known as a ‘blind’ test, this is a test for which the hacker is given no background information besides the name of the target company.
- Covert pen test: Also known as a ‘double-blind’ pen test, in this situation, almost no one in the company is aware that the pen test is happening, including the IT and security professionals who will be responding to the attack. For covert tests, it is especially important for the hacker to have the scope and other details of the test in writing, beforehand, to avoid any problems with law enforcement agencies, later on.
- External pen test: In this case, the ethical hacker goes up against the company’s external-facing technology, such as its website and external network servers. In some cases, the hacker may not even be allowed to enter the company’s building. This can mean conducting the attack from a remote location or carrying out the test from a truck or van parked nearby.
- Internal pen test: In this case, the ethical hacker performs the test from the company’s internal network. This kind of test is useful in determining how much damage a disgruntled employee can cause from behind the company’s firewall.
Penetration testing methodologies and standards
The following five are regarded as the top penetration testing methodologies and standards today.
OSSTMM (Open Source Security Testing Methodology Manual)
This is a peer-reviewed methodology for security testing, maintained by the Institute for Security and Open Methodologies (ISECOM). The manual is updated every six months or so, to remain relevant to the current state of security testing. ISECOM says its main objective with the OSSTMM is to provide a scientific process for the accurate characterisation of operation security that can be used for penetration testing, ethical hacking, and other security testing. ISECOM focuses on verified facts to make sure that organisations using the OSSTMM for their own penetration testing methodologies can know they are making fact based decisions.
This framework contains a comprehensive guide for testers to identify security vulnerabilities within a network (and its components) from various potential angles of attack. This methodology relies on the tester’s in-depth knowledge and experience, as well as human intelligence, to interpret the identified vulnerabilities and their potential impact within the network. OSSTMM provides five channels to guide organisations to fully extend their security processes and determine how well they actually function. The five channels include:
- Human security: How securely humans within an organisation interact and communicate is evaluated operationally, as a means of testing.
- Physical security: OSSTMM tests physical security, which is defined as any tangible element of security that takes physical effort to operate.
- Wireless communications: Electronic communications, signals and emanations are all considered wireless communications that are part of the operational security testing.
- Telecommunications: Whether a telecommunications network is digital or analogue, any communication conducted over the telephone or network lines is tested in OSSTMM.
- Data networks: This includes the security testing of electronic systems and data networks that are used for communication or interaction via cable and wired network lines.
OWASP (Open Web Application Security Project)
This is the most recognised standard in the industry. This framework provides a methodology for application penetration testing that can not only identify vulnerabilities commonly found within Web and mobile applications, but also find the complicated logic flaws that stem from unsafe development practices.
With the help of this methodology, organisations are better equipped to secure their applications – Web and mobile alike – from common mistakes that can have a potentially critical impact on their business. Organisations looking to develop new Web and mobile applications should also consider incorporating this standard during their development phase to avoid introducing common security flaws.
NIST (National Institute of Standards and Technology)
This provides a manual that is best suited to improve the overall cyber security of an organisation. The most recent version, NIST 1.1, places more emphasis on critical infrastructure cyber security. Complying with the NIST framework is often a regulatory requirement for various American providers and business partners. NIST discusses penetration testing in SP800-115. The NIST methodology is less exhaustive than OSSTMM.
The Best Open Source Automated Penetration Testing Tools
This penetration testing execution standard consists of seven main sections. These cover everything related to a penetration test – beginning with the initial communication and reasoning behind a pen test, right through to the intelligence gathering and threat modelling phases (when testers are working behind the scenes in order to get a better understanding of the tested organisation). PTES also covers vulnerability research, exploitation and post exploitation (when the technical expertise of the testers comes into play and combines with their understanding of the business of the target organisation). Finally, PTES covers the reporting, which captures the entire process, in a manner that makes sense to the customer and provides the most value to it. The following are the main sections defined by the standard, as the basis for penetration testing execution:
- Pre-engagement interactions
- Intelligence gathering
- Threat modelling
- Vulnerability analysis
- Exploitation
- Post exploitation
- Reporting
ISSAF (Information System Security Assessment Framework)
The ISSAF standard contains an even more structured and specialised approach to penetration testing than the previous standard. These sets of standards enable a tester to meticulously plan and document every step of the penetration testing procedure, from planning and assessment, to reporting and destroying artefacts. This standard caters for all steps of the process. Pen testers who use a combination of different tools find ISSAF especially crucial as they can tie each step to a particular tool. The assessment section, which is more detailed, governs a considerable part of the procedure. For each vulnerable area of your system, ISSAF offers some complementary information, various vectors of attack, as well as possible results when a vulnerability is exploited.
ISSAF breaks the pen testing project into three phases:
- Planning and preparation
- Assessment
- Reporting, clean-up and destroying artefacts
Automated penetration testing
Automated penetration testing plays an important role in a security analyst’s arsenal. As part of an organisation’s overall security strategy, automated penetration tests quickly evaluate the existing security maturity of its technical infrastructure. However, one cannot solely rely on automated penetration tests, and they must be monitored by the internal security team.
The goal behind penetration testing is to assume a hacker-like mindset, so that real-life attacks are simulated using the tools that are most likely to be used by the attackers. Conducting these tests is a time-consuming activity, and needs to be performed by properly trained individuals to get the best results.
In order to cut down on the time element, many organisations aim for automating certain parts of the process. Though the penetration tests are still monitored by a skilled security analyst or a team of analysts, many steps of a penetration test can be easily automated. For example, manually running scans on each system will take up a significant amount of time, while these steps can be easily automated by using a vulnerability scanner to scan multiple systems at once. On similar lines, automated exploit tools can be used to perform an attack.
Automated penetration testing tools have multiple key benefits for an organisation. To start with, automated scans can be performed more quickly than manual scans, and hence, the speed of detecting new vulnerabilities also increases. Second, a security analyst will manually scan and test systems, one by one, which becomes a tedious process. Automated tools can cover a large number of systems for thousands of vulnerabilities. Third, with automated tools performing most of the basic parts of penetration testing, your internal team is not overloaded with monotonous work. It can instead focus its time on looking out for advanced attacks. Fourth, automated penetration testing tools can also play a major role in the compliance of certain standards or frameworks.
A number of commercial and open source automated penetration testing tools are available. In this article, we focus on the top five.
Metasploit
Metasploit was created by H.D. Moore in 2003 as a portable network tool using Perl. By 2007, the Metasploit Framework had been completely rewritten in Ruby. On October 21, 2009, the Metasploit Project announced that it had been acquired by Rapid7, a security company that provides unified vulnerability management solutions.
Metasploit can be used to test the vulnerability of computer systems or to break into remote systems. Like many information security tools, Metasploit can be used for both legitimate and unauthorised activities. Since the acquisition of the Metasploit Framework, Rapid7 has added two open core proprietary editions called Metasploit Express and Metasploit Pro.
The basic steps for exploiting a system using the Metasploit Framework include:
- Choosing and configuring an exploit for a specific target. Metasploit has over 300 exploits for various operating systems.
- Checking whether the intended target system is vulnerable to the chosen exploit.
- Choosing and configuring a payload. A payload is essentially code that will be executed once the targeted system gets compromised — for example, a remote shell.
- Executing the exploit.
Metasploit contains a fully loaded pen testing toolkit comprising the following.
- Exploits: An exploit is a method by which the attacker takes advantage of a flaw within a system, service, application, etc. Exploits are always accompanied by payloads.
- Payload: This is the piece of code that is run in the successfully exploited system.
- Auxiliary: This provides additional functionality such as fuzzing, DoS attacks, scanning and recon, but it doesn’t inject a payload like exploits.
- Encoders: This obfuscates modules to avoid detection by a protection mechanism such as an antivirus or a firewall (e.g., backdoor creation).
- Nops: This prevents the payload from crashing while using jump statements in its shellcode.
- Post-exploitation: A post-exploitation module enables you to gather more information or to gain further access to an exploited target system.
- Shellcode: This is a set of instructions that an exploit uses as the payload.
Main features of the Metasploit Framework:
- It is a penetration testing framework with more than 1800 exploits.
- It has 1000+ auxiliary modules, 300+ post-exploitation modules, 500+payloads, as well as a lot of encoders and nops.
- Metasploit has a meterpreter module, which is an advanced, dynamically extensible payload.
- Command-line interface (mfsconsole), manual exploitation, manual credentials, brute forcing, and much more.
Features of Metasploit Pro:
- Web interface and Metasploit Pro console (to create and manage projects, scan and enumerate hosts, import and export data, configure and run modules, run automated exploits, view information about hosts, collect evidence from exploited systems, etc).
- Team collaboration capabilities (to share host data, view collected evidence, create host notes, divide pen testing into multiple parts, assign members a specific network segment to test, etc).
- It runs the following services: PostgreSQL (database), Ruby on Rails (Metasploit Pro Web Interface), Metasploit service, bootstraps Rails, the Metasploit Framework, and the Metasploit RPC server.
- Penetration testing workflow involves smaller and more manageable tasks and database exploits through a Web based user interface.
- Web app testing for OWASP Top 10 vulnerabilities, phishing awareness management and spear phishing, and much more.
Latest version: 5.0.0
Official website: https://www.metasploit.com/
Sn1per
Sn1per is an automated scanner that can automate the process of collecting data for exploration and penetration testing. It uses such well-known tools as amap, arachni, amap, cisco-torch, dnsenum, enum4linux, golismero, hydra, metasploit-framework, nbtscan, nmap smtp-user-enum, sqlmap, sslscan, theharvester, w3af, wapiti, whatweb, whois, nikto and wpscan.d during a penetration test to enumerate and scan for vulnerabilities.
Sn1per modes:
- REPORT: Outputs all results to text in the loot directory for later reference. To enable reporting, append ‘report’ to any sn1per mode or command.
- STEALTH: Quickly enumerates single targets using mostly non-intrusive scans to avoid WAF/IPS blocking.
- DISCOVER: Parses all hosts on a subnet/CIDR (i.e., 192.168.0.0/16) and initiates a sn1per scan against each host. Useful for internal network scans.
- PORT: Scans a specific port for vulnerabilities. Reporting is not currently available in this mode.
- FULLPORTONLY: Performs a full detailed port scan and saves results to XML.
- WEB: Adds fully automatic Web application scans to the results (port 80/tcp and 443/tcp only). Ideal for Web applications but may increase scan time significantly.
- NOBRUTE: Launches a full scan against a target host/domain without brute forcing services.
- AIRSTRIKE: Quickly enumerates open ports/services on multiple hosts and performs basic fingerprinting. To use it, specify the full location of the file which contains all hosts, IPs that need to be scanned and run ./sn1per /full/path/to/targets.txt airstrike to begin scanning.
- NUKE: Launches full audit of multiple hosts specified in the text file of choice. Usage example: ./sniper /pentest/loot/targets.txt nuke.
- LOOT: Automatically organises and displays loot folder in your browser and opens Metasploit Pro and Zenmap GUI with all port scan results. To run, type ‘sniper loot’.
Features:
- Automatically collects basic recon data (i.e., whois, ping, DNS, etc.)
- Automatically launches Google hacking queries against a target domain
- Automatically enumerates open ports
- Automatically brute forces sub-domains and DNS information
- Automatically checks for sub-domain hijacking
- Automatically runs targeted NMap scripts against open ports
- Automatically runs targeted Metasploit scan and exploit modules
- Automatically scans all Web applications for common vulnerabilities
- Automatically brute forces all open services
- Automatically exploits remote hosts to gain remote shell access
- Performs high level enumeration of multiple hosts
- Auto-pwn added for Metasploitable, ShellShock, MS08-067 and Default Tomcat Creds
- Automatically integrates with Metasploit Pro, MSFConsole and Zenmap for reporting
- Creates individual workspaces to store all scan output
Latest version: 8.2
Official website: https://github.com/1N3/Sn1per/releases
Nettacker
OWASP Nettacker is an open source penetration testing framework with auto-information gathering and vulnerability assessment features. It eventually generates a report of networks, including services, bugs, vulnerabilities, misconfigurations and other information such as running services, open ports, server information, reverse IP lookup, DNS information, sub-domain records, CMS information, plugins, themes, directories, etc. The most common vulnerabilities that can be detected with OWASP Nettacker include those found via brute-force attacks, ProFTPD (FTP server) vulnerabilities, expired certificate issues, weak signature algorithms, cross-site scripting, header misconfigurations, server version-specific vulnerabilities, clickjacking, heartbleed attacks, CCS injection, and pma (PhpMyAdmin) attacks.
The brute-force scan option assesses the security of different network protocols like FTP, SSH, telnet, HTTP, NTLM, and xmlrpc protocols. The ProFTPD-related scanning covers vulnerabilities like bypass SQL protection, CPU consumption, directory traversal, heap overflow, integer overflow, restriction bypass, and memory leak vulnerability detection.
OWASP Nettacker is a Python based project that is tested on different operating systems including Linux, MacOS and Windows OS. The framework is compatible with both Python versions (2 and 3). OWASP Nettacker depends on the different packages in the requirements.txt file that are included in the framework’s source code directory.
Features:
- IoT scanner, network service analysis and services brute-force testing
- Services vulnerability testing, information gathering, fuzzing, HTTP/HTTPS crawling with HTML/text outputs
- Python multi-thread and multi-process network information gathering vulnerability scanner
- Service and device detection (SCADA, restricted areas, routers, HTTP servers, logins and authentications, none-indexed HTTP, paradox system, cameras, firewalls, UTM, WebMails, VPN, RDP, SSH, FTP, TELNET services, proxy servers and many devices like Juniper, Cisco, switches and much more… )
Latest version: 0.0.1
Official website: https://owasp.org/www-project-nettacker/
Jok3r
Jok3r is a Python3 CLI application based automated testing framework for network infrastructure and Web black security tests. It quickly identifies the ‘low-hanging fruit’ type of vulnerabilities on most common TCP/UDP services and other Web technologies, and combines open source tools in a smart way.
Features:
- Over 50 open source tools and all applications packed in a Docker image running Kali OS on a Docker hub.
- Tools updatable on a single command and easy interface for addition/removal of tools.
- Targets most common TCP/UDP services (HTTP, FTP, SSH, SMB, Oracle, MS-SQL, MySQL, PostgreSQL, VNC, etc).
- Supports automatic fingerprinting (product detection) of targeted services.
- Automatically scans and/or exploits most critical vulnerabilities (e.g., RCE) on Web and application servers (e.g., JBoss, Tomcat, Weblogic, Websphere, Jenkins, etc).
- All outputs from security checks, detected credentials and vulnerabilities are stored into the database and can be accessed easily.
- Automatically runs vulnerability scanners on most common CMS (WordPress, Drupal, Joomla, etc).
Latest version: 3.0
Official website: https://www.jok3r-framework.com/
Legion
Legion, a fork of SECFORCE’s Sparta, is an open source, easy-to-use, super-extensible and semi-automated network penetration testing framework that aids in the discovery, reconnaissance and exploitation of information systems, and is powered by 100+ auto-scheduled scripts.
Legion provides an easy-to-use graphical interface, unlike most tools mentioned here. It’s a modular framework, allowing you to add or customise functionalities. It’s another pen testing tool that’s written in Python, which means that it can also run on any system capable of running Python, i.e., it supports Windows, MacOS and Linux.
Features:
- Automatic recon and scanning with NMAP, whataweb, nikto, Vulners, Hydra, SMBenum, dirbuster, sslyzer, webslayer and more (with almost 100 auto-scheduled scripts).
- Easy-to-use graphical interface with rich context menus and panels that allow pen testers to quickly find and exploit attack vectors on hosts.
- Modular functionality allows users to easily customise Legion and automatically call their own scripts/tools.
- Highly customisable stage scanning for ninja-like IPS evasion.
- Automatic detection of CPEs (Common Platform Enumeration) and CVEs (Common Vulnerabilities and Exposures).
- Real-time autosaving of project results and tasks.
Latest version: 0.3.6b
Official website: https://govanguard.com/legion/