A virtual private network (VPN) acts as a secure tunnel, which extends over a public or shared network, so that data can be exchanged anonymously and securely across the Internet, just like using a private network. In this article, sysadmins can get an insight into the best free and open source VPN tools available.
With the explosive growth of the Internet, the one main thrust of every IT organisation is to exploit it to the maximum to further business interests. Initially, companies used the Internet to promote their products, brand image and services through corporate websites. But the Internet today is visualised as a platform with limitless possibilities. The focus has shifted to e-business, whereby the global reach of the Internet is used for easy access to key business applications and data that resides in traditional IT systems. Companies are looking for the best solution to securely and cost-effectively extend the reach of their applications and data across the world. While Web-enabled applications can be used to achieve this, a virtual private network (VPN) offers a more comprehensive and secure solution.
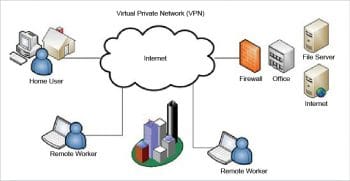
VPNs securely convey information across the Internet connecting remote users, branch offices and business partners to an extended corporate network. The basics of a VPN are highlighted in Figure 1.
According to a report by Orbis Research, the global VPN market was valued at US$ 15.64 billion in 2016 and is expected to reach US$ 35.73 billion by the end of 2022, growing at a CAGR of 14.77 per cent between 2016 and 2022.
A VPN is an extension of an enterprise’s private intranet across a public network such as the Internet, creating a secure private connection, essentially through a private tunnel.
The VPN definition can be split as follows.
- It is virtual: This means that the physical infrastructure of the network has to be transparent to any VPN connection. In most cases, it also means that the physical network is not owned by the user of a VPN, but is a public network shared with many other users. To facilitate this transparency to the upper layers, protocol tunnelling techniques are used. To overcome the implications of not owning the physical network, service level agreements (SLAs) with network providers are created to provide, in the best possible manner, the performance and availability requirements needed by the VPN.
- It is private: The word ‘private’ with regard to VPNs refers to the privacy of the traffic that flows over the VPN network. VPN traffic flows over public networks and therefore the necessary security precautions need to be taken. The security requirements are: data encryption, data authentication, secure cryptographic keys to follow encryption and authentication, defence against the relay of packets and address spoofing.
- It is a network: A VPN is regarded as an extension to the company’s existing network infrastructure. This means that it must be available to the rest of the network, to all or a specified subset of its devices and applications, by regular means of topology like routing and addressing.
Types of VPNs
VPNs can be classified into the following two main categories:
- Site-to-site VPNs
- Remote access VPNs
Site-to-site VPN: This allows offices in multiple fixed locations to establish secure connections with one another over public networks such as the Internet. A site-to-site VPN extends the company’s network, making computer resources from one location available to employees at another. It is also called router-to-router VPN.
Site-to-site VPNs are categorised into the following two types.
- Intranet based: If a company has one or more remote locations and wishes to connect them under a single private network, an intranet VPN can be created to connect each separate LAN to a single WAN.
- Extranet based: IT organisations working in close collaboration with other organisations can build an extranet VPN that connects to those other organisations’ LANs. An extranet VPN allows the companies to work together in a secure, shared network environment while preventing access to separate intranets.
Remote access VPN: A remote access VPN allows a user to connect to a private network and access its services and resources remotely. The connection between the user and the private network happens via the Internet and the connection is secure. There are two main components in remote access VPNs. The first is the network access server (NAS), also termed the media gateway or remote access service (RAS). It is regarded as a dedicated server in which the user connects to the Internet to use the VPN. The NAS connectivity requires a valid user name and password, and to authenticate the user every NAS has its own authentication procedure. Another requirement is remote access VPN-client software. All the users who want to use VPN services have to install software in the users’ own computers to establish and maintain the VPN connection. A remote access VPN is useful both for business as well as home users.
VPN protocols
A VPN primarily depends on how it is used and how much security, performance and uptime is required by specific users. A VPN has many protocols, which enable users to communicate between sites, cloud based vendors, streaming services and even gaming servers.
The following are the basic protocols for VPNs.
- Point to Point Tunnelling Protocol (PPTP): This is one of the most common, easy to configure and fast VPN protocols. It is very useful for audio and video streaming, and works without any hiccups on even old devices with limited processing capabilities. PPTP has a lot of security vulnerabilities — its underlying protocols like MS-CHAP-v1/v2 are unsecure and can easily be cracked by hackers. It uses 128-bit encryption keys for sensitive data transfers.
- Layer 2 Tunnelling Protocol (L2TP): This is a standard protocol for tunnelling L2 traffic over the IP network. Its ability to carry almost any L2 data format over IP or other L3 networks makes it highly useful. The UDP port is used for L2TP communications, but it doesn’t provide any security for data like encryption and confidentiality like the IPSec protocol. It consists of two components — the tunnel and the session. The tunnel provides reliable transport between two L2TP Control Connection Endpoints (LCCEs) and carries only control packets. The session is logically contained within the tunnel and carries user data. It is not secure by itself and uses IPSec and 3DES encryption methods.
- IPSec (Internet Protocol Security): IPSec is a trusted encryption and tunnelling protocol that uses encryption on the IP traffic over a given tunnel. It defines cryptographic algorithms used to encrypt, decrypt and authenticate packets as well as the protocols required for secure key exchange and key management. It contains two mechanisms for securing IP packets. The first is ESP (Encapsulating Security Payload) Protocol, which defines a method for encrypting data in IP packets and the authentication header (AH) for the digital signing of IP packets. The second mechanism to secure IP packets is IKE (Internet Key Exchange), which is used to manage cryptographic keys used by hosts for IPSec.
- Secure Socket Tunnelling Protocol (SSTP): This is considered as a top-grade VPN secure protocol with 2048-bit encryption providing a mechanism to transport PPP traffic via the SSL/TLS channel. SSL/TLS provides transport-level security with key negotiation, encryption and traffic integrity checking. SSTP can be used to pass through proxy servers and firewalls. During the session, clients and servers using SSTP must be authenticated during the SSL phase of transmission. Generally, SSTP is used for remote access, i.e., by an employee accessing a network remotely from a different office or home who has no support for network-to-network tunnels. Performance wise, the quality of SSTP will degrade if the bandwidth is limited, and any lack of bandwidth can lead to sessions expiring.
- Multi-Protocol Label Switching (MPLS): This is used within the computer network infrastructure to speed up the data flow from one point to another. It implements and uses labels for routing decisions. MPLS operates by assigning a unique label or identifier to each network packet. The label consists of the routing table information, such as the destination IP address, bandwidth and other factors, as well as the source IP and socket information. The router can refer only to the label to make the routing decision rather than look into the packet. MPLS supports IP, asynchronous transfer mode (ATM), frame relay, synchronous optical networking (SONET) and Ethernet based networks. MPLS is designed to be used on both packet-switched networks and circuit-switched networks.
- Hybrid approach: Modern VPN networks use a blend of MPLS and IPSec protocols to leverage broadband bonding routers to make a cost-effective and reliable VPN architecture.
So, considering the adaptability of VPN, lots of VPN services have been created to address the increasing need to create custom VPN connections.
In this article, we list the top open source tools available for sysadmins to create their own VPNs.
SoftEther
SoftEther (Software Ethernet) is an open source, cross-platform, multi-protocol VPN client and VPN server software that supports almost all VPN protocols like SSL VPN, L2TP/IPSec, OpenVPN and Microsoft SSTP protocol. It provides sysadmins with a strong alternative to other VPN products like OpenVPN, IPSec and MS-SSTP, and is considered to have the best throughput, low latency and high resistance to firewalls. SoftEther VPN optimises performance by full Ethernet frame utilisation, reducing memory copy operations, parallel transmission and clustering.
Components
- SoftEther VPN server: This implements the VPN server, and listens to and accepts connections coming from VPN clients or the VPN bridge with varied VPN protocols.
- SoftEther VPN client: This has a virtualised function of the Ethernet network adapter. It has advanced functions like the best VPN communication settings compared to other VPN clients.
- SoftEther VPN bridge: This builds site-to-site VPNs, and systems administrators use it to install the SoftEther VPN server on the central server and SoftEther VPN bridge on remote sites.
- VPN server manager: This is a GUI based tool for systems administrators for the SoftEther VPN server and bridge.
- Command-line admin utility: This program runs on the consoles of every supported operating system. When users are unable to use Windows or Linux with Wine, they can alternatively use vpncmd to manage the VPN programs. vpncmd is also useful to execute a batch operation, such as creating many users on the virtual hub, or creating many virtual hubs on the VPN server.
Features
- Supports site-to-site and the remote access VPN with AES-256 and 4096-bit encryption.
- High speed throughput performance up to 1Gbps; IPv4 / IPv6 dual-stack; no memory leaks.
- Supports all VPN protocols like OpenVPN, IPSec, L2TP, MS-SSTP, EtherIP, L2TPv3; multi-language support and deep-inspect packet logging function.
- Cross-platform support including for Windows, Mac, Android, iOS, Linux, etc.
Official website: https://www.softether.org/
Latest version: 4.28
Algo VPN
Algo VPN is open source software that’s specially designed for self-hosted IPSec VPN services. It was designed by the folks at Trail of Bits for fast deployment, using modern protocols and ciphers to enhance security. It comprises a set of Ansible scripts for easy setup by systems admins for creating personal IPSec based VPNs. Algo automatically deploys an on-demand VPN service in the cloud that is not shared with other users.
Features
- Supports sysadmins with a helper script to add or remove users from the network instantly.
- Supports only IKEv2 with encryption algorithms, i.e., AES-GCM, SHA2, P-256 and Wireguard.
- Facilitates configuring limited SSH users for tunnelling traffic.
- Supports DigitalOcean, Microsoft Azure, Google Compute Engine, OpenStack, Vultr and Ubuntu 18.04 server.
Official website: https://github.com/trailofbits/algo
Streisand
Streisand only supports installation on the Ubuntu 16.04 server using single commands, and supports L2TP, OpenConnect, OpenSSH, OpenVPN, Shadowsocks, Stunnel, Tor Bridge and Wireguard. Depending on the protocol chosen by the user, apps can be installed. It has many features that match those of Algo, but provides more protocol support for sysadmins. Streisand is installed using Ansible, and users can be added easily using custom-generated connection instructions. It includes an embedded copy of the server’s SSL certificate.
Features
- Step-by-step client configuration is done by the newly installed Streisand server and users can install it using Web browser based instructions.
- Uses SHA-256 checksums for verifying GPG signatures.
- Supports Amazon EC2, DigitalOcean, Google Compute Engine, Linode or Rackspace.
Official website: https://github.com/StreisandEffect/streisand
OpenVPN
OpenVPN is a free and open source, cross-platform VPN software application to help systems administrators to create point-to-point and site-to-site connections in routed or bridged configurations and remote access facilities. It adopts a custom security protocol that uses SSL/TLS for key exchange. OpenVPN can traverse firewalls and NAT firewalls, allowing users to bypass gateways and firewalls that might otherwise block connections.
Architecture components
- Encryption: OpenVPN uses the OpenSSL library to facilitate data and control connection encryption and authentication. It also uses HMAC packet authentication to provide an additional layer of security to the connection. It supports mbed TLS for better encryption in real-time traffic flow.
- Authentication: It offers pre-shared keys, and certificate based and user name/password based authentication.
- Networking: It supports both TCP and UDP transport connections, while multiplexing is created on SSL tunnels on a single UCP/TCP port. It can work better with almost all proxy servers and NAT, as well as get through firewalls.
- Security: Provides 256-bit encryption through the OpenSSL library, and has the ability to drop root privileges and use mlockall to prevent swapping sensitive data to the disk. It also supports the use of smart cards through PKCS#11 based cryptographic tokens.
- Extensibility: OpenVPN provides advanced features like logging, enhanced authentication, dynamic firewall updates, RADIUS integration, etc.
The two versions of OpenVPN available are:
- Community Edition: Free and open source.
- Access Server: Commercial community edition with add-on features like LDAP integration, SMB server, Web UI management, and add-on tools installation for smart VPN connectivity.
Features
- SSL/TLS for session authentication and IPSec ESP for tunnel transport over UDP.
- Compatible with SSL/TLS, RSA certificates, X.509 PKI, Dynamic Host Configuration Protocol (DHCP), Network Address Translation (NAT) and TUN/TAP virtual devices.
- Fully automated VPN certificate management and provisioning built-in. External PKI is also possible, so you have full control over your existing PKI and use the OpenVPN solution with it.
- Access control rules let you specify which user or group has access to which IP addresses or subnets, and if VPN clients can contact each other or not.
- Built-in authentication system with Web based management. External authentication systems like PAM, LDAP or RADIUS can also be used. The authentication system is extensible but requires programming knowledge (Python).
Official website: https://openvpn.net/
Latest version: 2.4.6
PriTunl
PriTunl is an open source VPN server-cum-management panel designed by BeyondCorp that enables systems administrators to create a cloud VPN with secure encryption, complex site-to-site links and gateway links. It also provides remote access to users in a local network via a Web interface. It makes use of the OpenVPN protocol to run a VPN server, and uses the Let’s Encrypt certificate to secure the VPN server and Web GUI. It uses MongoDB at its backend to store all data.
It features up to five authentication layers, a fully customised plug-in integration system, is cross-platform and provides support for OpenVPN clients and AWS VPC networks.
Features
- All source code is available at GitHub to enable developers to re-configure, re-design and develop advanced features, allowing complete transparency and customisation.
- Enables sysadmins to do all configurations using a Web GUI, which is easier than other VPN servers.
- Facilitates end-to-end security between client and server, and uses Google Authenticator for one-step authentication.
- Uses IPSec for site-to-site links and VPC peering.
- Easy integration and configuration with other third party services using the REST API.
Official website: https://pritunl.com/
Latest version: 1.29.1827.6
strongSwan
strongSwan is an open source multi-platform IPSec implementation proposed by Andreas Steffen at the University of Applied Sciences in Rapperswil, Switzerland. This VPN solution implements both IKEv1 and IKEv2 key exchange protocols, and uses UDP encapsulation and port floating for NAT-traversal. It supports the Online Certificate Status Protocol, message fragmentation, and modular plugins for crypto-algorithms; it also supports OSCP, CA as well as RSA private keys and X.509 certificates. It is supported by all native clients like Linux, Windows, Mac OS X, FreeBSD and Blackberry OS.
Features
- strongSwan supports Elliptic Curve Cryptography (ECDH groups and ECDSA certificates and signatures) both for IKEv2 and IKEv1.
- Automatic assignment of virtual IP addresses to VPN clients from one or several address pools using either the IKEv1 ModeConfig or IKEv2 configuration payload.
- strongSwan IKEv2 NetworkManager applet supports EAP, X.509 certificate and PKCS#11 smartcard-based authentication.
- Modular plugins for crypto-algorithms and relational database interfaces.
- Automatic insertion and deletion of IPsec-policy based firewall rules.
- Dynamic IP address and interface update with IKEv2 MOBIKE.
- Fully tested support of IPv6 IPsec tunnel and transport connections.
Official website: https://www.strongswan.org/
Latest version: 5.7.1
WireGuard
WireGuard is a multi-platform, open source, simple, fast and most easy-to-use VPN solution available for sysadmins. It uses modern cryptography. It is better than IPSec and OpenVPN in terms of configuration, performance and usability. It is easy to use like SSH, and a VPN connection is developed by simply exchanging public keys, while everything else is handled by WireGuard.
WireGuard uses state-of-the-art cryptography, like the Noise Protocol Framework, Curve25519, ChaCha20, Poly1305, BLAKE2, SipHash24, HKDF, and secure trusted constructions.
WireGuard implements VPN techniques to create secure point-to-point connections in routed or bridged configurations, and it runs as a module inside the Linux kernel. A process called cryptokey routing is at the heart of WireGuard encryption. The mechanism works by associating public encryption keys with a list of VPN tunnel IP addresses that are allowed inside the tunnel. A unique private key and a list of peers are associated with each network interface. Each of the peers has a short and simple public key, used to authenticate it with other peers. These public keys may be distributed for use in configuration files in a number of ways, much like the transmission of SSH public keys.
In any server configuration, each peer (client application, etc) can send packets to the network interface with a source IP address that matches its corresponding list of permitted IP addresses. When the network interface wishes to send a packet to a peer, it looks at the destination IP of the data packet, and compares it to each peer’s list of permitted IPs, in order to determine which peer to send it to.
Features
- WireGuard is designed as a general-purpose VPN for running on embedded interfaces and super computers alike, fit for many different circumstances.
- It is currently under heavy development, but already might be regarded as the most secure, easiest to use, and simplest VPN solution in the industry.
- Though it is still under development, even in its unoptimised state, it is faster than the popular OpenVPN protocols and delivers comparatively lower ping times.
Official website: https://www.wireguard.com/
Latest version: 0.0.20181006
FreeLan
FreeLan is an open source, multi-platform, peer-to-peer VPN software with no GUI but is packed with a multitude of features that allow users to surf the Web anonymously. It implements a peer-to-peer, full mesh VPN to create secure site-to-site and point-to-point connections in routing or bridged mode.
FreeLan uses the Open Secure Sockets Layer (OpenSSL) library to provide encryption of both the data and control channels. It can be configured in the following three ways.
- Client-server: With one computer acting as a server and the rest as clients. The server can also decide whether the clients can communicate with each other or not. This configuration is considered fragile because if anything happens to the server, the complete network can be destroyed.
- Peer-to-peer: In peer-to-peer network configuration, each node (device) is connected to all other nodes and if any node is disconnected, the entire network is not disturbed; so connectivity is ensured at all times.
- Hybrid: This is a combination of the client-server and peer-to-peer networks.
Features
- Offers pre-shared keys, certificate-based and user name-password based authentication.
- Written in C++ and available under the GNU GPL.
- Generic VPN software, not a Web proxy service.
Official website: https://www.freelan.org/
Latest version: 2.0.0