Penetration testing is used to determine the vulnerabilities of Web and smartphone apps. It is also called pen testing or ethical hacking, and can be carried out manually or automatically.
With the increasing dependence on online platforms, the issues and concerns of security and privacy merit attention. A number of cases associated with data breaches, hacking, data leakages, server cracking get reported every day in the global news. This creates a sense of distrust among the public towards the use of online platforms, whether via Web applications or smartphone apps. There is a need to create awareness about the diverse aspects of security and privacy, while using online platforms.
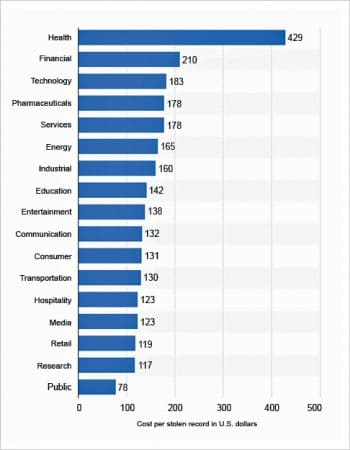
These hacking and data breach attempts actually cost organisations a lot of money, as can be seen in Figure 1 from the reports of the global data platform, Statista.
Free and open source tools for security
There is a need to secure Web and smartphone applications against malicious hackers and data breach attempts. There are a number of tools and frameworks that are widely used for penetration testing and digital forensics. These tools, when used by application developers, prevent data theft.
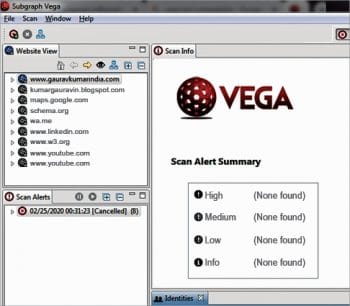
Vega (https://subgraph.com/vega/) is one of the powerful free and open source tools for penetration testing. It is used as a Web security scanner and is an effective platform for Cross Site Scripting (XSS) implementations. In addition, the test associated with SQL injection and information disclosure can be evaluated. Vega is a GUI based tool written in Java and is cross-platform. It is developed by Subgraph and is available for cyber forensic and Web penetration analytics.
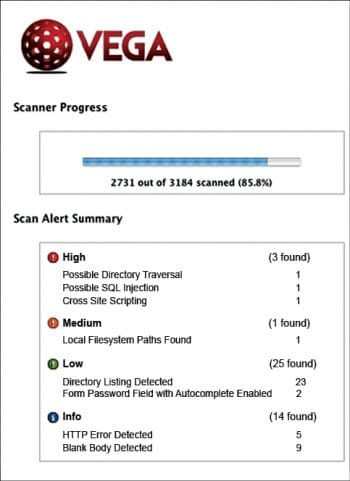
The Vega scanner presents the vulnerabilities, with the associated impact classified as either High, Medium or Low. This predicts the performance of the Web application and indicates possible security breach points.
Penetration testing and auditing Android based smartphone apps
Today, most of the Web services and applications are deployed on smartphone platforms including Android, iPhone, Blackberry, KaiOS, Symbian, Java and many others. The software applications launched for mobile platforms need to be tested rigorously against assorted assaults and vulnerability points.
Nowadays, most of the smartphone apps are available on Android operating systems. They are widely adopted by mobile phone users because of their popularity and availability as open source distributions. Installation of Android apps in the Android Application Package (APK) format requires specific permissions, which are generally ignored by Android users.
With the increasing number of smartphones and mobile applications, there is a need to check the vulnerabilities of these devices to avoid misuse and exploitation.
There are a number of cloud repositories, from where the Android APK files are downloaded:
https://apkpure.com/
https://www.apkmirror.com/
https://www.androiddrawer.com/
https://apk-dl.com/
https://en.aptoide.com/
https://androidapksfree.com/
https://www.appsapk.com/
https://apk4all.com/
…and many others.
Using the Android Asset Packaging Tool (AAPT), the permissions associated with the APK can be analysed critically so that data breach attempts and the anonymous copying of information can be avoided. In some cases, smartphone users do not download the Android app from the Google Play Store but directly download the APK from different portals. This practice can be quite dangerous; so users are advised to use advanced tools and analyse the inherent permissions before installing the app on the mobile phone.
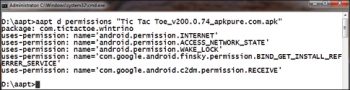
In addition, research scholars and practitioners can work on this domain of smartphone malware analysis by collecting the permissions from assorted APK files, and then training the data sets using machine learning. This will help to predict the security, privacy and data breach issues of upcoming smartphone apps.
Table 1: Popular tools for Web application testing
| Tool | URL |
| Vega | https://subgraph.com/vega/ |
| Canoo Web Test | http://webtest.canoo.com/ |
| Webrat | https://github.com/brynary/webrat |
| Watir | http://watir.com/ |
| SoapUI | https://www.soapui.org/ |
| Cucumber | https://cucumber.io/z |
| Selendroid | http://selendroid.io/ |
| Selenium | https://www.seleniumhq.org/ |
| Pylot | https://code.google.com/archive/p/pylt/downloads |
| OpenSTA | http://opensta.org/ |
| Grinder | http://grinder.sourceforge.net/ |
| Gatling | https://gatling.io/ |
| Multi-Mechanize | https://multi-mechanize.readthedocs.io/en/latest/ |
| Tsung | http://tsung.erlang-projects.org/ |
| WebLoad | https://www.radview.com/webload-download/ |
| TestNG | https://testng.org |
| Locust | https://locust.io/ |
| Capybara | https://github.com/teamcapybara/capybara |
| Apache JMeter | https://jmeter.apache.org/ |
| Appium | http://appium.io/ |
| FitNesse | http://fitnesse.org/ |
Table 2: Penetration testing and audit tools
| Tool | URL |
| AAPT | https://androidaapt.com/ |
| OWASP Zed Attack Proxy | https://www.owasp.org |
| QARK
(Quick Android Review Kit) |
https://github.com/linkedin/qark |
| Devknox | https://devknox.io/ |
| Drozer | https://labs.mwrinfosecurity.com/tools/drozer |
| MobSF
(Mobile Security Framework) |
https://github.com/MobSF/Mobile-Security-Framework-MobSF |
| Mitmproxy | https://mitmproxy.org/ |
| iMAS | https://github.com/project-imas/about |













































































