Embark on your Istio journey, and revolutionise the way you orchestrate microservices in a Kubernetes environment.
Orchestrating seamless communication, fortifying security, and achieving observability pose key challenges in the world of containerised applications and microservices. Enter Istio, an open source service mesh platform designed to tackle these complexities. This article serves as a comprehensive guide, taking you through the essential steps to embark on your Istio journey—from the initial setup to the exploration of its advanced features.
A service mesh is a decentralised infrastructure that ensures secure, reliable communication between microservices by employing service proxies. These proxies, deployed with each application instance, facilitate routing, security, and policy application consistently. Istio, an open source service mesh, simplifies microservices management in cloud-native applications. It enables intelligent routing, resilience against failures, policy enforcement, and observability. Istio secures service-to-service communication with features like mutual TLS (mTLS), offering a comprehensive solution for optimising and securing microservices architecture.
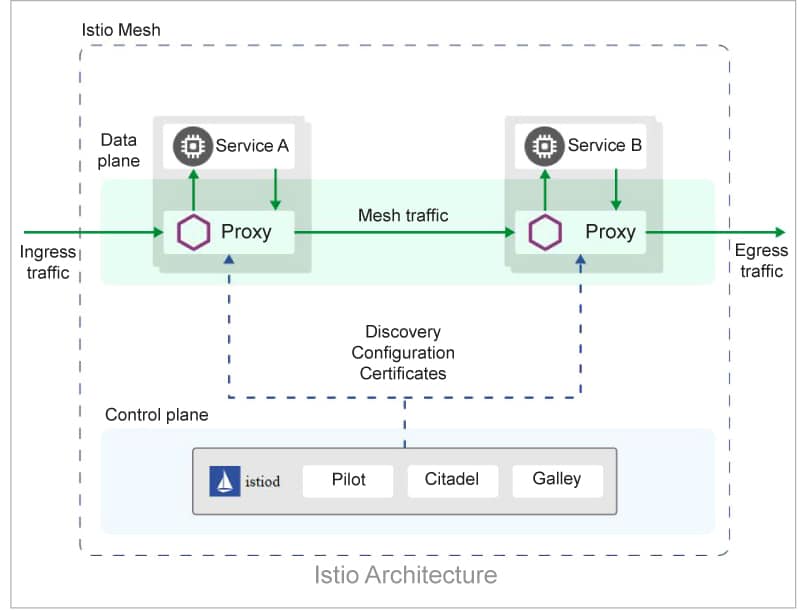
Istio architecture
Istio’s architecture consists of data plane and control plane components. The data plane employs Envoy proxies, sidecar containers alongside microservices, managing traffic, security, and observability. The control plane, comprising Pilot, Citadel, Galley, and Mixer, centrally configures and enforces policies. Pilot disseminates routing rules, Citadel handles security with mTLS, Galley validates and processes configurations, and Mixer collects telemetry data. This architecture ensures seamless communication, security, and observability in a microservices environment, empowering developers to efficiently manage and optimise their applications within a service mesh paradigm.
Prerequisites for setting up Istio
Kubernetes cluster: Elevate your platform
Before delving into Istio, ensure you have a thriving Kubernetes cluster. For quick testing and development, tools like minikube or kind can swiftly set up a local cluster.
kubectl: Your command centre
Equip yourself with kubectl, the Kubernetes command-line tool, to seamlessly navigate and interact with your Kubernetes cluster. Find detailed installation instructions on the official Kubernetes documentation.
Helm: The navigator
Harness the power of Helm, the Kubernetes package manager, for streamlined deployment and management of applications. Detailed installation instructions are available on the Helm GitHub repository.
Installation
Download Istio: Gateway to excellence
Embark on your Istio journey by visiting the official website (https://istio.io/latest/docs/setup/getting-started/#download). Download the Istio release tailored for your platform and extract the files to a location of your choosing.
Install Istio: A seamless onboarding
Navigate to the Istio directory in your terminal and initiate the Istio installation with the following command:
istioctl install
This single command deploys the Istio control plane, incorporating pivotal components such as Pilot, Citadel, Galley, and the Ingress Gateway.
Verify installation: Ensuring a solid foundation
Post-installation, use the following command to confirm that the Istio components are up and running:
kubectl get svc -n istio-system
Ensure all services in the Istio system name space, including istio-ingressgateway and istiod, boast a status of running.
Deploy sample application
‘Bookinfo’ sample app — Unveiling the possibilities: Istio comes bundled with a compelling showcase—’Bookinfo’. Deploy this sample application and witness the orchestration of multiple microservices:
kubectl apply -f https://istio.io/latest/docs/examples/bookinfo/platform/kube/bookinfo.yaml
Enable Istio sidecar injection — Powering communication: Label the default name space to effortlessly enable automatic sidecar injection—a crucial Istio feature facilitating communication between microservices:
kubectl label namespace default istio-injection=enabled
Access application — Gateway to success: Retrieve the external IP of the Istio Ingress Gateway using:
kubectl get svc -n istio-system istio-ingressgateway
With this external IP, access the Bookinfo application and bask in the seamless integration afforded by Istio.
Istio features
Traffic management: Orchestrating precision
Unlock the potential of Istio’s traffic management. Modify virtual services and destination rules to wield control over traffic routing and splitting. Perfect for conducting A/B testing and executing canary deployments with finesse.
Security: Fortifying the citadel
Dive into Istio’s security arsenal, featuring mTLS and robust access control policies. Enable automatic encryption of microservices communication with mTLS and implement policies to govern access based on predefined rules.
Observability: Illuminating insights
Leverage Istio’s observability tools to gain deep insights into your microservices. Seamlessly integrate with Grafana and Prometheus for comprehensive dashboards and metrics. Visualise your service mesh topology with Kiali, and trace transactions across microservices using Jaeger.
Canary deployments: Navigating transitions
Implement canary deployments effortlessly with Istio’s traffic shifting capabilities. Gradually transition traffic between different versions of microservices, ensuring a smooth rollout and minimal user impact.
Clean-up
As you conclude your exploration, maintain a tidy environment by executing the following commands:
kubectl delete -f https://istio.io/latest/docs/examples/bookinfo/platform/kube/bookinfo.yaml istioctl x uninstall --purge
This guide is your compass for navigating the vast landscape of Istio. As you delve deeper into this service mesh, explore the extensive documentation (htps://istio.io/latest/docs/) for advanced configurations and best practices. Istio empowers you to unlock the full potential of your microservices architecture—ensuring resilience, security, and observability at scale.













































































