Your smartphone holds a world of data, but is it secure enough? From understanding network technologies to implementing protection measures, this is your guide to safeguarding digital assets.
Mobile devices have become an extension of ourselves, holding a wealth of sensitive information. As technology advances, securing these devices, especially in enterprise settings becomes increasingly vital. Mobile devices have unique characteristics compared to desktops, making their security a bit more challenging. In this article, we will explore various communication methods as well as the security concerns associated with enterprise mobile security.
Mobile devices use electromagnetic waves (zero and one) for communication with each other, but they lack the capability to transfer data over long distances independently. They rely on different methods such as a cellular network (5G is the fifth generation of cellular wireless standards providing capabilities beyond 4G), Bluetooth, Wi-Fi, near field communications, and so on. Let’s look into these methods in depth and the security concerns they present.
Cellular networks
Cellular networks, also known as mobile networks, are the primary mode of communication connecting end nodes through service provider networks. Each phone communicates with the service provider by radio waves through a local antenna at a cellular base station or cell site. These cellular networks consist of several components.
Cellular layout: Mobile networks are divided into different geographical areas known as cells. These cells are further divided into hexagonal cells — an antenna covers a cell with certain frequencies. Each cell has a transceiver, a mobile tower that wirelessly connects to mobile devices.
Base station: The base station is placed below the tower. Base stations provide the cell with network coverage and connect with the tower to transmit voice, data, and other types of content to consumers. The base stations are meant to improve the signal frequency and communication between interconnected devices such as computers or smartphones.
Tower: This is where the antennas and electronic communications equipment are placed to create a cell or adjacent cells. The cell towers distribute the signals generated by the base station.
Mobile tower switching office (MTSO): All base stations and towers in a city are connected via a high-speed link or fibre optics to a mobile telephone switching office (MTSO). Our mobile does not have enough signal power to directly contact a caller residing in another city; hence, it sends a signal to a mobile tower. The mobile tower then sends signals to the MTSO. The MTSO checks our SIM data in its database to find the cell in which the phone is present, and sends a signal to the other city’s MTSO. Finally, the MTSO sends signals to the mobile through the mobile tower. The MTSO is normally located in the central cell of a cluster and is generally connected to the public switched telephone network (PSTN).
Public switched telephone network (PSTN): A public switched telephone network is a combination of telephone networks used worldwide, including telephone lines, fibre optic cables, switching centres, cellular networks, satellites and cable systems. The PSTN is a century-old worldwide connected telephone network and lets users make landline telephone calls.
Common security concerns: Here is a critical list of security concerns particularly related to the cellular network.
- Traffic monitoring
- Location tracking
- DDOS attacks
- Access fraud
- Stolen phones
- Subscription fraud
Security measures: The key security measures that can help safeguard against these common security threats are:
- Network traffic monitor and analysis
- Encrypted communication
- Velocity checking
- A subscriber usage-pattern database
- Customer call analysis
- Geographic dispersion checking
- Extensive proprietary anti-fraud algorithms
For more in-depth information about cellular network fraud and solutions, you can refer to https://csrc.nist.gov/csrc/media/publications/conference-paper/1997/10/10/proceedings-of-the-20th-nissc-1997/documents/031.pdf.
Wi-Fi
Wi-Fi is the family of wireless network protocols commonly used for local network access. Wi-Fi stands for wireless fidelity. It uses radio frequency to share an internet connection with multiple devices within a certain range via a Wi-Fi router. This router is connected directly to the internet modem and acts as a hub to broadcast the internet signal to all Wi-Fi enabled devices. Wi-Fi repeaters extend the range of the existing network.
Common security concerns: The most relevant security concerns for Wi-Fi networks are:
- Data capture
- On-path attacks
- Denial of service attacks
Security measures: Wired equivalent privacy (WEP) encryption was designed to protect against casual snooping. Later WPS – Wi-Fi protected setup, WPA – Wi-Fi protected access and WAP2 were introduced. All these options are no longer considered secure.
In 2018, WPA3 was announced as a replacement for WPA2, increasing security and enabling secure authentication on wireless routers.
WPA3-Personal: This is a shared key – everyone uses the same key.
WPA3-PSK: The WPA3 session key is derived from PSK using SAE (simultaneous authentication of equals) to provide stronger defences against password guessing. This allows the access provider and station peers to authenticate each other as part of the handshake process while using cryptographic tools to prevent an attacker from performing an offline password cracking scheme.
Li-Fi
Li-Fi, short for light fidelity, offers an innovative way to connect to the internet using light from lamps, streetlights or LED televisions. Li-Fi uses infrared light or LEDs to transmit data. In addition to being cheaper, safer and faster than Wi-Fi, it does not need a router and just requires you to point your mobile or tablet in direct line-of-sight to the light source to surf the web.
Common security concerns: The major security concerns with Li-Fi technology are:
- Jamming
- Spoofing
- Data modification
- Inability to work without light
Security measures: Li-Fi technology is generally considered to be more secure than Wi-Fi, as light cannot pass through walls like radio waves, and it carries more volume of data at a time. Plenty of security features can be embedded in Li-Fi systems in order to make them more secure, such as encryption and monitoring.
Bluetooth
Bluetooth is a short range communications technology intended to replace the cables connecting portable units while maintaining high levels of security. Each device equipped with a Bluetooth chip communicates via spread-spectrum, frequency-hopping, and a full-duplex signal.
An antenna-equipped chip in each device that wants to communicate sends and receives signals at a specific frequency range defined for short-range communication. To communicate, Bluetooth devices pair with each other to form a personal area network (PAN), also known as a piconet. This process is done through discovery, with one device making itself discoverable by the other device.
Bluetooth is a common mobile connectivity method because it has low power consumption requirements and a short-range signal. One of the most popular communication methods is 802.11 wireless. Point-to-point is a one-to-one connection, involving conversation between two devices. In a point-to-multipoint connection, multiple devices can connect but this doesn’t necessarily mean that you can stream media from two devices at a time.
Common security concerns: Some of the most vital security concerns for Bluetooth technology are:
- Bluejacking: Sending of unsolicited messages to another device via Bluetooth
- Bluesnarfing: Unauthorised access to a Bluetooth-enabled device to steal data from it
Security measures: The security measures that are most effective against these security threats are:
- Update with latest patches
- Monitoring
- Encryption
RFID
Radio frequency identification (RFID) refers to a wireless system comprising two components — tags and readers. The reader is a device that has one or more antennas that emit radio waves and receive signals back from the RFID tag.
There are two types of RFID tags — active and passive tags. An active tag can broadcast a signal over a larger distance because it contains a power source. A passive tag, on the other hand, isn’t powered but is activated by a signal sent from the reader.
RFID uses radar technology, and radio energy is transmitted for bi-directional communication.
Common security concerns: Major security concerns hounding RFID technology include:
- Data capture
- Spook reader
- Signal jamming
- Decrypt communication
Security measures: The measures having the most impact on RFID security concerns are:
- Cryptography
- Blocker tags; these prevent unauthorised readers
RFID is commonly used as a geofencing security measure to define a geographic perimeter. When the device enters or exits the perimeter, alerts are sent through this technology.
NFC
Near-field communication (NFC) is a set of standards for contactless communication between devices. NFC chips in mobile devices generate electromagnetic fields. This allows a device to communicate with other devices. NFC is an extension of RFID technology.
Near-field communication transmits data through electromagnetic radio fields to enable two devices to communicate with each other. To work, both devices must contain NFC chips, as transactions take place within a very short distance. NFC-enabled devices must be either physically touching or within a few centimetres of each other for data transfer to occur.
NFC began in the payment-card industry and is evolving to include applications in numerous industries worldwide.
The NFC standard has three modes of operation.
- Peer-to-peer mode: Information shared is exchanged between two mobile devices directly.
- Read/write mode: An active device receives data from a passive device.
- Card emulation: The device is used as a contactless credit card.
It emulates a payment card or other physical card in card readers, magnetic-stripe readers, and contactless card readers used to make payments directly from your mobile device.
Common security concerns: The most relevant security concerns for NFC technology are:
- Remote capture
- Frequency jamming
- On-path attacks
- Loss of NFC device control — digital pick-pocketing
Security measures: The security measures that most effectively handle NFC security concerns are:
- Encryption
- Up-to-date patching at all times
- Turning it off when not in use
Mobile networks
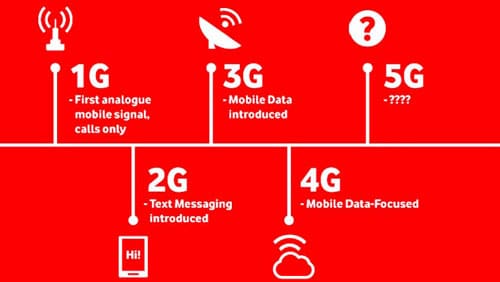
Mobile networking has evolved significantly since the introduction of the first-generation (1G) mobile network in the 1980s. G refers to generation. Each generation is defined as a set of telephone network standards, which detail the technological implementation of a particular mobile phone system.
1G: 1G was the first generation of wireless cellular technology. It was analogue and supported voice calls only. The maximum speed of 1G was 2.4Kbps.
2G: 2G introduced digital technology and the ability to send SMS (short message service) and plain text-based messages. GSM and CDMA were also introduced during this period. The maximum speed of 2G with general packet radio service (GPRS) was 50Kbps. The maximum theoretical speed was 384Kbps with enhanced data rates for GSM evolution (EDGE).
Before making the major leap from 2G to 3G wireless networks, the lesser-known 2.5G and 2.75G were interim standards that bridged the gap.
3G: 3G enabled web browsing, email, video downloading, picture sharing, and so on. The maximum speed of 3G was around 2Mbps for non-moving devices and 384Kbps for devices in moving vehicles.
4G: 4G applications include amended mobile web access, IP telephony, gaming services, high-definition mobile TV, video conferencing, 3D television, and cloud computing. The maximum speed of a 4G network when the device is moving is 100Mbps. The speed is 1Gbps for low-mobility communication such as when the caller is stationary or walking.
5G: 5G promises significantly faster data rates, higher connection density, much lower latency, and energy savings, among other improvements. It offers data transfer rates of up to 20Gbps, and allows users to download ultra-high-definition videos and access the internet at lightning-fast speeds. It also offers lower latency, better network coverage, and improved call quality.
Wireless carriers
Wireless carriers are cellular technology companies that provide mobile telecommunications services for supported devices.
CDMA: CDMA stands for code division multiple access. It is a handset-specific technology. CDMA is not very common, and is available in comparatively fewer carriers and countries. These devices are exclusive to Canada, Japan, and the United States.
The CDMA technology does not support transmission of voice and data simultaneously. It is faster, provides better security and comes with built-in encryption.
GSM: The GSM (global system for mobile) standard was launched by AT&T in Finland. Every device uses SIM (subscribers identity module) to communicate with the provider network.
GSM is highly available and globally used. Over 80% of the entire world’s mobile networks use it. It uses time-division multiple access (TDMA) and frequency-division multiple access (FDMA). GSM supports the transmission of both voice and data at once. It is slower, less secure, and has no default encryption compared to CDMA.
LTE: Long-term evolution (LTE) is used for faster data transfer and higher capacity. Different variations of LTE networks exist across carriers that use different frequencies. For example, Sprint, T-Mobile, Verizon, and AT&T all have their own bands of LTE.
LTE moves large packets of data to an internet protocol system (IPS). Old methods like CDMA and GSM only transferred small amounts of data.
Both LTE and 4G evolved together, with LTE being the industry standard for the forward edge of the fourth generation’s advancement.
4G LTE functionality has two key preconditions: a network that supports the ITU-R (ITU Radiocommunication Sector) standard speeds, and a device powerful enough to match and handle the speeds of that network.
Both GSM and CDMA have switched to LTE as the global 4G standard.
SATCOM: For users who lack traditional landline or cellular coverage, satellite communication (SATCOM) is an option for mobile device use. It uses an artificial satellite to transmit radio signals covering far greater distances and wider areas than most other radio technologies.
Satellite phones function in remote locations as they do not rely on phone transmission lines or cellular towers. Most satellite phones have limited connectivity to the internet, and data rates tend to be slow, but they come with GPS capabilities to indicate the user’s position in real time.
Mobile management
Mobile management is all about keeping your devices and data safe — from mobile device management (MDM) that sets access policies to mobile content management (MCM), which secures data.
Mobile device management (MDM): Managing mobile device access and usage in an organisation is a security challenge, where company-owned or user-owned mobile devices are centrally managed. This includes setting policies on apps, camera usage, data, access, and so on. It also focuses on access control features such as screen locks, multi-factor authentication, remote wipe and geofencing.
Mobile content management (MCM): Mobile content management secures the content present on mobile devices; it involves monitoring and restrictions on file sharing, online content viewing, and uploading.
It also entails centralised data management using solutions such as Microsoft Office 365. It implements data loss prevention (DLP) to prevent any sensitive information leakage, encrypts data on the device, and restricts and blocks external or removable drives.
Mobile application management (MAM): Managing mobile apps is challenging, as not all applications are secure and some may be malicious. MAM ensures that any new application installed is managed through proper channels. This way, only apps with the right permissions are allowed to be installed.
Not all applications are dangerous but those that are not required for business, such as games and social media apps, are denied installation.
Unified endpoint management (UEM): UEM is an evolution of MDM, managing both mobile and non-mobile devices. Through UEM, end users can use different types of devices. Applications can be used across different platforms.
Mobile protection measures
Mobile protection measures are like your device’s personal bodyguards, ensuring its safety.
Remote wipe: Managed by MDM, remote wipe removes all the data from the device, usually during theft, necessitating proper data back-up.
Geolocation: This uses location tracking systems for various purposes, including during commute, cross-border alerts and finding lost phones.
Geofencing: This involves implementing restrictions on mobile features when the device is present in a particular location, with authentication and login allowed only within designated areas.
Screen lock: Mobiles are secured using a PIN, passcode, or biometrics, with auto-lock features after a configured time, and data erasure after multiple invalid entries.
Push notification services: This is an information pop-up service on the screen, receiving notifications even when the phone is idle or is using a different application.
Passwords, PINs and biometrics: This involves multi-authentication for mobile devices based on the apps used, managed through MDM, with password rotation, reset and complexity policies.
Context-aware authentication: This helps switching to multi-level authentication when abnormalities are observed, such as access through different locations, different Wi-Fi connections, or paired Bluetooth devices.
Containerisation: This segments storage for business use to avoid data leaks and facilitate easy offboarding, while retaining personal data.
Full device encryption: This ensures data security even after its theft, with keys managed and rotated through MDM.
MicroSD hardware security module (HSM): This provides security services like encryption, key generation, rotation, digital signatures, and encrypted key storage.
SEAndroid (Security Enhancements for Android): This is built using SELinux (Security Enabled Linux) with centralised policy management. It ensures devices are patched with the latest security fixes.
Mobile deployment models
Enterprise mobile device deployment models fall into any of the following categories.
BYOD (Bring Your Own Device): Employees own the device, which can be challenging to secure, and containerisation through MDM can be used to manage corporate data.
COPE (Company Owned/Personally Enabled): Company buys the device, which is for both professional and personal use. The organisation has full control on the device, including monitoring.
CYOD (Choose Your Own Device): Similar to COPE, these are corporate-owned devices where the user selects the mobile device. This can get tricky in terms of security for certain models.
COBO (Company Owned/Business Only): Company buys devices and uses them only for official purposes with specific restrictions.
VMI (Virtual Mobile Infrastructure): Apps and data are separated from the mobile device. Data is stored securely in a centralised location to minimise risk.
Mobile security, along with other general security measures, plays a crucial role in ensuring the safety of enterprises and individuals in the rapidly evolving digital landscape. By employing robust mobile management and protection measures, businesses can safeguard sensitive data and mitigate potential threats effectively.