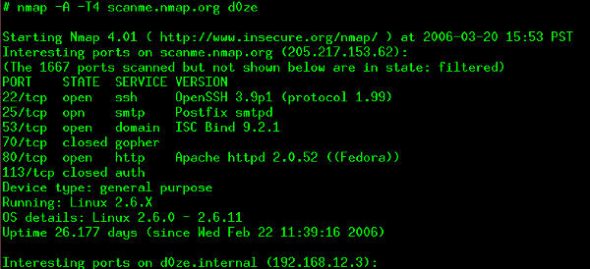
 Nmap is Hollywood’s most famous “hacking” tool that has featured on numerous blockbusters. It was originally written to find hosts in a network thus creating a map of the network. Nmap does this by sending some unique packets and analysing the response received. Over the years, Nmap has grown tremendously and can now figure out the operating system, services with their versions and other statistics like presence of a firewall and uptime of the machines it scans.
Nmap is Hollywood’s most famous “hacking” tool that has featured on numerous blockbusters. It was originally written to find hosts in a network thus creating a map of the network. Nmap does this by sending some unique packets and analysing the response received. Over the years, Nmap has grown tremendously and can now figure out the operating system, services with their versions and other statistics like presence of a firewall and uptime of the machines it scans.
Version 6 of Nmap was recently released after almost three years of active development and boasts a more powerful Nmap Scripting Engine, over 250 new scripts, full IPv6 support and improved scan speeds among many other improvements.
With close to 4,000 code commits since version 5, Nmap 6.0 has many outstanding new features added in the arsenal. Nmap released what it calls the top 6 improvements in version 6. Let’s review what they think makes this version worth the upgrade.
Improved Nmap Scripting Engine
The Nmap Scripting Engine, NSE for short, uses the Lua scripting language. You can automate most of the tasks using it. NSE was built to make it easy to run tasks such as vulnerability scanning, backdoor scanning, exploitation. Almost 300 scripts were added from version 5 to 6. All the scripts in the current version of NSE are documented on the project website. Along with the addition of scripts, the NSE has undergone massive infrastructure improvements providing a sizeable boost in performance.
Web Scanning Improvements
When Nmap came into existence in the late 90s, Internet wasn’t as sophisticated as it is today. Most hosts were only serving static content and simple TCP/UDP ports could pretty much spill all the information about a host. With shared hosting and URL resolutions, the scan scenario is quite different these days. Nmap Web scanning has evolved with the Internet and this release isn’t an exception to it.
Capabilities of brute force attacks, HTTP pipelining and caching were already present. The new NSE uses these techniques and scripts to achieve better automated scans. With close to 50 scripts added everything from complex tasks as as finding backup copies of files on a server to simply grabbing favicons off of hosts can now be performed with this tool.
Full Support for IPv6
IPv6 has been around for a long time and yet most servers and operating systems still don’t fully utilise this new standard. The Internet has been trying to move to IPv6 due to exhaustion of IPv4 addresses.
Nmap now supports OS detection, raw packet scanning, advanced host discovery on IPv6. It’s still under heavy development though, the advantage of IPv6 is also the main issue in scanning. Brute force host discovery was possible on IPv4 due to relatively less address space. With IPv6, this is no longer possible so some workarounds were required. It still does a pretty good job considering how unenthusiastic the Internet has been to move to IPv6 thus far.
Nping Replaced
Nping, as the name suggests, generates packets, analyses them and does response time measurements. It also generates packets for almost all protocols being used around the Internet today. It’s not just a simple packet generator though.
The best thing about Nping is its ability to echo packets. As the packets change from hop to hop, Nping can analyse these changes and determine things such as firewall rules, packet corruption detection. Of course, it can also generate packets for multiple hosts and ports with fully custom packet header format which can extend to a self stack stress test, ARP poisoning and Denial of Service attacks to name a few.
More Bling-Bling
Don’t get me wrong, I actually love its command-line interface. However, there are people who want all the information to be graphically available — and, at times, they are correct. Nmap comes with a GUI called Zenmap.
A GUI makes sense for people who know little about Nmap. It gives easier access to NSE scripts, tells you what options the scripts take, lets you set filters that update the display results in real time… they have done a good job with this and many experienced CLI users
might also find this intuitive — or just something new to play with ;-)
Speed… Speed… Speed
Let’s face it — port scanning is a slow process. NSE scripts try to implement parallelism and improve the scanning speeds as much as they can, but scanning tens of thousands of machines is still pretty time consuming. People behind Nmap have been trying to reduce this delay to a minimum and they have successfully done it in certain cases.
Some of the highlights of this release are: less number of probes required for the same scans, time requirements have reduced to a mere 10 per cent of Nmap 5, faster OS fingerprinting, and better Zenmap performance.
Bottom-line
The points highlighted above are just the gist of the abundance of improvements that Nmap brings with the 6.0 release. Some features listed on its roadmap are additions such as an updater script for NSE, real-time OS fingerprinting updates and even more scripts for the NSE.
The bottom-line? With Nmap alone and enough knowledge about use-cases, you can put your network under a stress test and fortify it to your needs. Like any powerful technology, however, Nmap can be used for blackhat hacking, unauthorised breaches, vulnerability discovery to name a few. This makes the use of Nmap slightly questionable. There are places where unauthorised packet injection or port scanning is illegal. So, you better know what you’re doing before you do it. Keeping that in mind, Nmap remains one of the most powerful tools out there and learning to use it properly is something every aspiring and seasoned sysadmins must have on their to-do list.
From the past: Check out our series of articles on advanced Nmap usage here.
Feature image courtesy: nmap.org



Nice one. Thanks
[…] What’s New in Nmap 6 […]
I dont see Nmap’s website mentioning about version 6.0… where did this come from please?