Monthly Archives: January 2011
Understanding a Kernel Oops!
Understanding a kernel panic and doing the forensics to trace the bug is considered a hacker's job. This is a complex task that requires...
Do You Know the Trick to Track Your Code’s DNA?
You can now manage the source code for software-related product development in your organisation, using the Black Duck Suite, which among other capabilities, generates...
Device Drivers, Part 3: Kernel C Extras in a Linux Driver
This article in the series on Linux device drivers deals with the kernel's message logging, and kernel-specific GCC extensions.
Enthused by how Pugs impressed their...
Securing Apache, Part 5: HTTP Message Architecture
In the last four articles in this series, we have discussed SQL injection, XSS, CSRF, XST and XSHM attacks, and security solutions. This article...
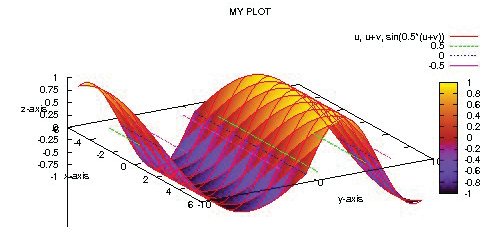
Plotting is Fun with GNUPlot
This article explores the use of GNUPlot for scientific plotting, along with examples.
While strings and pages of data seem cryptic, a plot reveals the...
Handling Interrupts
In my last article, we explored the concept of interrupts and how they catch the CPU's attention. In this article, we will look at...
phpVirtualBox — Accessing VirtualBox from a Browser
This article introduces phpVirtualBox, an open-source, AJAX and PHP-based implementation of the Oracle VirtualBox user interface
Advanced Nmap: FIN Scan & OS Detection
Nmap is a fantastic tool, and I just can't refrain from praising it, every time I use it. The earlier articles in this series...
Aircrack-ng: Wi-Fi Troubleshooting, Auditing and Cracking Made Easy
Wi-Fi technology has today become almost ubiquitous for wireless local area networks at offices, restaurants, homes, airports, hotels, etc. However, with increased Wi-Fi usage...
Puppet Data Centre Automation Solution, Part 3: Resource Types & Example Configs
The previous article in this series focused on creating users, groups and files (based on home directories). Let's now look at the various types...