The Malboxes utility helps to analyse malware on virtual machines. This article explains how this tool works, with an example.
Imagine receiving good news like ‘You have won a lottery’ or ‘You have been selected to receive an award’ through an email. But the moment you open this harmless-looking mail, you realise all your files have been encrypted, and a ransom of over US$ 1,000 is being demanded to get them back. This is what happened to the victims of WanaCrypt0r, a global ransomware attack that first appeared on Friday, May 12, 2017.
It is very important to understand the nature of such malicious files. Malware analysis is similar to defusing bombs, as the goal is to deconstruct and decipher the software designed to cause harm to or spy on computer users. The program is frequently obfuscated (i.e., packed) to make analysis difficult, if not impossible.
Malware has the ability to do any or all of the following things.
- Implant payload or variants: In the field of malware, this refers to inserting a virus, worm, or Trojan designed to attack a victim’s machine.
- Obfuscate malware behaviour and code: Malware obfuscation is a technique that makes textual and binary data harder to decipher. Attackers utilise such methods to make it difficult for the antivirus to detect it, and filter less malware.
- Runtime polymorphism: This is an encryption method used for mutating malware’s static binary code in order to avoid discovery.
- Spyware: This collects information and data about the device and the user, while observing the user’s activity, without the knowledge of the user.
- Keylogging: Every user activity including emails, accessed websites, apps and keystrokes is tracked.
The need for malware analysis
Malware analysis is critical for investigating any occurrence of malware. It is carried out in two different ways — static and dynamic analysis.
Static analysis: This is a simple way to dissect any binary file (executable) without executing it.
Dynamic analysis: This involves execution of malware within the isolated environment (sandbox) that is separated from the real production environment.
Simple malware can easily be detected by using static analysis. So present day hackers use advanced techniques to obfuscate code and executables to bypass static detection techniques, making it imperative to use dynamic analysis.
If your organisation is attacked by malware, and the threat is eliminated by hiring a good security consultant, you still need to look out for the following to avoid another attack:
- Probability of rootkit or Trojan implantation in the system
- Is the threat eliminated?
- What changes did the attacker make to the system?
- How did the attacker access the backdoor to the system?
Malboxes
Malboxes is a utility that builds Windows virtual machines (VMs) without requiring any user intervention. The malware analysis tools and security settings for the VMs are set up for malware investigation. Malboxes can also be referred to as a tool designed to assist in the creation of secure and rich-featured Windows PCs for malware analysis. Not only can anyone use this tool, it even works with trial versions of Windows if you don’t have your own licence. Malboxes creates a virtual machine (VM) template for Windows 10 Enterprise evaluation and then launches a duplicate of it with the current folder shared on the VM’s desktop. It also comes with a set of tools for safe malware analysis built into its virtual machine.
Architecture of Malboxes
Malboxes wraps together the following components:
- A packer configuration
- Windows unattended installation configuration
- PowerShell recipes to disable security features (Defender, auto-updates, firewall, etc)
- A set of malware analysis focused tools installed using the Windows package manager Chocolatey
- A Vagrant file generator so that the VMs can be managed with Vagrant
Tools that come with the Malboxes VM
The following tools are installed as part of the build process.
- WinDBG: A well-known name for the Windows debugger, it offers regular updates, functionality, and online support. It has a graphical user interface (GUI) that displays the debugger output, as well as stacks and registers. It is used to examine memory dumps in both kernel and user mode.
- Complete Sysinternal suite: This suite of tools consists of a collection of Windows apps that can be downloaded for free from Microsoft Technet’s Sysinternals area. They are all portable, which means that they can be placed on a Flash drive and used from any PC, eliminating the need of installing them.
- Fiddler: A debugging proxy server tool that allows logging, analysing, and changing HTTP and HTTPS traffic between your computer and a Web server/s.
- Wireshark with NPcap (a Windows 10 compatible winpcap replacement): NPcap is a Windows version of the libpcap library that includes a packet capture driver. This library can be used by Wireshark on Windows to record live network data.
- IDA Pro remote debuggers (if IDA Pro is installed on the host): The ‘debugger server’ is the computer that runs the debugging application. To debug viruses, Trojans, and malware, the debugger client is kept as far away from the compromised computer as feasible.
The following changes are made to the guest operating system:
- Automatic updates disabled
- Windows Defender disabled
Why Malboxes?
It is important to analyse malware in a safe environment. Malboxes, with its tools, helps us do just that.
- Malboxes builds everything required in the analysis toolkit, in the following way:
1. Creates and allocates a safe environment for analysis
2. Sandboxes the system from the production environment
3. Installs behaviour and code analysis tools - Malboxes helps to overcome faulty malware analysis consequences, which can range from the leakage of internal information, products, or licences to the identification of an organisation’s IP addresses and erasure from the infected computer.
- Because Malboxes includes Chocolatey, a single command can be used to install anything from the large Chocolatey software package gallery. In the configuration file of Malboxes, you can change the default list of packages installed.
- Malboxes offers the advantage of coming with tools preloaded and may be deployed with the help of a few commands, avoiding hours of effort in installing these individually. Malboxes is built around Python 3 and supports the Windows, Mac and Linux operating systems.
Installation steps on a Windows machine
Requirements
- Python 3.3+
- Packer
- Vagrant
- VirtualBox or a vSphere/ESXi server
Minimum specs for the build machine
- At least 5GB of RAM
- VT-X extensions strongly recommended
Install VirtualBox: VirtualBox is a powerful x86 and AMD64/Intel64 virtualisation product for enterprise and home use. It is used here in order to provide a hypervisor for the Malboxes virtual machine to run on. Not only is VirtualBox an extremely rich-featured, high performance product for enterprise customers, it is also the only solution that is freely available as open source software under the terms of the GNU General Public License (GPL) version 2.
Install Git and Python3: Git is a free and open source distributed version control system designed to handle small and very large projects with speed and efficiency. It is used to clone the Malboxes project from the GitHub repository. It is easy to learn and has a tiny footprint with lightning fast performance that outclasses SCM tools like Subversion, CVS, and Perforce.
Python is an interpreted high-level general-purpose programming language that not only constructs but also aims to help programmers write clear, logical code for small and large-scale projects with its object-oriented approach. Pip3 is the package installer for Python that can be used to install packages from the Python package index and others. It comes with the latest version of Python. We will be using Pip to install the required dependencies such as ‘setuptools’ and ‘git install malboxes’. Pip3 gets you a newer version than that with ‘apt-get’. Furthermore, combined with ‘virtualenv’, it allows you to install your dependencies within a single directory.
Install Vagrant: Vagrant is a virtual machine based environment management tool. Vagrant Boxes are prebuilt basic images that can be used as a starting point. This can be used to build a Malboxes image to test malware on it. Vagrant works on Mac, Linux, Windows, and more. Remote development environments force users to give up their favourite editors and programs. Vagrant works on your local system with the tools you’re already familiar with.
Install Packer 1.2.3 and add it to environment variables: Packer is a program that automates the production of machine images of any form. It encourages users to utilise a framework like Chef or Puppet to install and configure software within Packer-created images, embracing modern configuration management. The Packer images allow machines that are fully loaded and configured to start in seconds. They can run production in AWS, staging/QA in a private cloud like OpenStack, and development in desktop virtualisation solutions like VMware or VirtualBox because they build similar images for many platforms. Add the downloaded exe file to environment variables in the Advanced System Settings, while installing Packer 1.2.3.
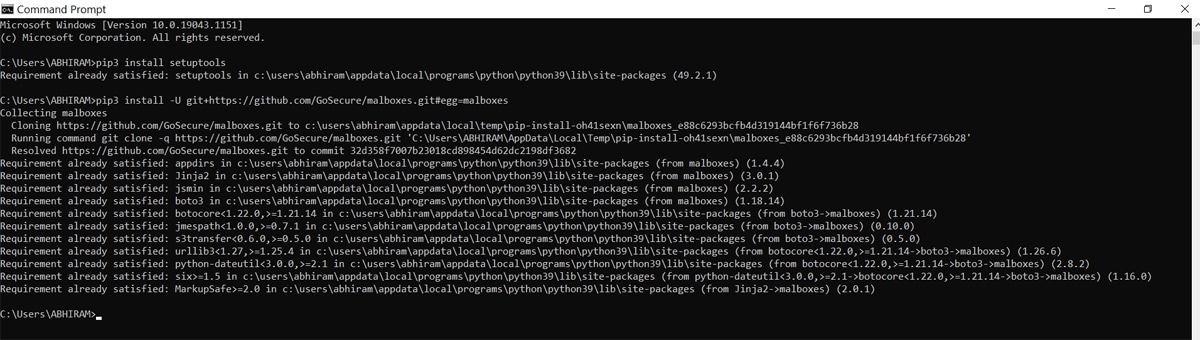
Install Malboxes and setuptools through CLI: Setuptools is a set of improvements to the Python distutils. It makes creating and developing Python easier for developers, particularly those that rely on other packages. Since Malboxes have dependencies, we can use setuptools to install them correctly.
Malboxes builds malware analysis on Windows virtual machines, providing an environment to test malware. Figure 3 shows the commands that have to be entered into the command prompt.
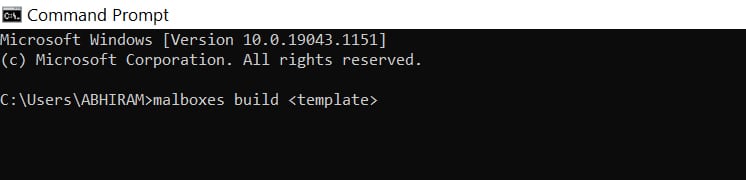
Next, check for Malboxes installation and create a box. As shown in Figure 4, this will build a Windows 10, 64-bit VM. We can check for other VMs by entering ‘malboxes list’ in the CLI.
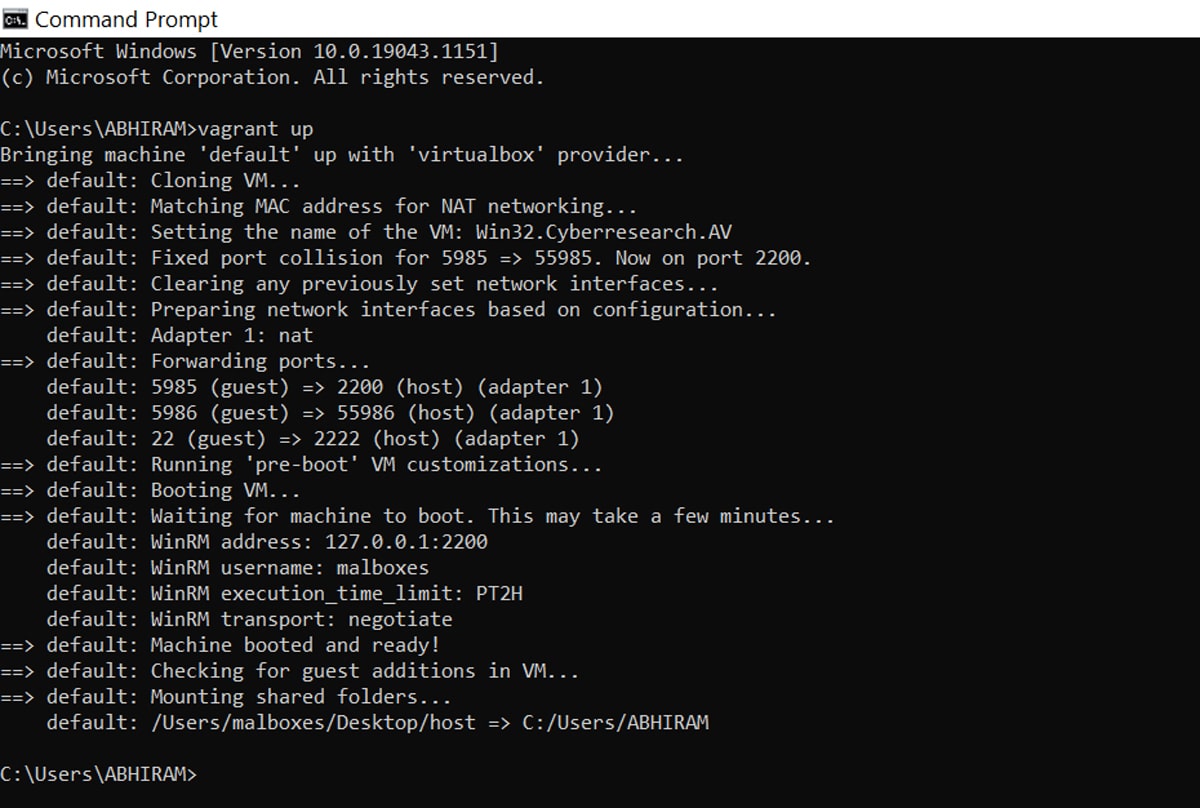
Now create a Vagrant file for malware analysis by typing in ‘vagrant up’.
This command creates and configures guest machines according to your Vagrant file. This is the singlemost important command in Vagrant (can be viewed in Figure 5), since this is how any Vagrant machine is created.
In the next step, spin up the new VM using the above syntax; for example: ‘malboxes spin win7_32_analyst newWin32VM’.
The ISO file can be found in the virtual box by double clicking on the new ISO file, or just running it by clicking on run. The VM should now start booting. Make sure sufficient RAM and system resources are provided to the VM.
Sample malware analysis
Let us now analyse a sample malware executable file in the built-in WinDBG on the Windows virtual machine. The steps to carry out the analysis are as follows.
Download a sample malware file: There are multiple resources from which we can download suitable malware executables for analysis, one of which is the GitHub repository called ‘Malware-Samples by fabricagic72’. These samples were caught by the owner of the repository using various honeypots. TekDefense has a bunch of executable malware samples as well, as seen in Figure 6.
Disable Defender and prepare for analysis: Find ‘disable_defender’ under the tools and execute it. The will disable the Defender on the VM.
Open a debugger such as WinDBG that comes with the virtual machine. It should be titled ‘x64dbg’.
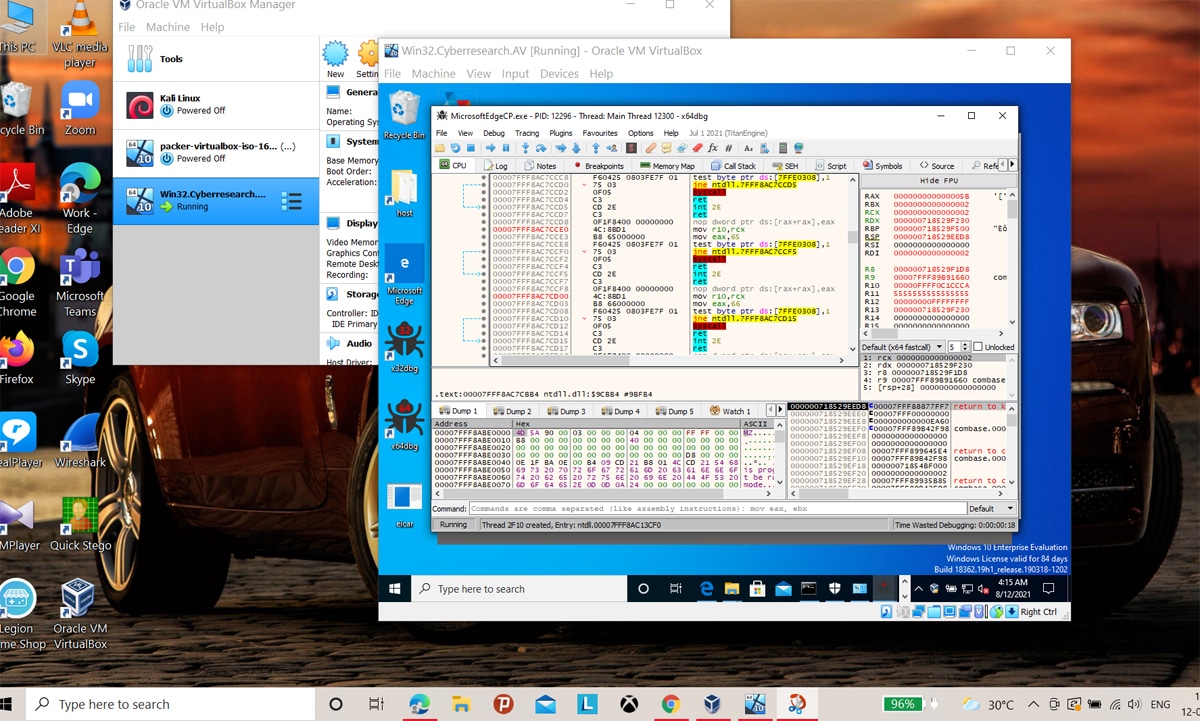
Drag and drop the executable file into the debugger: To analyse the malware, we now click on ‘show code’ and then read the code. A red flag indicates that the code is obfuscated, and hints at a malicious program. This confirms that the potentially malicious program stays in its bounds and does not break out of the sandbox, providing for safe malware analysis.
The code snippet shown in Figure 8 is part of the malware payload, where the functions and objects are haphazard and nonsensical, hinting towards code obfuscation and a malicious program.
So we have learnt how to build a Malboxes lab environment for offline malware analysis and also tested it. Malware today is constructed in such a way that it can detect a VM and may even try to leap out of the environment, onto the host. Hence, performing malware analysis in a controlled environment is recommended.









































































