Tag: Penetration testing
What is Penetration Testing and Why is it Important?
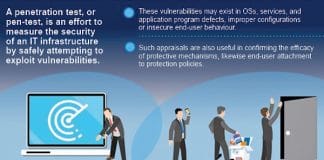
Penetration testing, also known as pen testing or security testing, is a form of ethical hacking. It’s an authorised cyber attack on any computer...
Kali Linux: Use this Popular Linux Distribution for Penetration Testing
This article explores penetration testing in conjunction with Kali Linux, the Debian-derived distro of the Linux operating system.
Penetration testing, also known as pen testing,...
The Best Open Source Automated Penetration Testing Tools
Nowadays, there is considerable amount of confusion among industry professionals and researchers regarding the significant differences between vulnerability scanning and penetration testing, as the...
Basics Of Vulnerability Assessment And Penetration testing
In these days of widespread Internet usage, security is of prime importance. The almost universal use of mobile and Web applications makes systems vulnerable...
Secure Your Career with ‘Ethical Hacking’!
In the dark alleys of virtual space, cyber crooks, a.k.a. hackers, are persistently coming up with novel attacks to knock out even the latest...
IPsec VPN Penetration Testing with BackTrack Tools
This article outlines the value of penetration-testing VPN gateways for known vulnerabilities and also shows you how to prevent a breach into the internal...
Web Application Penetration Testing Using Samurai
This article introduces you to penetration-testing of Web applications. Also included is some hands-on work with a Web-testing framework called Samurai.
Penetration testing, affectionately called...
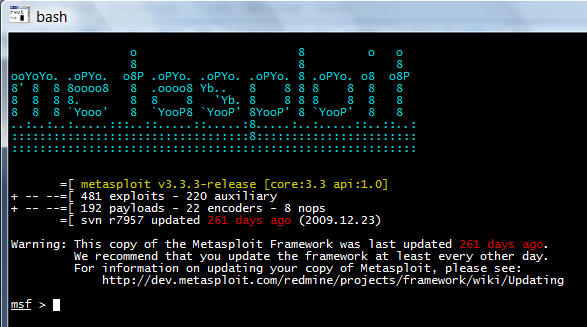
Metasploit: The Exploit Framework for Penetration Testers
Today, the Metasploit Framework is considered the single most useful auditing tool that is freely available to security professionals and penetration testers. It has...