Tag: Security
“Risk minimisation while dealing with open source and cloud software is...
UK-headquartered Source Code Control Limited provides services ranging from open source software risk management to bespoke cloud transformation recommendations. It has just set up...
Microsoft launches Cloud Katana into Open Source
Tech giant Microsoft announced to open source Cloud Katana, a cloud-native serverless application built on the top of Azure Functions to assess security controls...
OAuth2 Demystified
In the era of rapid application development and deployment as well as concerns around security and privacy, the OAuth2 authorisation is a huge boon.
When...
Deliver Software Faster with Secure DevSecOps
In the new digital world, businesses are demanding quick release cycles. Teams have started adopting continuous integration and continuous delivery practices along with other...
Detecting an Attack with Snort is Easy
If you are interested in security, you may have already used Snort for checking your machine’s security status. Snort is a free and open...
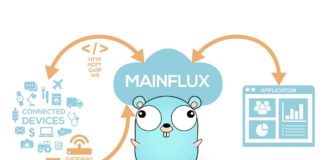
Exploring Mainflux and Its Usage
Mainflux is a highly secure, open source and patent-free IoT cloud platform developed in the GO programming language. It is based on a set...
Getting Started with Blockchain
Transparency, immutability and security, which characterise blockchain technology, have propelled it into unthought of domains. From being a means of carrying out decentralised monetary...
What PHP Developers Can Do to Secure Web Apps
Web applications scripted in PHP are vulnerable if proper precautions are not taken to ensure security. This article highlights the measures to be taken...
The Linux Foundation Announces Formation Of Open Source Security Foundation
It will combine efforts from the Core Infrastructure Initiative, GitHub's Open Source Security Coalition and other open source security work from founding governing...
Tools to Ensure the Security of Web Applications
Web applications have the potential to reach a wider spectrum of users in comparison to desktop apps, and hence have become a popular platform...