Kerberos is an open source authentication and single sign-on protocol widely used in the computing industry. This article gives a basic overview of the protocol.
In distributed systems, when clients need to access other resources in the network, they are authenticated through network protocols that have evolved over time. Security is of prime concern as distributed systems are prone to a variety of threats. There are various authentication protocols that are classified based on the underlying cryptographic algorithm used. There are two broad types of cryptographic techniques — symmetric key cryptography (private key encryption) and asymmetric key cryptography (public key encryption).
Symmetric key cryptography (private key encryption): This is when the sender and receiver of the message encrypt and decrypt the plain text message using the same key.
Asymmetric key cryptography (public key encryption): This is when a private key is kept from unauthorised users and a public key is known to everyone. Messages encrypted by the public key can be decrypted only by the corresponding private key.
Various protocols that use symmetric key cryptography include intermediate additional steps like sending nonce, using a third authentication server, one-time passwords, timestamps and a combination thereof.
Introducing Kerberos
Kerberos is a protocol based on symmetric cryptography that uses trusted third-party authentication servers. The components of the service include the following:
a) Server
b) Domain controller – Authentication servers and ticket granting servers
c) Clients – These constitute the three ‘heads’ of Kerberos (named after the watchdog of the underworld, Cerberus, in Greek mythology). They are designed to completely avoid sending passwords through non-secure networks.
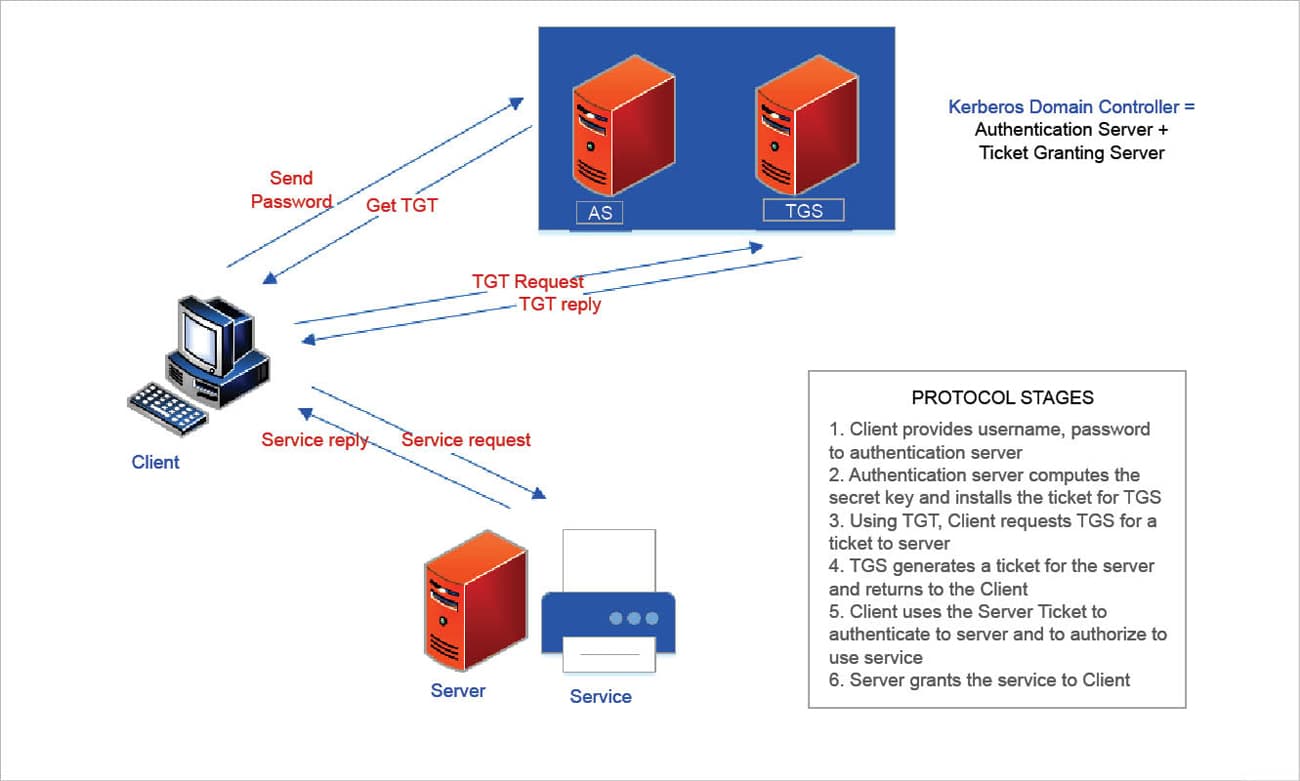
Windows Server uses Kerberos as its primary authentication mechanism. It uses tickets as the token for user verification. Tickets are digital tokens that store session keys that can be used instead of passwords to access Kerberised services. The tickets used in the Kerberos system are the ticket granting ticket and the server ticket, as shown in Figure 1. These tickets have a timestamp that indicates their expiration time. The Kerberos domain controller or the key distribution centre houses the authentication server and the ticket granting server. The secret keys of the users and services are stored in a database in the authentication server. The clients authenticate themselves to every node (or principal, in Kerberos terminology) of the system.
Advantages of Kerberos
- Kerberos is designed to work even in insecure networks. The encryption key must be compromised in order to break the underlying algorithm. The protocol against replay attacks that eavesdrop on Kerberos messages and retransmit them by embedding the IP addresses of clients in the tickets. The timestamps used in the tickets restrict the window of time for which messages can be replayed.
- The protocol against replay attacks that eavesdrop on Kerberos messages and retransmit them by embedding the IP addresses of clients in the tickets.
- The timestamps used in the tickets restrict the window of time for which messages can be replayed.
Drawbacks of Kerberos
- Kerberos has a single point of failure – the key distribution centre (KDC).So, a continuous availability of KDC zhas to be ensured.
- Since timestamps are used in Kerberos, it would be required that the clocks of all principals be synchronised.
- If the KDC infrastructure is compromised, it would mean that any attacker can impersonate a user.
Other authentication protocols and a comparison between them
One may come across very many other authentication protocols, some of which also facilitate SSO (single sign-on). A few popular ones are LDAP or Active Directory, NTLM, OAuth2, SAML, RADIUS and OpenID.
Most of these protocols differ in the way authentication is handled. Some are standards, and some are proprietary. They also differ in use cases. Kerberos, LDAP and NTLM are used more as network protocols in enterprise LANs, while SAML, OAuth2 and OpenID are used with Web applications over HTTP and the RESTful API.
A lot of research goes into formulating cryptographic algorithms to make the Internet more secure. Kerberos has been around for a long time and provides the backbone for many commercial products. It is easy to set it up in Windows or Linux systems. Recent research has provided public key cryptographic extensions to Kerberos authentication, which overcome some of its limitations, paving the way to improved scalability, security and client privacy.










































































