Tag: Security
Iptables: The Flexible Firewall Utility for Linux
This article covers the basics of Iptables and will add to your understanding of this firewall utility. After going through it, you can try...
OPNsense: Setting up basic Firewall
Security concerns prompt the securing of networks against hacking and intrusion. OPNsense is an open source, FreeBSD based firewall and routing platform. It includes...
Open Source Adoption by Indian Government
The Indian Government must adopt open source but must ensure that a firm support system is in place before its adoption.
The government’s decision to...
Secure a Linux Box through the Right File Permissions
This article discusses how a Linux machine can be controlled by assigning permissions for accessing files and directories to owner users, group members and...
The Internet of things (IoT)
The IoT is a technology in the making and we can experience it in small ways, even now. The author presents an appetite whetting...
A Primer on Evil Twin Wireless Attacks
In a scenario where we are using freely available public wireless networks all the time, security considerations are vital. Wireless attacks can be launched...
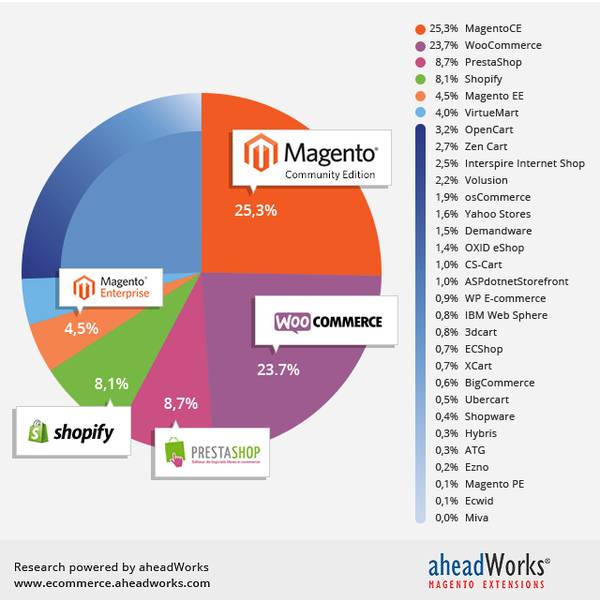
Ecommerce Store on Magento Platform Needs Security and Protection
Magento, an eBay product was earlier known as Varien. It is one of the most preferred eCommerce platforms and is being used by almost...
The Most Popular Security Assessment and Server Hardening Tools
Enterprises require high levels of security for their computer systems. A server attack or a malware intrusion can cause incalculable damage. Prudence, therefore, is...
A Peek into the Top Password Managers
We use passwords to ensure security and the confidentiality of our data. One of the biggest modern day crimes is identity theft, which is...
An Introduction to Bitcoin: The Open Source Cryptographic Currency
Bitcoin is the new 'virtual currency' that has aroused the interest of millions of people, financial and banking institutions, and government agencies. As it...