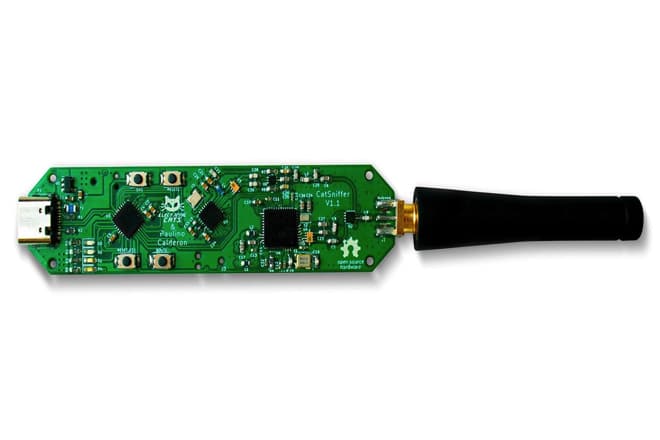
CatSniffer, a new portable multi-protocol sniffer supports multiple frequency bands common to IoT devices. Announced on pre-sale by open source design provider Electronic Cats, the new tool allows debugging, analysing, and sniffing IoT devices. The hardware is released under an CERN Open Hardware Licence v1.2.
CatSniffer covers three core frequency ranges grouped as LoRa, sub-GHz, and 2.4 GHz and protocols including Thread, ZigBee, BLE 5, IEEE 802.15.4g, 6LoWPAN, LoRa (LoRaWAN), and sub-GHz.
The new sniffer relies on two radios – Semtech SX1262 handles LoRa and LoRaWAN communication to cover protocols. It was designed as a portable USB stick that integrates the new generation of the chips TI CC1352, Semtech SX1262, and Microchip SAMD21E17.
This board is an auditing tool for security researchers looking into IoT security. The board can be used with different types of software including third-party sniffers such as SmartRF Packet Sniffer, Sniffle, zigbee2mqtt, Z-Stack-firmware, our custom firmware, or the user can even write own firmware for hacking needs.
“This kit is designed to allow product developers to evaluate electronic components, circuit, or software associated with the kit to determine whether to incorporate such items in a finished product and software developers to write software applications for use with the end product,” reads a company note.
The initial examples are available in CatSniffer GitHub repo.