Dynamic application security testing (DAST) focuses on finding security vulnerabilities in a web application while it is running. This article looks at Acunetix and GuardRails, which are two popular DAST tools.
Security controls are integrated into the DevOps process through a method called DevSecOps. This includes integrating security early in the software development life cycle (SDLC). Additionally, DevSecOps enhances cooperation between the development and operations teams by including security teams into the software delivery process. Security becomes a shared responsibility under DevSecOps, which calls for changes in technologies, processes, and culture across the SDLC key functional teams. The DevOps continuous integration and continuous delivery (CI/CD) process must incorporate security, and everyone participating in the SDLC has a part to play.
Testing, triage, and risk mitigation should be included early in the CI/CD workflow to avoid the time-consuming and frequently expensive consequences of making a patch after the event. This idea is a component of ‘shifting left’, which brings security testing closer to programmers so that they may address security flaws in their code almost immediately rather than ‘bolting on security’ at the end of the software development life cycle (SDLC). DevSecOps integrates real-time continuous feedback loops and insights throughout the whole SDLC, from planning and design through coding, building, testing, and release.
Dynamic application security testing (DAST)
Dynamic application security testing (DAST) is used to investigate a web application and find vulnerabilities using simulated attacks. This type of technique evaluates the software from the ‘outside in’ by attacking an application just as a malicious user might. A DAST scanner looks for results that do not match the intended result set after the execution of these attacks in order to identify security issues. DAST has the advantage of identifying potential security holes without taking the application into account. And it does not require access to the source code. The disadvantages are that it cannot determine the exact position of a code vulnerability and that security knowledge is needed to interpret reports.
Software applications are evaluated using DAST. This testing simulates the actions of a malicious party trying to access an application remotely. Software applications are continuously scanned by DAST for security holes using market-leading vulnerability sources like the Open Web Application Security Project (OWASP Top 10), Common Weakness Enumeration (CWE) and SysAdmin, Audit, Network and Security (SANS). OWASP is a standard document for developers and web security; it includes injection (SQL injections, command injections, CRLF injections, and LDAP injections), broken authentication, sensitive data exposure, XML external entities, broken access control, security misconfiguration, cross-site scripting, insecure deserialization, using components with known vulnerabilities, and insufficient logging and monitoring.
The main difference between DAST and SAST (static application security testing) is how each approaches security testing. SAST scans the application code while it is at rest to look for defective code that provides a security danger, whereas DAST analyses the operational program without having access to its source code.
DAST is a type of closed-box testing that simulates the viewpoint of an external attacker. It is assumed that the tester is unaware of the inner workings of the program. It can find security flaws that manifest themselves only during software runtime.
Acunetix
One of the DAST tools is Acunetix. Although there are numerous tools available today, Acunetix offers a free trial as well as membership services for premium features like speed and accuracy. It is a superior tool that is quick and accurate, and it also has a user-friendly interface that makes it simple to operate and utilise for our website. Acunetix is a program that analyses web applications for exploitable defects like SQL injection and cross-site scripting. It is used to evaluate the security of online applications. Acunetix typically scans any website or online application that may be accessed using a web browser and uses the HTTP/HTTPS protocol.
Acunetix offers a powerful and distinctive approach to evaluating pre-built and bespoke online applications, including those that make use of JavaScript, AJAX, and Web 2.0 technologies. A sophisticated crawler on Acunetix can locate practically any file. This is crucial, because something cannot be verified without being found. Finding a bug is crucial for making a perfect application.
Configuring and working of Acunetix
Begin by downloading Acunetix from the internet. The link is https://acunetix-web-vulnerability-scanner.software.informer.com/download/#downloading. It has a trial version, but is a subscription based application.
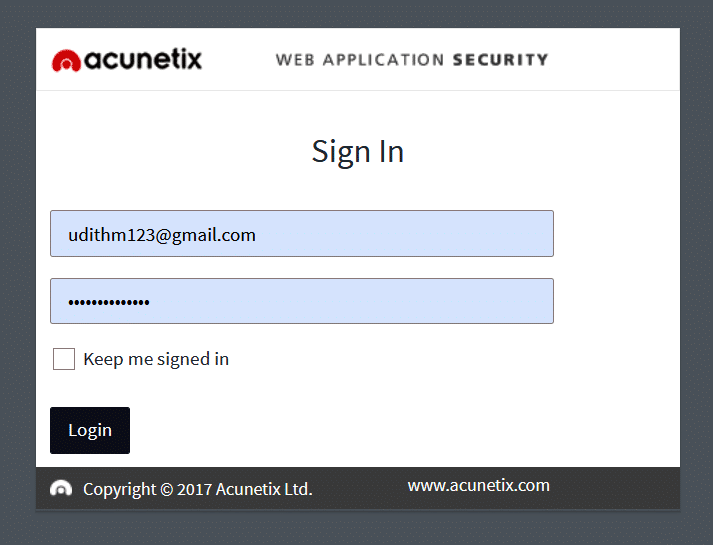
Next, install the application. You need to create a profile with user name and password. We can see the login page in Figure 1.
The application gets opened in ‘13443’ port by default. In case a process is running on that port, you can change it while starting the application.
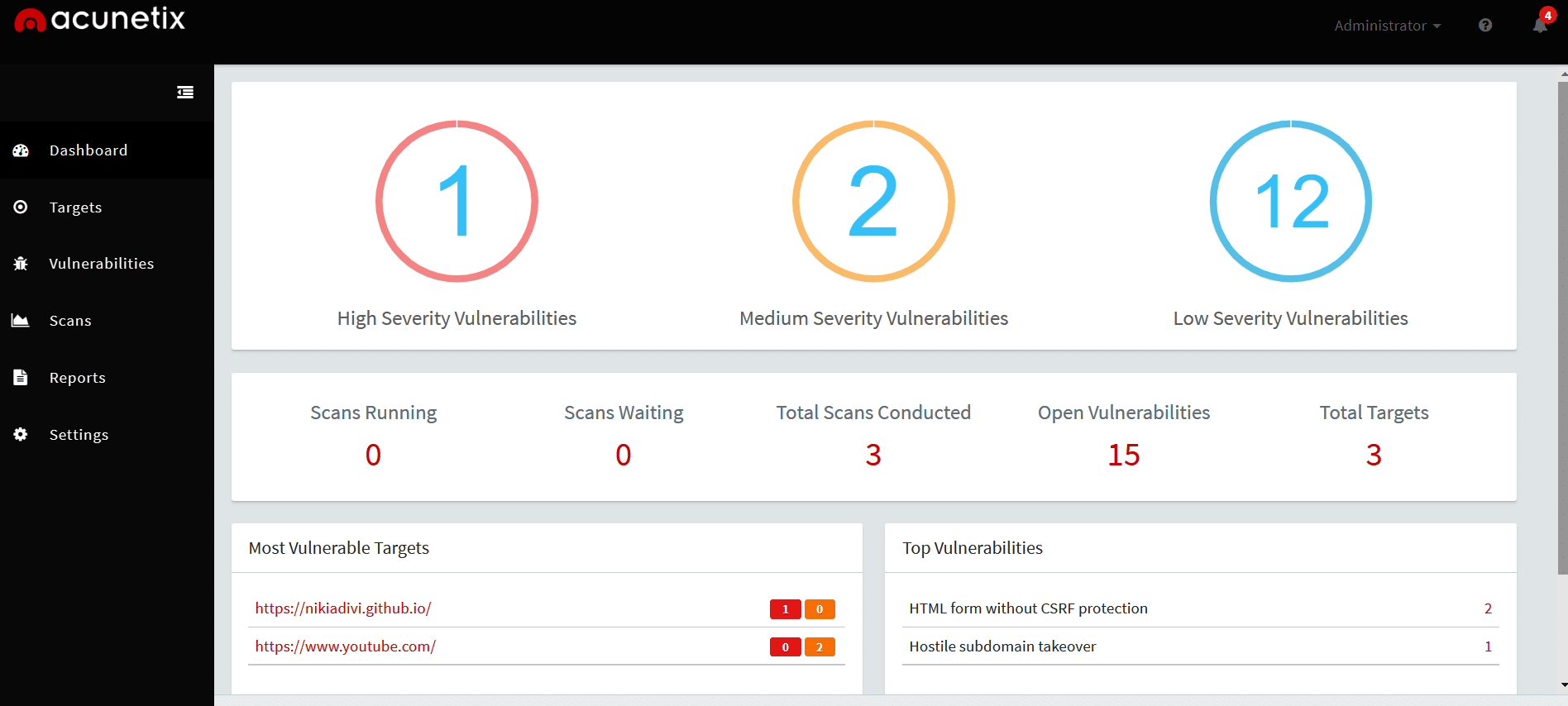
After you log in, you will be taken to the dashboard, where you can see your overall test results. Figure 2 shows an example of a dashboard.
For running a new scan, go to Targets and then click on ‘Add Target’. A pop-up appears as shown in Figure 3.
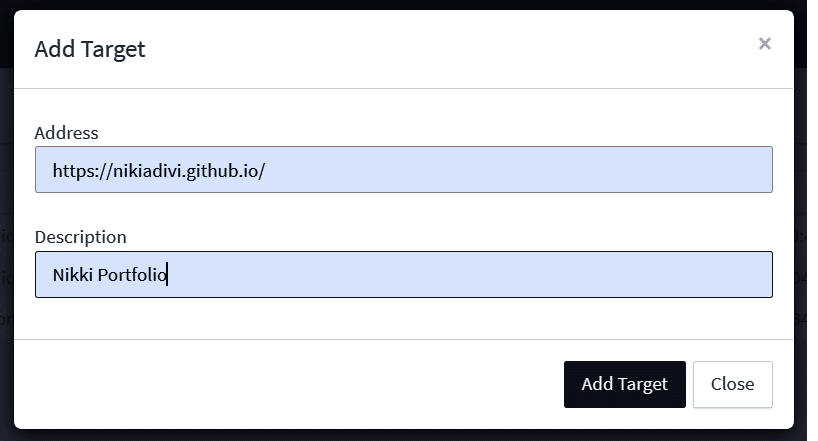
Enter the hosted address of the application and description. Then click on ‘Add Target’.
After adding Target, you will be taken to a page where you can select scan speed, and business criticality. Next, you can give the instructions to log in. Figure 4 gives an image of the page.
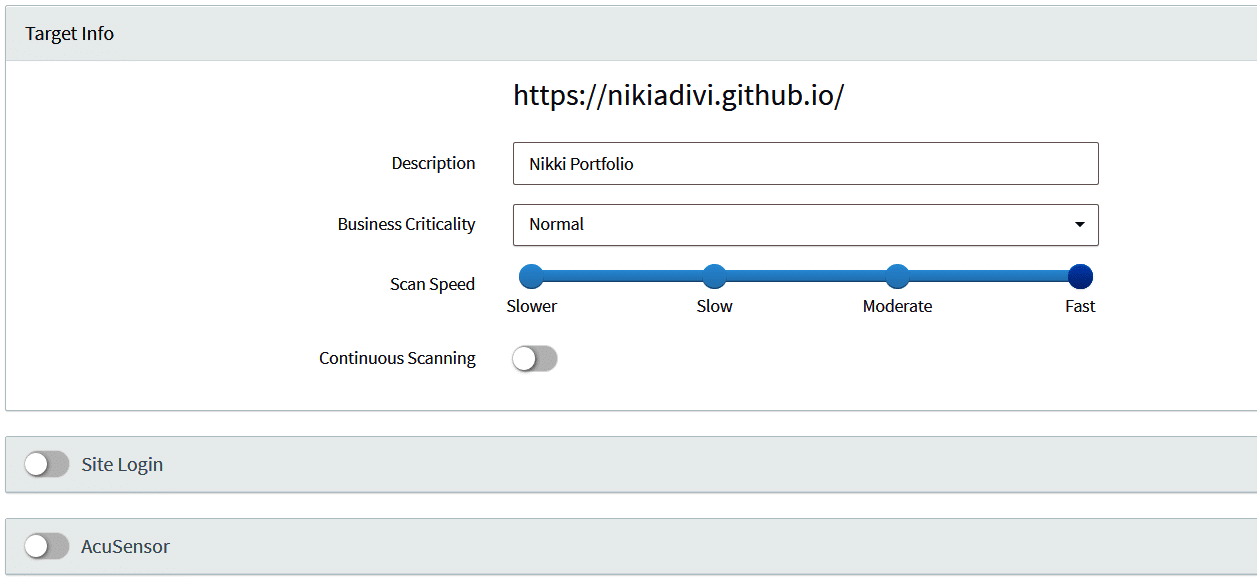
You can either give user name and password or give instructions on the flow of the login. Figure 5 shows the login instruction settings page.
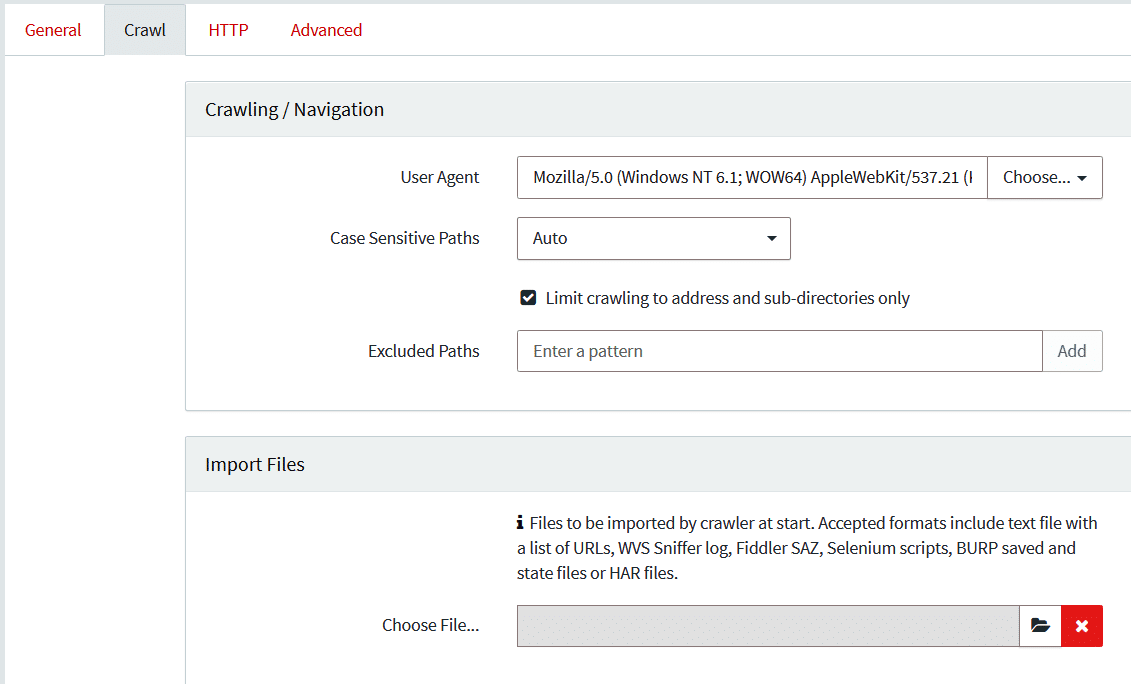
Some of the default settings will be taken based on the website and we can change these if we want to. We can select the type of browser to check the application in, and if we want to exclude any paths we can mention that in the settings. Figure 6 shows the crawl settings.
There are some HTTP and advanced settings that we can control according to our requirements. Figure 7 shows the HTTP settings and Figure 8 shows the advanced settings.
After we have selected the required setting, click on ‘Scan’. Then the pop-up shown in Figure 9 comes up.
We can select the type of scan based on our requirements. We can schedule scans like instant scan, scheduled scan or a recurring scan.
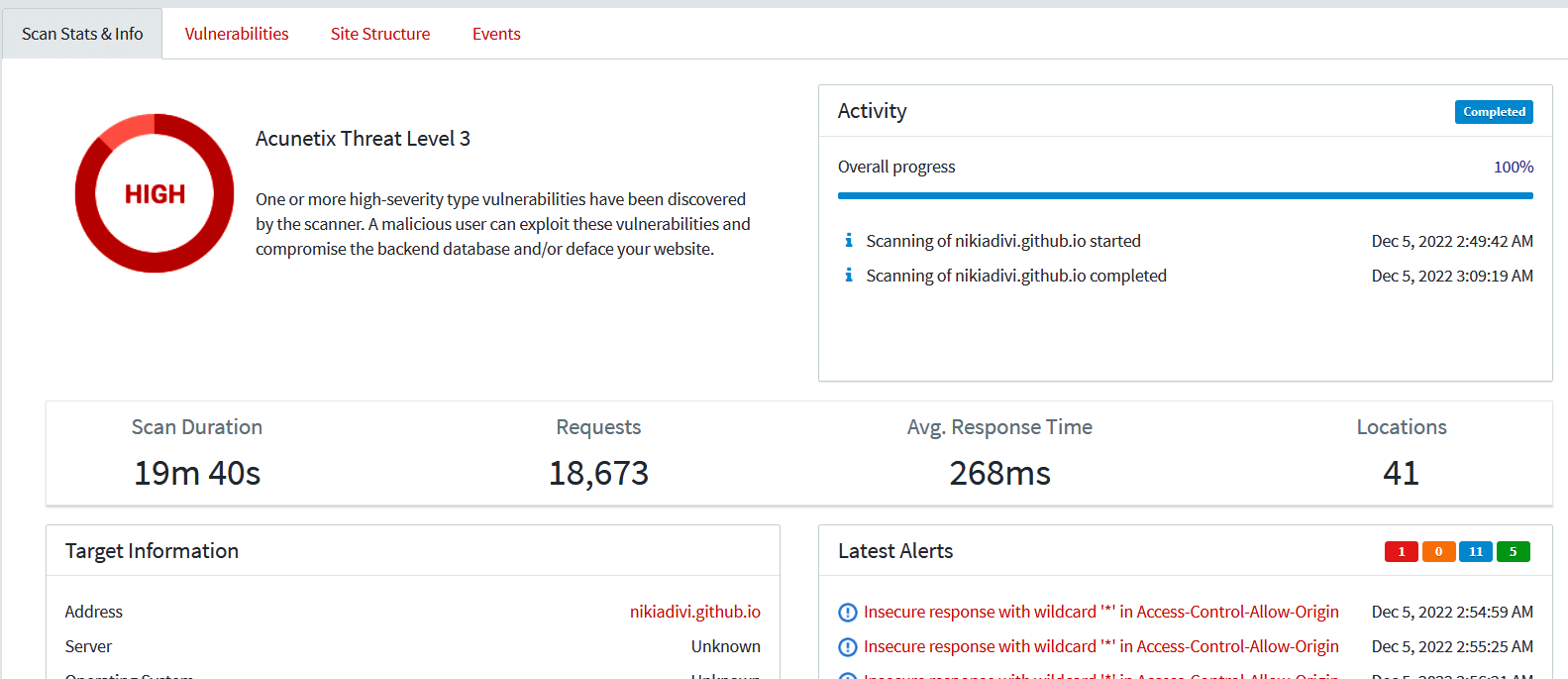
After selecting the scan, click on ‘Create scan’. Figure 10 shows the report of the scan.
There will be four levels of security, and the applications classify all the vulnerabilities into those levels. You will get the results on completing the scan.
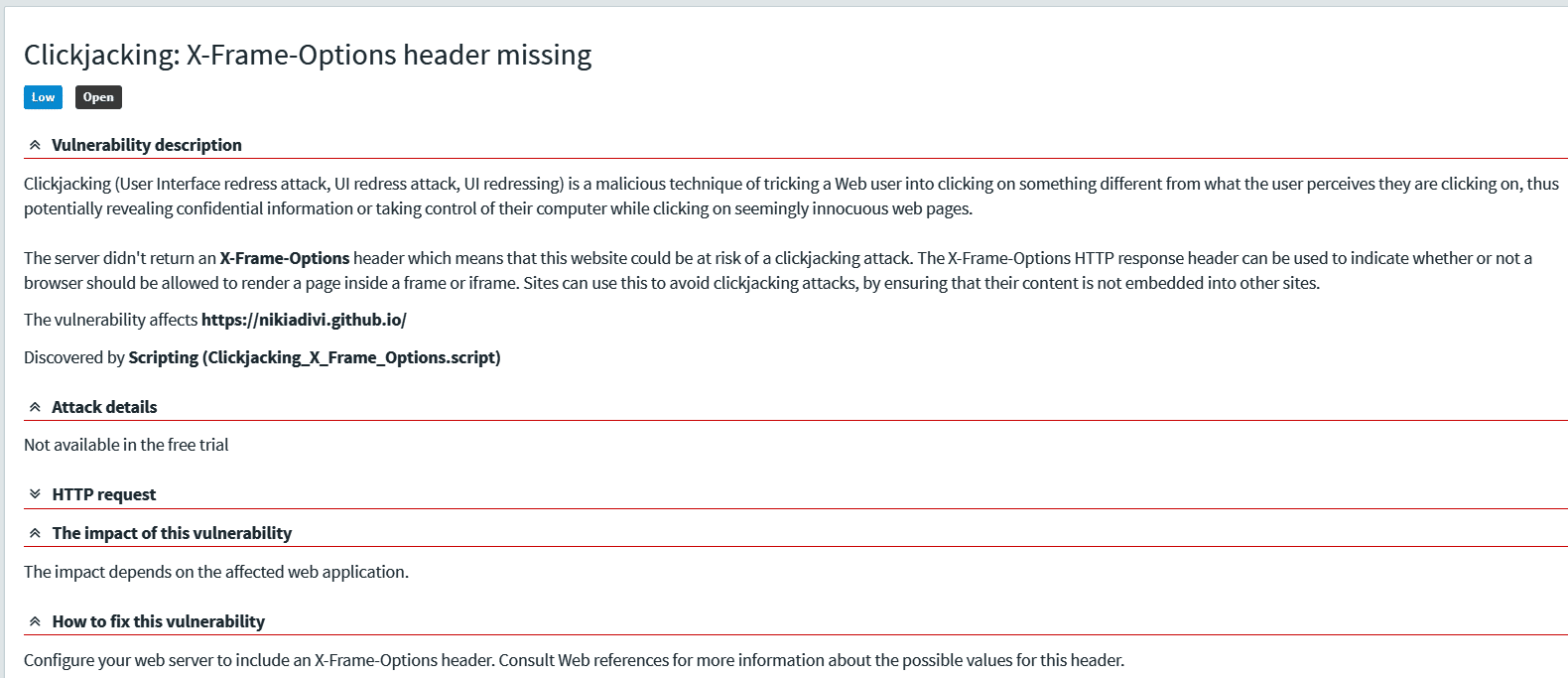
You can select a vulnerability to find out the problem. Figure 11 gives an example of a vulnerability report.
GuardRails
GuardRails manages the usage of open source and commercial security tools by seamlessly integrating them into your current development workflow. It carefully picks each security rule of the security tools in order to minimise noise and only report high-impact and important security problems. Installing and setting up security technologies may be time-consuming and difficult, even for a single repository. GuardRails streamlines, accelerates, and rewards that process for developers.
It only takes a few minutes to install GuardRails across all your repositories. Once engaged, GuardRails examines all new code updates to look for security flaws before demonstrating to users in detail how to fix them.
GuardRails is different from other solutions in four key areas:
- Version control system integration
- Security tool orchestration
- Security rules curation
- False positive detection
Configuration of GuardRails
Since it is a web application there is no need to install any application on our local computer. Just go to the website and login either with GitHub, GitLab or Bitbucket. The link is https://dashboard.guardrails.io/login.
After logging in with your account, give permission from your GitHub or other platforms to access your repo from GuardRails.
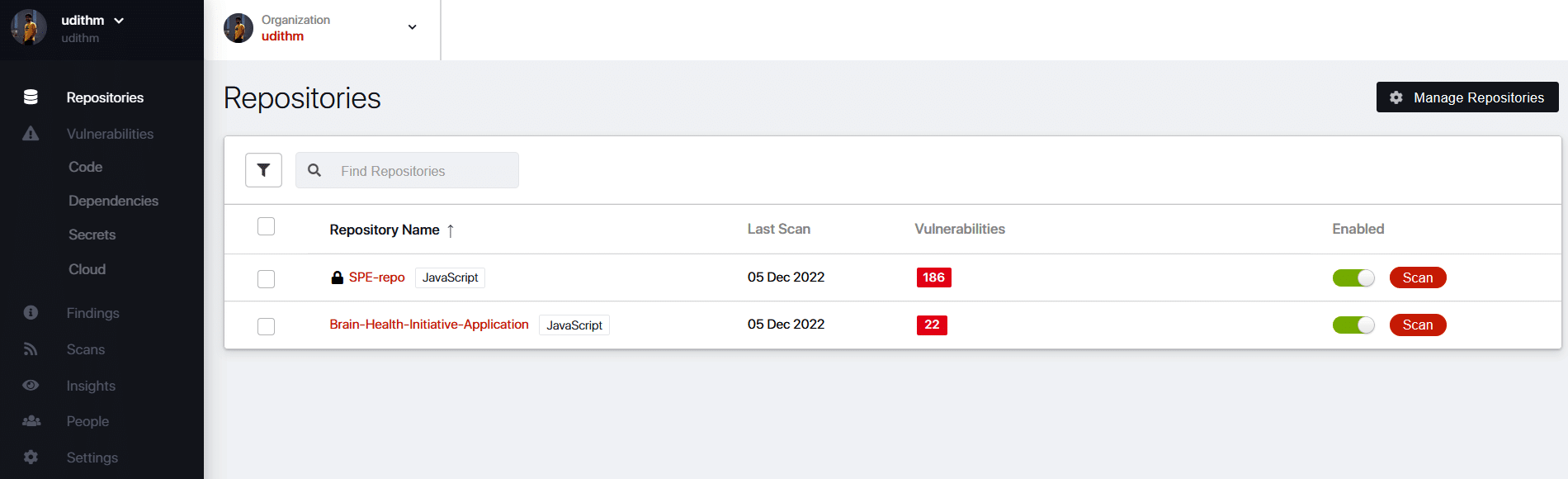
Once your repo is added, it will be displayed on the dashboard, as shown in Figure 13.
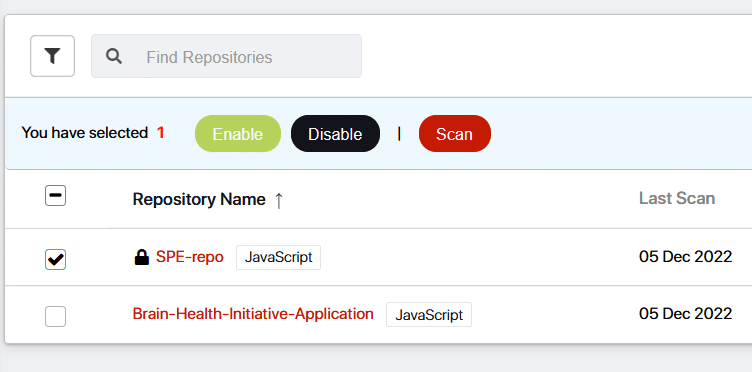
You can now select the repo you want to scan, and select ‘scan’ as shown in Figure 14.Figure 14: Select the repo to scanFigure 14: Select the repo to scanFigure 14: Select the repo to scan
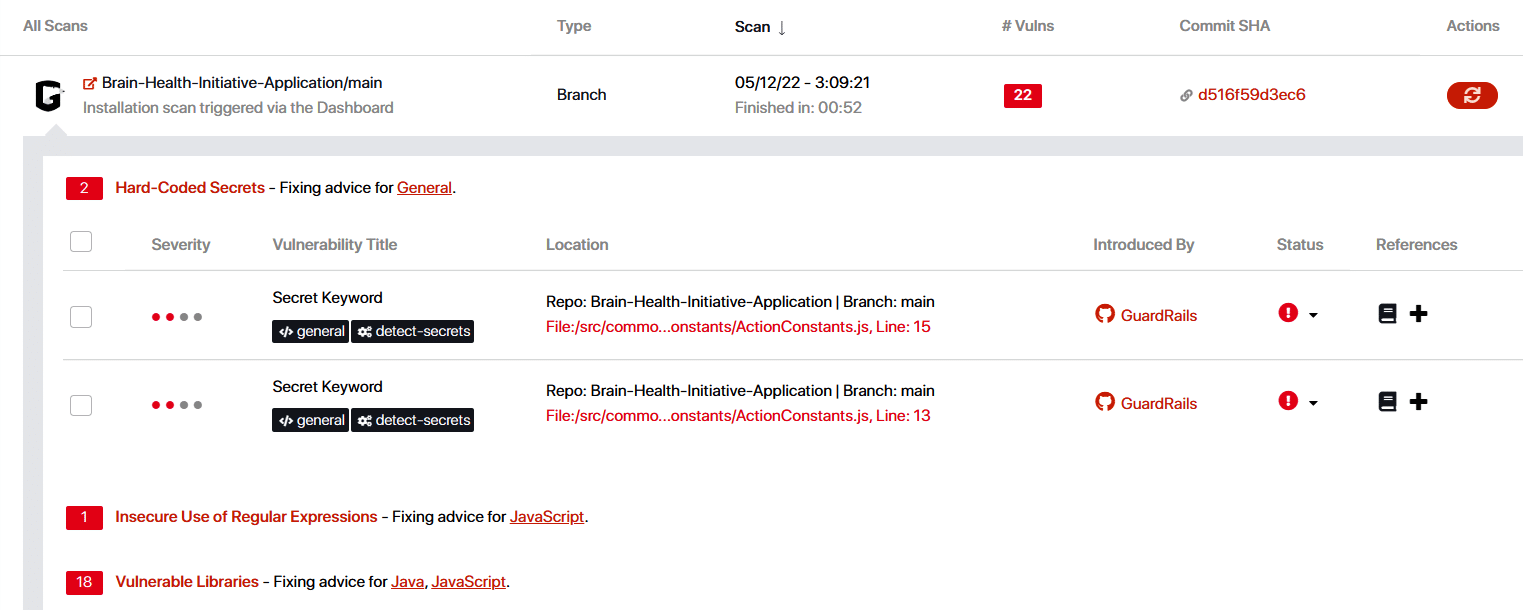
After the scan is done, you will get a report with all the vulnerabilities given in three levels. An example report is shown in Figure 15.
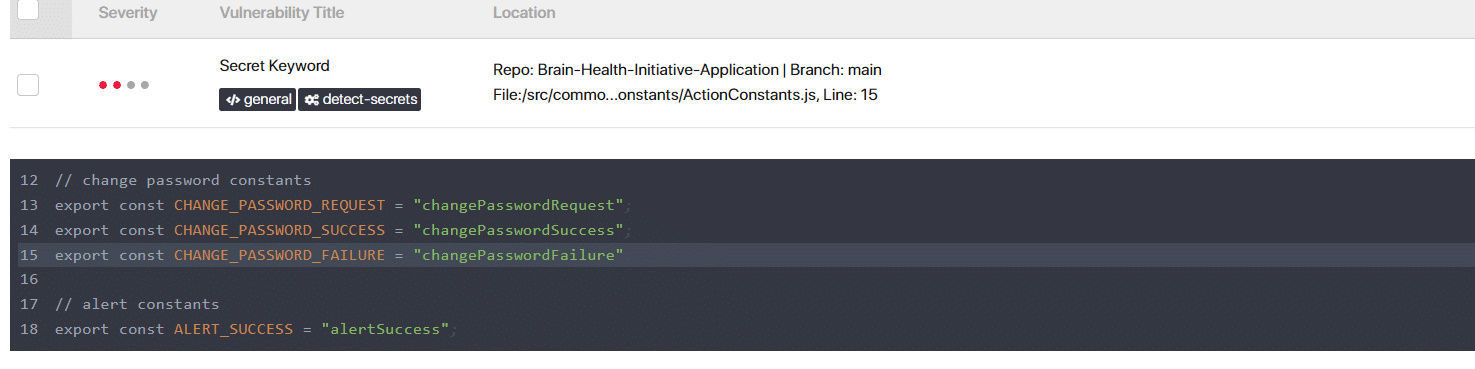
You can also select any vulnerability and get the details of where the problem has been identified (Figure 16).
After you verify the problem in the code and rescan it, it won’t be shown again if solved.
Nuclei
An upcoming open source DAST tool is Nuclei. It is an application that needs to be downloaded and installed on our local computer.
Using a template, Nuclei is used to deliver queries across targets, producing no false positives and providing rapid scanning on many hosts. Nuclei scans a wide range of protocols, including TCP, DNS, HTTP, SSL, File, Whois, WebSocket, Headless, etc. It enables complex and flexible templating, which may be applied to represent different security checks.
The reference for the nuclei repository is https://github.com/projectdiscovery/nuclei.
The security tools covered in this article are efficient and easy to integrate with the development pipeline. Acunetix and Guardrails showcase cutting-edge technologies that are constantly improving due to their intuitive user interfaces, deeper feature sets, quick testing, and enhanced efficiency. In contrast to Guardrails, which is immediately connected to GitHub or other accounts where it is simple to access projects, Acunetix requires installation and a subscription edition for additional capabilities. Nuclei is also being used frequently and helping to fix security related issues in developed software.