Home 2010
Yearly Archives: 2010
Accessing a Home Laptop Remotely from Android
Consider this: You're on vacation in the Maldives, when your office calls, with an urgent request for some files and information. These happen to...
Securing Apache, Part 3: Cross-Site Request Forgery Attacks (XSRF)
Intended for information security experts, systems administrators, and all those concerned about Web security, this third article in the series moves on from SQL...
Kernel Tracing with ftrace, Part 1
This article explains how to set up ftrace and be able to understand how to trace functions. It should be useful for current kernel...
‘Featuristic’ Linux Load Balancing with LVS
This article deals with setting up LVS (Linux Virtual Server) for clustering on SUSE. Also discover how it acts as a scalable and high-performance...
Puppet Data Centre Automation Solution, Part 1: Setting Up Master & Client
Managing data centres comprising hundreds of systems is tough. Fortunately, configuration-management systems help bring things under control, by automating common configuration tasks, making systems...
Get Started with Turnkey Linux — When and Where it Makes Sense
This article deals with getting open source software packages up and running on bare metal/virtual platforms in a stress-free manner.
What happens when your online...
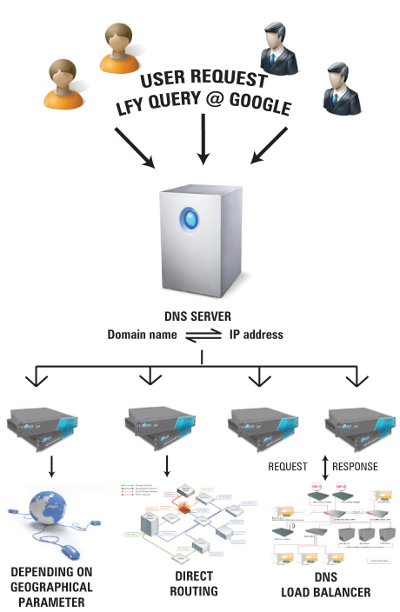
Advanced NMap: Some Scan Types
A broad overview and the basic features of NMap have been covered in an earlier article in this series of articles on Nmap. In...
Joy of Programming: Logical Bugs and Intuitive Thinking
Logical bugs are very common in code and are often very difficult to find and fix. In this column, we'll look at an example...
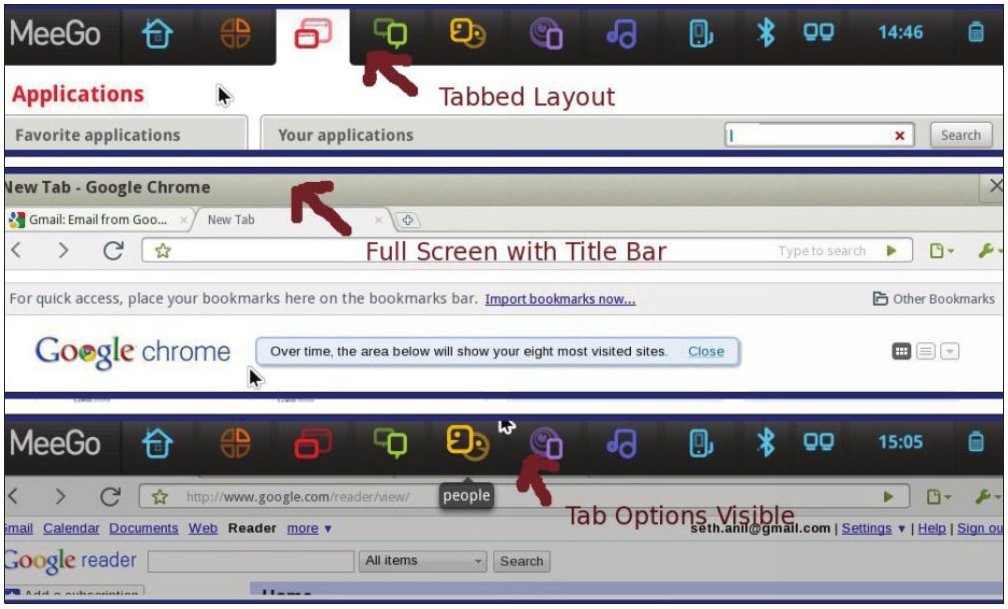
Exploring Software: Netbook Operating Systems
A modern netbook is likely to have 150 GB of disk space, 1 GB of RAM, a screen resolution of 1024×800 pixels, and a...
CodeSport
Welcome to CodeSport! In this column, we provide the solutions to a few of the questions we had featured last month.
Last month's column featured...