IoT (Internet of Things) and IoT devices are evolving to enhance productivity and efficiency in a range of industries, as well as ensure more security of data.
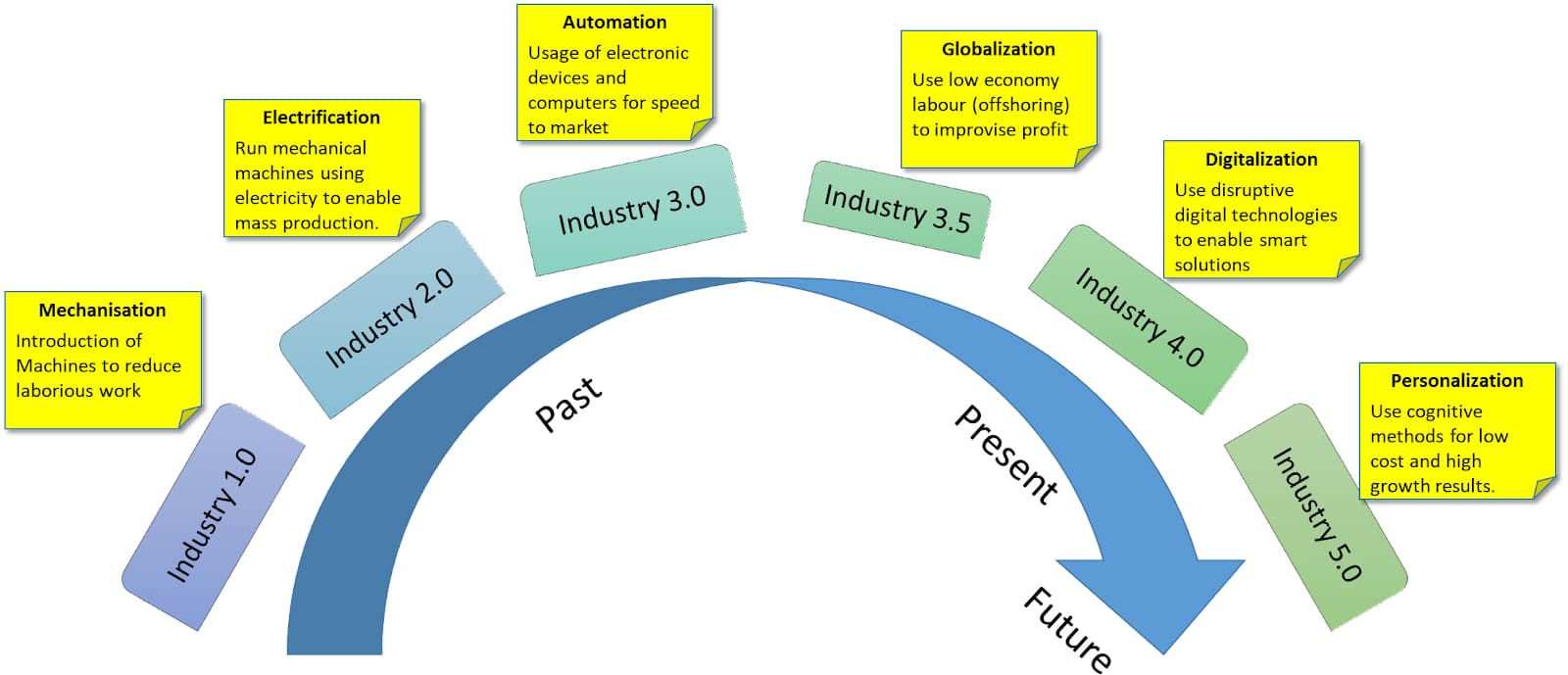
The human lifestyle evolves with each social, economic and technological revolution. In recent times, Industry 4.0 has harnessed technology (including cloud platforms, IoT-connected devices, blockchain-enabled crypto transactions, and digital twins) to enhance mass production. One drawback of Industry 4.0 adoption is its focus on either efficiency or productivity. In an efficiency-driven solution, the aim is cost optimisation, resource management, and waste reduction. In a productivity-driven approach, the focus in on reducing time to market and operational overheads.
Industry 5.0 has emerged to address these shortcomings of Industry 4.0. For example, Industry 4.0 introduced robotic automation for improved efficiency and quality of service. Now, in Industry 5.0, we will employ cobots or collaborative robots designed to work closely with humans.
Industry 5.0 also aims not to replace human efforts but to support them, focusing on the quality of service along with cost, resource, and effort optimisation. It seeks to improve customer relations with contact center AI, interactive bots, mixed reality-based immersive customer experiences, and a responsive and distributed supply chain for seamless collaboration with teams.
However, the transition to Industry 5.0 is challenging and demands advancements in IoT, connected communication, cloud-based scalable business solutions, IoT-enabled data transmission and management, hyper automation for operational maturity models, and immersive user interactions.
Business context of IoT services
When the Internet of Things (IoT) is applied to different sectors, new terms and definitions emerge, such as IoMT, IoDT, IoVT, IoIT and IoRT. Each of these simplifies some complex business and technical requirements. Let’s explore these terms.
- Internet of Medical Things (IoMT) – Commonly used for technology solutions combined with sensors for health monitoring and remote patient monitoring in the healthcare industry
- Internet of Drone Things (IDT) – Utilises drones and unmanned aerial vehicles (UAV) for applications like agriculture, wildlife monitoring, evacuation drills, and industrial site monitoring
- Internet of Digital Twins (IoDT) – Replicates human-like virtual assistants, robotic assistants and chatbots to aid end users, e.g., virtual banking assistants for financial advisors
- Internet of Vehicle Things (IoVT) – Applied in the automotive industry for digital metaspace to sell cars, simulators for vehicle driving training, and vehicle design using digital canvases
- Internet of Robotic Things (IoRT) – Used in production design to create a low-cost simulated environment that uses robots for inspection, quality tests and training
- Internet of Intelligent Things (IoIT) – Applied in industries like virtual/online retail stores to analyse user patterns and behaviour to provide intelligent services based on machine learning
Internet of Everything (IoE) combines all or some of these services to integrate various processes, using the internet for data handling, as well as specialised devices like head-mounted devices, IoT sensors and monitors, and people with defined roles/responsibilities to handle various business functions.
In simple terms, these services (IoE) are not confined to specific technologies but use various combinations to enhance customer experiences, provide better solutions, and reduce costs for ‘go to market’ solutions across different sectors.
Trends in IoT-enabled application architecture
The latest trends in IoT-enabled application architecture include:
- Blockchain for IoT security: Blockchain technology can secure IoT devices and data by providing a decentralised and tamper-proof system.
- Smart home devices: IoT-enabled smart home devices are gaining popularity, offering remote control and communication with other household devices.
- Cybersecurity priority: With the growing prevalence of IoT devices, cybersecurity becomes increasingly important. IoT-driven software architectures must consider the implications of software complexity, security, and privacy.
- Edge computing rising over cloud computing: Edge computing is gaining prominence due to its ability to process data faster, reducing the need to transmit data to the cloud for processing.
- AI and Big Data significance: IoT is a key source of real-time data for AI applications, enabling AI-driven decisions.
- Complex wearable devices: IoT-enabled wearable devices used for health monitoring and fitness tracking are becoming more complex.
- Microservices architecture adoption: IoT-centric software architecture poses unique challenges, and adopting microservices architecture can help.
Overall, IoT-enabled application architecture must evolve to meet the unique demands and challenges posed by IoT, as emerging IoT devices become the new norm.
Security requirements in IoT-enabled application services
IoT-enabled devices communicate through protocols like Message Queue Telemetry Transport (MQTT), which is an open messaging and lightweight protocol for IoT. This involves personal area networks (PANs) or wide area networks (WANs) connecting multiple data centres through public or private cloud services.
In this network, IoT security on infrastructure components and IoT application security on IoT-enabled edge services (like secure access service edge (SASE)) are important to protect connected devices and application data. Some of the core principles for developing a security strategy for IoT applications and infrastructure services are:
- Data encryption at rest to protect data when it is stored in the data storage or application storage facility. This could be through encryption or device level cipher protection to avoid tampering data access from outside.
- Data encryption in transit or in motion to protect data when transporting through a communication protocol. This could be through secured tunnel or safeguarding network services using secured protocols like SSL, TLS, FTPS, etc.
- Device identity to protect unauthorised devices being connected to IoT network of services. Each device in the IoT implementation is identified through unique device identity. This is used to authenticate (verify device access) and authorise (permit device connection) in the IoT ecosystem of connected devices.
- Protect device authentication through a token-based authentication and authorisation framework like OAuth 2.0.
- Policy management to provide role-based access control, along with user principles and policy definitions to enable device protection facilities in the IoT ecosystem. This will enable access management for all the connected services.
- Two-way protection in all services through certificate based authentication like public key infrastructure (PKI) and organisation-based access control (OrBAC).
When using MQTT for machine-to-machine network communication, it’s essential to ensure device authorisation and data protection. IoT security and IoT application security play critical roles in the IoT ecosystem.
Edge computing for IoT services
Edge computing for IoT services is a distributed computing paradigm that brings computation and data storage closer to data sources, such as IoT devices and sensors. This allows for real-time data processing and analysis, reduced latency, and improved bandwidth efficiency.
Edge computing is particularly well-suited for IoT applications because it can help to address some of the key challenges of IoT, such as:
- Handling large volumes of data: IoT devices generate large volumes of data, which can be costly and time-consuming to transmit to the cloud. Edge computing can help reduce this amount of data by processing and filtering it at the edge.
- Reducing latency: IoT applications often require real-time data processing and analysis in order to make timely decisions. Edge computing can help to reduce latency by bringing computation closer to the sources of data.
- Improving reliability: IoT devices are often deployed in remote or harsh environments where network connectivity may be unreliable. Edge computing can help to improve reliability by allowing IoT devices to continue operating even when they are not connected to the cloud.
Edge computing for IoT services can be used to implement a wide variety of applications, including:
- Real-time monitoring and control: Edge computing can be used to monitor and control IoT devices in real time. This can be used for applications such as predictive maintenance, traffic management, and industrial automation.
- Video analytics: Edge computing can be used to perform video analytics on IoT devices, such as security cameras and traffic cameras. This can be used for applications like object detection, motion detection, and facial recognition.
- Machine learning: Edge computing can be used to train and deploy machine learning models on IoT devices. This allows for real-time predictions and decisions to be made at the edge, without the need to send data to the cloud.
Here are some examples of edge computing for IoT services in use today.
- Smart cities: Edge computing is being used to power smart city applications such as real-time traffic monitoring, parking management, and air quality monitoring.
- Industrial automation: Edge computing is being used to improve the efficiency and reliability of industrial automation processes. For example, edge computing can be used to monitor and control machines in real time, and to perform predictive maintenance to prevent downtime.
- Retail: Edge computing is being used to improve the customer experience in retail stores. For example, it can be used to power personalised recommendations, in-store navigation, and queue management systems.
Overall, edge computing is a powerful technology that can be used to improve the performance, reliability, and security of IoT services.
Threats in IoT enabled architecture
As per the Singapore Computer Society (SCS) Cyber Literacy Report 2020 and Blackberry Threat Report 2022, IoT attacks remain one of the top 5 cyber threats around the world. IoT plays a vital role in today’s connected world, spanning applications from smartwatches and IP cameras in traffic and road safety control, to CCTVs for smart city administration, PoS monitoring in retail stores, and inventory supply chain in manufacturing sector.
IoT architecture is based on three major components.
- Edge client – Collects data from connected devices and sends it to the gateway
- Gateway – Validates and forwards data to the cloud platform for storage and processing
- Cloud – Receives and processes data blocks from the gateway, stores them in cloud storage, and transfers for processing like analytics and reporting services hosted on the cloud native platform
Security design is vital in IoT architecture design strategy. We need to see this at four levels:
- Infrastructure security to manage security at the physical device level from device controllers, edge, gateway and cloud.
- Platform security to manage security at runtime services in edge and gateway in order to handle access control and protect data privacy requirements.
- Network security to manage, monitor and adopt data encryption during network transfers — two-way handshake to ensure secured clients are connected, and audit security logs for anomaly behaviour, if any.
- Application security to manage native and third party services handling data and to ensure that IoT services like API are protected from cyberattacks.
Potential challenges in IoT security could be data privacy compromised when using third party services, unprotected data storage, lack of role-based access control (RBAC), weak cloud architecture to protect public exposed services, and insecure or outdated IoT device components being exposed to cyberattacks.
Future developments in IoT enabled services
Here are some potential future developments in IoT-enabled services.
- Ubiquitous connectivity: 5G and beyond will enable massive scale IoT deployment. Connectivity will be faster, cheaper, and more reliable.
- AI at the edge: More advanced edge devices will allow localised AI inferencing, reducing latency and data transfer.
- Increased adoption in industries: Manufacturing, healthcare, smart cities and more will see expanded IoT adoption for monitoring, automation, etc.
- Advanced analytics: With more data, analytics and predictive modelling will become more sophisticated and accurate.
- Growth of as-a-Service models: Device management, connectivity, security, etc, will increasingly be offered ‘as a service’.
- New voice/gesture interfaces: There will be more natural interfaces based on voice assistants, computer vision, and AR/VR.
- Increased focus on security: Security architectures spanning edge, network, and cloud will be crucial.
- Distributed computing: Swarms of collaborative edge devices for distributed computing paradigms will be leveraged.
- Personalised IoT: Tailored solutions using wearables, smart home tech, and personalised healthcare will be popular.
- Sustainability: Greener devices, renewable energy, and optimised energy usage will be in focus.
- Smart cities: Urban IoT rollouts will improve traffic, public services, and more.
- Better hardware: Smaller, cheaper, more efficient IoT sensors and edge hardware are on the cards.
- Closed loop automation: Systems that translate IoT data into automated intelligent actions to improve business processes will be in common use.
The future of IoT promises a brighter, more efficient, and interconnected world, but it will require overcoming scale, complexity, privacy and security challenges.