The on-premise versus cloud data storage debate is an ongoing, never ending one. When deciding on either of them, the security of the data is of utmost consideration. There are many myths and fears surrounding cloud security. This article seeks to dispel them by clearly outlining the safety and security in cloud storage, compared to on-premise storage.
The term cloud basically refers to ‘anything’ that is not on your computer or logical drives, and which can be accessed (read or written to) from your computer with the help of the Internet. This ‘anything’ on the cloud is stored, hosted and maintained in some data centre of usually a third-party storage provider. Some of the world’s leading cloud services are Amazon Web Services (AWS), Microsoft Azure, Google Cloud, and so on.
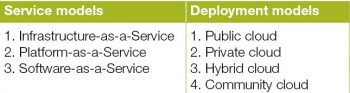
As per the US based National Institute of Standards and Technology (NIST), there are three service models and four deployment models for cloud storage, as listed below.
Nowadays, organisations are moving their infrastructure to the cloud on a large scale instead of setting up their own on-premise storage, which comes with huge installation and maintenance costs. The major benefits are high reliability, low maintenance and optimised costs, as you pay only for what you use.
Cloud storage has a wide range of benefits but there are some concerns too. The major concerns arise with regard to security. What if a cloud storage provider’s servers, which host its customers’ sensitive data, are hacked into or compromised by some unauthorised person accessing them and, even worse, the clients are denied access to their own data?
Let’s discuss cloud security so that it helps you stop worrying about it.
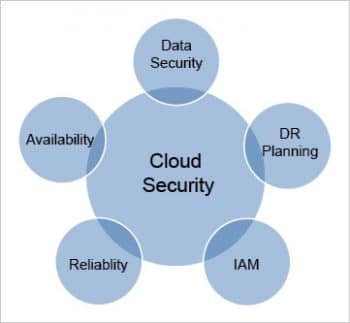

Cloud security vs on-premise security
Cloud security
To understand the security provided by the cloud, it is important to know how data is being stored in the cloud and how resources are provided to customers. This is done in two ways.
- Shared infrastructure: In this case, multiple customers are allotted resources from storage/drives of a single machine. This weakens the trust of customers, making them unwilling to store sensitive data. This can be conceived as renting different flats to different tenants in a single apartment building, where every tenant has his/her own set of keys to enter his/her flat. No one can step into someone else’s flat, unless the door is kept open or the tenant forgets to lock it. This is how security in shared infrastructure works. By managing proper authentication, one can reduce the chance of a security breach considerably. But customer awareness is necessary in this respect.
- Dedicated infrastructure: This is when customers are allotted dedicated machines and not shared resources. Here you have the entire apartment building to yourself, where you have the authority to appoint a guard to take care of it or do it on your own. Since you have rented the entire apartment building, you need to pay a high cost. The cloud providers only interfere if you ask them to do so. You can provide any level of security you wish or can afford to.
From the hardware point of view, you are guaranteed high reliability, high durability, and high availability. You are covered against disaster as the service providers give you the option of storing your data in multiple zones. It is highly unlikely that data stored in different zones and in different data centres will become unavailable at the same time, even in the case of some natural disaster—as it is not going to occur at all the data centres at the same time.
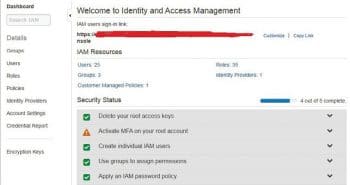
Cloud providers like Amazon provide identity and access management (IAM). This allows organisations to enforce role based controls on what a user can do in an AWS environment (IAM integrates with users’ existing Active Directory or other authentication platforms). Breech of this kind of security depends upon how well you are providing access controls based on the roles you have created for the user(s). The cloud providers offer you the ability to analyse the activity on the cloud through detailed logs, using which you can audit any unusual or potentially malicious activity.
Figure 2 gives an example of the cloud security provided by AWS.
Security in a cloud environment is a shared responsibility. It differs based on which service model and deployment model is used. The security issues fall into two categories:
1. Those faced by cloud service providers
2. Those faced by customers
AWS provides five layers of security, and it would be good if these are followed by the rest of the cloud service providers. The five layers are listed below.
Identity and Access Management (IAM): This provides role based authentication.
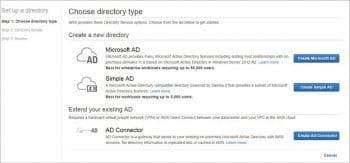
Directory Service: This provides easy set-up with your existing Microsoft AD, Simple AD and AD connector.
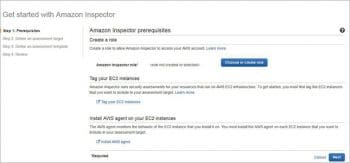
Inspector: Amazon Inspector automatically assesses applications for vulnerabilities or deviations from best practices.
WAF: This is a Web application firewall, which protects your Web app from common exploits that consume excessive resources, compromise security or affect application availability.
Certificate Manager: This helps in procuring SSL/TSL certificates for your AWS.
On-premise security
You can physically locate your hardware resources on-premise, and seeing the green LED flicker can lead you to assume that everything is alright. But once your resources are connected to the Internet, they are no more private. You can monitor the health of your server, but who can ever know the exact location of data once it’s transferred from the source?
Even physical security of your hardware may be at risk if the intentions of those safeguarding your servers are not bona fide—perhaps because you delayed their payment for the past month or you are not paying them as per their expectations. You can always implant a CCTV camera, but this will only give you footage and not security.
Although it has been a major cause of debate between vendors and customers, cloud providers usually do not charge you for the maintenance of their hardware.
Public clouds increase security
Nowadays, cloud security is a hugely debated topic. All the cloud service providers guarantee maximum security. They provide services in three models—Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS) and Software-as-a-Service (SaaS). The main formula for successful security in any model provided by cloud service providers is ‘restricted and required’ access.
Even if the railway platform is for public use, there are certain rules that need to be followed before you step on to the platform, otherwise you will get into trouble. The same way, these cloud service providers force their customers to impose certain security rules for public access. Some of these rules are listed below.
1. Security groups: These are the groups that define the firewalls for a system. That system may be an instance, a database, a group of instances or even as large as your entire virtual cloud. These security groups have their own set of boundaries, namely, inbound and outbound range. You can add/delete/edit the rules defined inside these boundaries. You have the luxury to set your rules—from giving access only to an SSH user at Port 22 from some specific machine, to allowing access to the entire world.
2. Network access control lists (ACL): This is an optional layer provided by some of the cloud service providers these days. In AWS, this acts as a firewall for controlling traffic to one or more subnets.
3. Key-pair access to VMs: Key-pair is basically known as key cryptography. It is used to encrypt and decrypt the login information. The public key is used to encrypt the login data such as passwords, and then the private key is used to decrypt the data. This pair of public and private keys is known as a key-pair and the mechanism is known as key-pair cryptography. Many cloud providers use this key-pair to give their customers access to their virtual machines.
4. Identity and access management (IAM): This allows organisations to enforce role based controls on what users can do in an AWS environment (IAM integrates with the users’ existing Active Directory, or other authentication platforms).
5. Virtual private cloud (VPC): This is like your data centre inside the cloud’s data centre. You have control over configuring your own route table, access control list (ACL), Internet gateway, and subnet setting.
Apart from these, there are some server level security systems like ipconfig, sysconfig, etc.
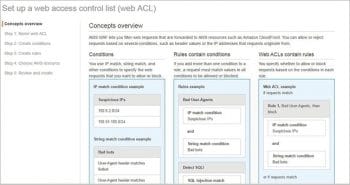
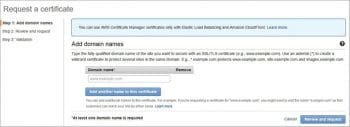
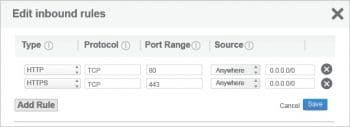
Possible threats and controls
In today’s world, we are the greatest threat to our own data. I would like to divide these security threats into two broad categories.
Physical security threats
Physical security is the biggest reason why organisations swarm to the cloud these days. The cloud not only takes care of the most satisfying feature called availability, i.e., more than 99 per cent, but it also takes care of the reliability and durability of resources to a great extent. On-premise infrastructure can never dream of reaching such levels. Cloud providers have data centres in multiple zones, and the hardware (like servers, routers, cables, etc) is physically isolated and secured from any unauthorised access, any natural disaster, and from theft.
The main concern with on-premise infrastructure is related to its ageing and obsolete technology. Cloud service providers use the most advanced, up-to-date technology to ensure against any damage to hardware or stored data.
Virtual security threats
Virtual security can be further divided into two categories.
Network security threats: There are many network related threats. With the advancement of technology, there is a rapid growth in the types of these threats. Every time a solution is found, new threats emerge. These threats clearly depend upon the malicious intent of human beings. Examples of such threats are DoS attacks, phishing attacks, MITM attacks, etc.
All these threats have been identified and mitigated to a large extent. It is not like there is no cure for any emerging malady. Of course, we humans are responsible for every loophole, as we make mistakes. If we think the way the attacker thinks, and if we take care of every small glitch, we can minimise the risks to a great extent. So here are some precautions that need to be taken at the time of set-up. Remember, prevention is always better than cure.
1. Make an access list and provide access only to those on the list.
2. Maintain a system to identify all unwanted access and activity, and analyse intrusions properly. Do not promote the ‘let it go’ attitude within the organisation.
3. Use secure protocols for remote login, such as SSH.
4. Use a difficult password.
5. Configure access lists or firewalls to permit only necessary traffic.
New and unique security solutions can be identified depending on your set-up and requirements.
Data security threats: With technology advancing and with the development of cloud computing, data security has turned into a major concern. Rising concerns have led to the development of some important methods to fulfil security requirements. These include advanced authentication encryption, key management, HSM (hardware security module) integration with safe-net and, of course, data masking.
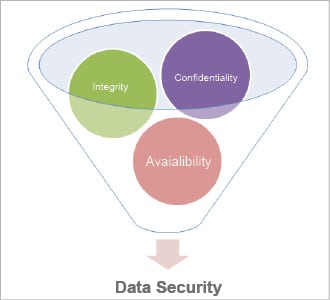
Data security needs to achieve three main goals.
- Confidentiality is privacy. To keep data private, it is necessary to maintain the privacy of each form of data. Not only is the privacy of sensitive data of the utmost priority, but the metadata and transactional data also needs to be safeguarded. There are many ways to secure data as described above, such as encryption, access control, any type of data masking as well as logical preventions.
- Integrity of data is the non-adulteration of data. No matter what happens, data integrity has to be maintained. Think of the consequences if your surname changes in your voter ID card. Data integrity can be achieved with a little effort. A well audited code also helps in maintaining the integrity of data. Data integrity is of utmost priority in case of revision control systems such as Git or Mercurial. They allow users to roll back previous versions of saved data. These systems use the SHA-1 algorithm to ensure data has not changed because of any accidental corruption.
- Availability is the third most important goal. What is the use of that voter ID card if you cannot vote for the upcoming elections? You think of using a bidding application but are prevented from bidding because you cannot access your banking site. Availability can be achieved with widespread Internet enabled access, and this is the topmost aim of any cloud service provider. AWS uses CloudFront to provide low latency in data access.

Managing your cloud
Management is the key while maintaining the security and integrity of your cloud. This has been a very hot topic since the development of cloud technology. There are tools that provision, monitor and can audit the activity on the cloud.
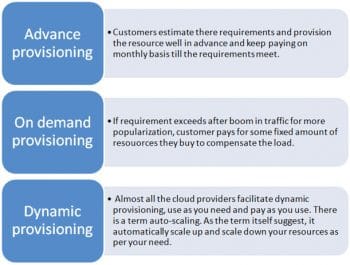
There are technologies that ease the management of the cloud in very huge projects, where management becomes a really tough task. Imagine monitoring and scaling 30,000+ servers behind a shopping website on a regular basis, with this provisioning of servers increasing steeply during sales and offers provided by the sites. Some cloud providers offer dynamic provisioning, while some provide these services on-demand. Generally, there are three types of provisioning supported by cloud providers, which are shown in Figure 10.
A good management of your cloud environment not only ensures the security of your cloud but also plays a key role in using your resources in a very wise, effective and economical way.
Some pointers which enable good management of cloud services are shown in Figure 11.
There are no plug-and-play devices available to ensure the 100 per cent security of anything in this world. The only thing we can do is to take the necessary precautions to prevent damage. We humans are the biggest threat to this world and to cloud security. So, remember, it’s you who can make your security air tight.











































































Good read